Valence’s latest report, The State of SaaS Security: Trends and Insights for 2025–2026, developed in partnership with the Cloud Security Alliance, uncovers a troubling disconnect: Despite increased investment and attention, organizations are still struggling with fundamental SaaS security challenges—including limited risk visibility, rampant shadow SaaS adoption, identity risks (both human and non-human), and uncontrolled data exposure.
Let's dive into the key findings from the latest research report to better understand the underlying causes of this challenge.
Investment vs. Reality
The report shows that SaaS security has become a top priority for 86% of organizations, with 76% increasing their budgets this year. This significant investment reflects the growing recognition of SaaS environments as critical business and data infrastructure, requiring robust protection.
However, this increased focus has yet to deliver consistent outcomes. Despite committing more resources, organizations continue to struggle with widespread data oversharing (63%) and poor access control (56%).
You Can’t Protect What You Can’t See
Perhaps most concerning is what we'd call a "confidence paradox". While 79% of organizations express confidence in their SaaS security programs, this confidence exists alongside significant SaaS security capability gaps:
- 55% of respondents admit employees adopt SaaS tools without security's involvement (shadow SaaS)
- 57% report fragmented SaaS security administration
- 42% of organizations say they lack comprehensive SaaS discovery capabilities and are unable to detect if employees are using risky GenAI applications such as DeepSeek
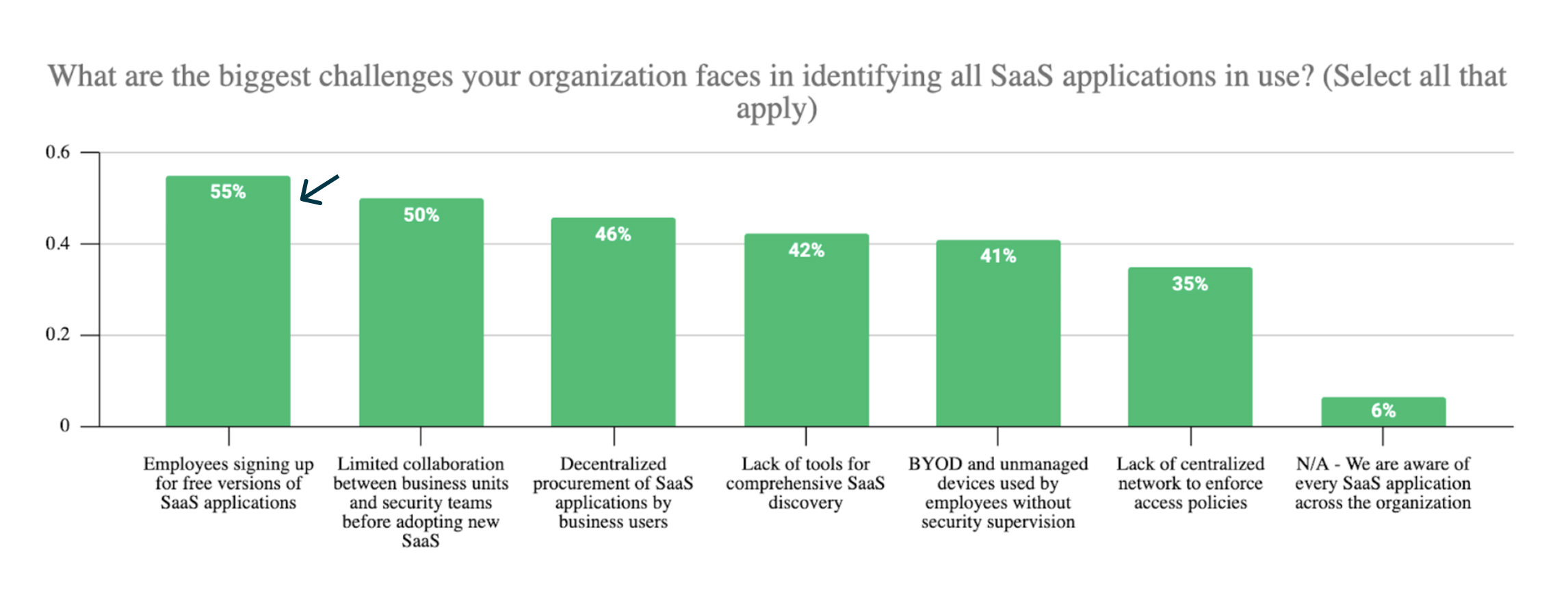
These statistics suggest that many security teams who expressed confidence in their SaaS security programs may have a false sense of control, all while lacking visibility into the full extent of their SaaS attack surface.
