Valence’s Latest Research on the 2025-2026 State of SaaS Security: Overconfidence Despite Critical Gaps

Valence’s latest report, The State of SaaS Security: Trends and Insights for 2025–2026, developed in partnership with the Cloud Security Alliance, uncovers a troubling disconnect: Despite increased investment and attention, organizations are still struggling with fundamental SaaS security challenges—including limited risk visibility, rampant shadow SaaS adoption, identity risks (both human and non-human), and uncontrolled data exposure.
Let's dive into the key findings from the latest research report to better understand the underlying causes of this challenge.
Investment vs. Reality
The report shows that SaaS security has become a top priority for 86% of organizations, with 76% increasing their budgets this year. This significant investment reflects the growing recognition of SaaS environments as critical business and data infrastructure, requiring robust protection.
However, this increased focus has yet to deliver consistent outcomes. Despite committing more resources, organizations continue to struggle with widespread data oversharing (63%) and poor access control (56%).
You Can’t Protect What You Can’t See
Perhaps most concerning is what we'd call a "confidence paradox". While 79% of organizations express confidence in their SaaS security programs, this confidence exists alongside significant SaaS security capability gaps:
- 55% of respondents admit employees adopt SaaS tools without security's involvement (shadow SaaS)
- 57% report fragmented SaaS security administration
- 42% of organizations say they lack comprehensive SaaS discovery capabilities and are unable to detect if employees are using risky GenAI applications such as DeepSeek
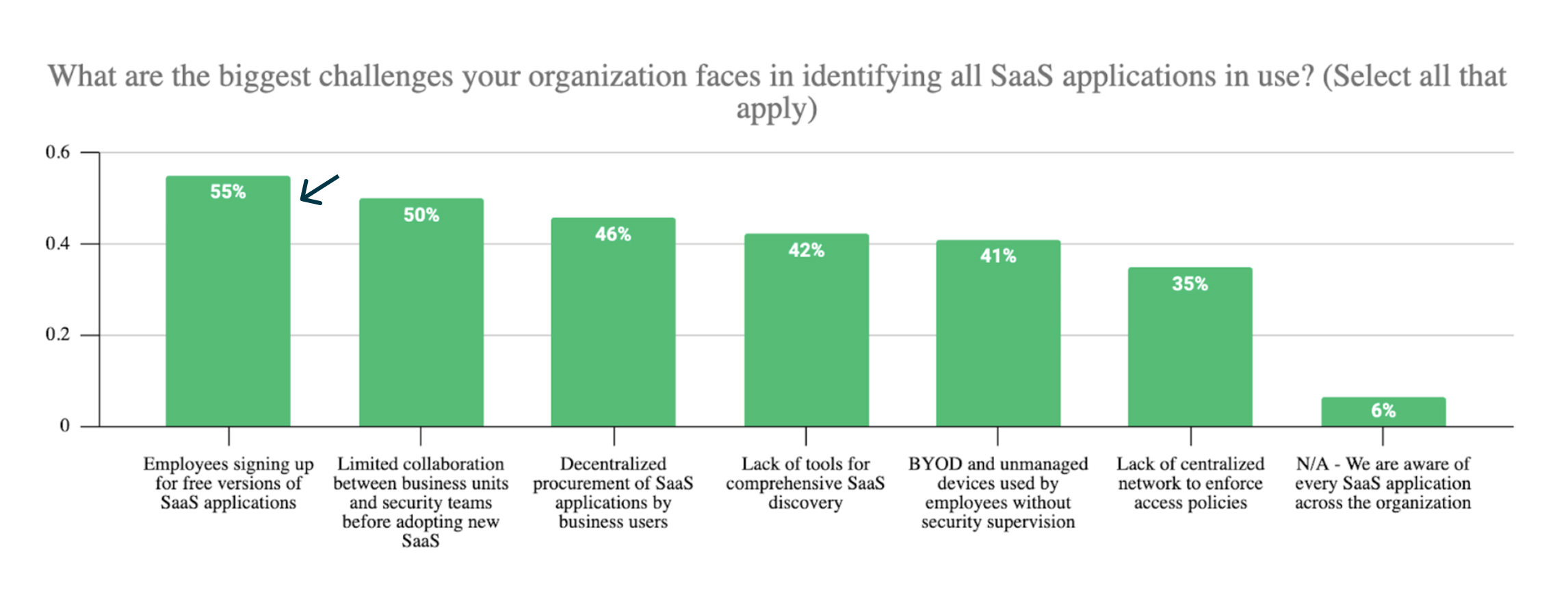
These statistics suggest that many security teams who expressed confidence in their SaaS security programs may have a false sense of control, all while lacking visibility into the full extent of their SaaS attack surface.
Human Identity Security Remains a Challenge
Securing SaaS identities and ensuring proper identity hygiene—particularly around privilege management and identity lifecycle processes—has never been more important. The latest Verizon Data Breach Investigation’s Report (DBIR) (2025), shows that credential compromise remains the leading threat vector responsible for the majority of breaches, while phishing and social engineering remain significant threats to organizations.
Our report supports these findings, indicating that organizations are still struggling with foundational identity and access management (IAM) across their SaaS estate.
- 58% of respondents struggle to enforce proper privilege management
- 56% have difficulty managing users across multiple applications
- 51% lack the ability to properly offboard dormant identities and accounts
Notably, nearly half of organizations are still unable to enforce consistent multi-factor authentication (MFA) and single sign-on (SSO) across all users and applications—a critical gap, as evidenced by the Snowflake breach.
These IAM shortcomings directly contribute to SaaS security incidents and complicate incident response. Without strong identity controls, organizations are more vulnerable to lateral movement and face significant challenges enforcing least privilege access.
Supply Chain Risk: Non-Human Identities
The SaaS landscape grows more complex with each passing quarter. SaaS-to-SaaS integrations and GenAI tools are expanding the attack surface, leaving 46% of organizations struggling to monitor non-human identities, and 56% concerned with over-privileged API access.
This highlights a critical evolution in SaaS security: It’s no longer just about human users. SaaS-to-SaaS integrations, APIs, and OAuth tokens have emerged as high-risk vectors that many security programs aren't equipped to address. Verizon’s (2025) DBIR underscores this, noting that third-party involvement in breaches doubled year-over-year to 30%—highlighting the growing risk from SaaS vendors, supply chains, and partner ecosystems.
Security Patchwork is Creating Gaps
It’s clear that today’s patchwork of SaaS security controls is no longer sufficient to protect modern enterprises. The patchwork approach is evident in the data:
- 69% of organizations rely on native security capabilities that exist within their SaaS applications
- 48% rely solely on the access management controls provided by their identity provider (IdP)
- 43% rely on CASBs
- 46% still conduct manual SaaS audits
These approaches are fundamentally incapable of addressing the breadth and complexity of today’s SaaS security challenges comprehensively. According to our report, the top areas where organizations struggle most include monitoring non-human identities (such as OAuth tokens, API keys, and service accounts), managing highly distributed SaaS environments, and driving the cross-functional collaboration required between security and business teams to effectively remediate risks.
Ultimately, a patchwork approach to SaaS security leads to limited risk visibility, inconsistent policy enforcement, operational inefficiencies, and escalating risk—issues that will only intensify as SaaS adoption continues to accelerate.
Bridging the Gap
The 2025 Valence report makes one thing clear: Security leaders must shift their thinking. Addressing SaaS security requires a comprehensive, purpose-built approach. Organizations must adopt a leading-edge SaaS security platform that covers these critical areas:
- Complete SaaS discovery across both sanctioned and unsanctioned applications
- Identity security management for both human and non-human identities, including SaaS-to-SaaS integrations
- Identity Threat Detection and Response (ITDR) to quickly flag and respond to suspicious and malicious activity
- SaaS data protection to reduce unauthorized data exposure
- Advanced remediation options tailored to the scale and complexity of SaaS environments
The imperative now is to build cohesive programs that cover the full spectrum of SaaS risks—from human access to non-human identities, from shadow SaaS to core business applications, and from ungoverned data to automated workflows that help security teams drive down risk efficiently.
What steps is your organization taking to close these gaps?
See how Valence helped Highspot reduce their SaaS attack surface risk by 38%—on day one.
SaaS Vendor Security Takes Center Stage

JPMorganChase's (JPMC) Global CISO Patrick Opet recently issued a stark warning in an open letter to SaaS vendors: intense market competition has prioritized rapid feature development over security, creating vulnerabilities that threaten individual organizations and the global economic system.
Let’s dive deeper into the systemic risks Opet highlighted in this extraordinary open letter.
System Risks Exposed
Organizations must rely on a limited pool of SaaS vendors, creating concentrated security risks in critical infrastructure. Opet notes: "Today, an attack on one major SaaS or PaaS provider can immediately ripple through its customers."
Security vs. Speed
Opet notes, vendors must prioritize foundational security over rushed feature releases, as JPMC has experienced multiple incidents in the past few years requiring swift isolation of compromised providers and substantial resources for threat mitigation.
Modern Architecture Vulnerabilities
Modern identity protocols like OAuth create significant security blindspots. For example, AI-driven calendar optimization with "read-only" access to corporate email represents a high-value target if compromised—demonstrated by the Microsoft Midnight Blizzard attack, where attackers exploited a legacy OAuth application to access sensitive corporate data.
SaaS: The New Battleground
Despite increased organizational investment in SaaS security, The State of SaaS Security: Trends and Insights for 2025-26 report shows that misconfigured settings remain the leading cause of breaches. These misconfigured settings can manifest in the form of over-privileged accounts, or, failing to enforce authentication controls such as multi-factor authentication (MFA) and single sign-on (SSO). The consequences of not enforcing foundational controls such as MFA can be dire, as demonstrated in the Snowflake breach that impacted 165 organizations, including AT&T, Santander and Ticketmaster. Part of the challenge stems from vendors shipping insecure defaults and customer unfamiliarity with proper security configurations. This is why CISA advocates for "secure-by-default" SaaS, including mandatory MFA for privileged accounts, eliminating default passwords, and enabling SSO and secure logging without additional charges.