Human Identity Security Remains a Challenge
Securing SaaS identities and ensuring proper identity hygiene—particularly around privilege management and identity lifecycle processes—has never been more important. The latest Verizon Data Breach Investigation’s Report (DBIR) (2025), shows that credential compromise remains the leading threat vector responsible for the majority of breaches, while phishing and social engineering remain significant threats to organizations.
Our report supports these findings, indicating that organizations are still struggling with foundational identity and access management (IAM) across their SaaS estate.
- 58% of respondents struggle to enforce proper privilege management
- 56% have difficulty managing users across multiple applications
- 51% lack the ability to properly offboard dormant identities and accounts
Notably, nearly half of organizations are still unable to enforce consistent multi-factor authentication (MFA) and single sign-on (SSO) across all users and applications—a critical gap, as evidenced by the Snowflake breach.
These IAM shortcomings directly contribute to SaaS security incidents and complicate incident response. Without strong identity controls, organizations are more vulnerable to lateral movement and face significant challenges enforcing least privilege access.
Supply Chain Risk: Non-Human Identities
The SaaS landscape grows more complex with each passing quarter. SaaS-to-SaaS integrations and GenAI tools are expanding the attack surface, leaving 46% of organizations struggling to monitor non-human identities, and 56% concerned with over-privileged API access.
This highlights a critical evolution in SaaS security: It’s no longer just about human users. SaaS-to-SaaS integrations, APIs, and OAuth tokens have emerged as high-risk vectors that many security programs aren't equipped to address. Verizon’s (2025) DBIR underscores this, noting that third-party involvement in breaches doubled year-over-year to 30%—highlighting the growing risk from SaaS vendors, supply chains, and partner ecosystems.
Security Patchwork is Creating Gaps
It’s clear that today’s patchwork of SaaS security controls is no longer sufficient to protect modern enterprises. The patchwork approach is evident in the data:
- 69% of organizations rely on native security capabilities that exist within their SaaS applications
- 48% rely solely on the access management controls provided by their identity provider (IdP)
- 43% rely on CASBs
- 46% still conduct manual SaaS audits
These approaches are fundamentally incapable of addressing the breadth and complexity of today’s SaaS security challenges comprehensively. According to our report, the top areas where organizations struggle most include monitoring non-human identities (such as OAuth tokens, API keys, and service accounts), managing highly distributed SaaS environments, and driving the cross-functional collaboration required between security and business teams to effectively remediate risks.
Ultimately, a patchwork approach to SaaS security leads to limited risk visibility, inconsistent policy enforcement, operational inefficiencies, and escalating risk—issues that will only intensify as SaaS adoption continues to accelerate.
Bridging the Gap
The 2025 Valence report makes one thing clear: Security leaders must shift their thinking. Addressing SaaS security requires a comprehensive, purpose-built approach. Organizations must adopt a leading-edge SaaS security platform that covers these critical areas:
- Complete SaaS discovery across both sanctioned and unsanctioned applications
- Identity security management for both human and non-human identities, including SaaS-to-SaaS integrations
- Identity Threat Detection and Response (ITDR) to quickly flag and respond to suspicious and malicious activity
- SaaS data protection to reduce unauthorized data exposure
- Advanced remediation options tailored to the scale and complexity of SaaS environments
The imperative now is to build cohesive programs that cover the full spectrum of SaaS risks—from human access to non-human identities, from shadow SaaS to core business applications, and from ungoverned data to automated workflows that help security teams drive down risk efficiently.
What steps is your organization taking to close these gaps?
See how Valence helped Highspot reduce their SaaS attack surface risk by 38%—on day one.



.jpg)