Shared Responsibility
Many organizations however fail to understand their responsibility for securing identities and data within SaaS applications. These gaps often remain unidentified until breaches occur. Vendors must also clearly define security boundaries, while customers must demand transparency about security control responsibilities.

Action Plan for Your Business
It's vital that you:
- Review security defaults across all SaaS providers and audit visibility based on your subscription tier
- Map your entire SaaS ecosystem, including unsanctioned applications
- Strengthen credential security through enforcing good password hygiene, MFA and SSO, to counter the breaches caused by stolen credentials and weak authentication
- Regularly audit and revoke unused OAuth token tokens to minimize the SaaS-to-SaaS attack surface
- Prioritize rapid threat detection and response as attack timelines shorten to mitigate the impact of a breach
The Path Forward
Organizations that will thrive are those that:
- Demand stronger security by default from SaaS vendors
- Implement rigorous third-party risk management
- Build defense-in-depth strategies assuming compromise will occur
- Invest in comprehensive SaaS ecosystem risk visibility and remediation capabilities
- Deploy real-time SaaS threat detection to detect compromise as it happens
As Opet warns, addressing these risks is essential to prevent "an unsustainable situation for the economic system."
The stakes are clear: either collectively raise SaaS security standards or face increasingly severe consequences.
The time to act is now.
See how Valence secures the entire SaaS ecosystem. Click here for a demo.
Why Your SaaS Security Strategy Needs Automated Remediation

Your security team is operating with a dangerous blind spot. Your SaaS environment is likely the most vulnerable aspect of your security posture due to unremediated and escalating cyber risk. Even if you're using a first generation SaaS Security Posture Management (SSPM) solution, the uncomfortable truth is that you have a significant degree of unremediated risk.
This is because manual remediation simply cannot scale with your expanding SaaS ecosystem. The average enterprise now uses in excess of 100 SaaS applications on the low-end, with thousands of SaaS-to-SaaS integrations and millions of external data shares constantly occurring and accumulating.
Read on to understand why automated remediation workflows are non-negotiable for a successful SaaS security strategy.
SaaS Beyond Security’s Control
One challenge of identifying risks is that most SaaS apps exist outside of the security team’s direct control. Unlike on-premise systems, that were typically administered by IT, IT/security teams cannot simply login and change settings or implement controls.
This decentralized landscape is today’s reality: Marketing owns Hubspot, Finance manages NetSuite, HR runs Workday, and Sales drives Salesforce—each SaaS application has its own administrators and security configurations.
When security teams identify a risk—like thousands of files being shared externally, they face the manually impossible task of remediating it. The same goes for SaaS-to-SaaS integrations—these non-human identities grow each day, are long-lived, and are often over-privileged.
Enter Automated Remediation Workflows
First-generation SSPMs deliver excellent risk visibility but leave security teams without the tools to operationalize response. It's common to hear that these tools do a great job of "lighting up all our SaaS risk,” for example, showing thousands of instances of sensitive data shared externally. The same applies to SaaS integrations sprawl.
But now what? How do you realistically remediate these risks with manual processes, and stay on top of them consistently?
Valence solves this gap, enabling scalable remediation workflows for known risks across SaaS data, access, and integrations.
- One-click remediation: Manually fix data exposure risk directly from the console, with full context
- Business-user collaboration: Engage with app owners via Slack or email to review, validate, and get additional context about SaaS risks before remediating them
- Automated remediation: Configure automated workflows with a no-code interface that allows you to define the desired triggers, outreach and actions required to enforce your security policy
The impact extends beyond efficiency. With automated remediation workflows, security teams can reduce data exposure and integration risk instead of simply documenting unaddressed issues.
Real World Success Stories
As a CISO, your skepticism about automation is well-founded. Legacy security automation tools often created more problems than they solved. However, modern SaaS security platforms like Valence have redefined the approach. The key is to focus on “automation” and not “automatic” remediation—this means a focus on automating manual tasks that are well-defined. If needed, our business user collaboration can keep a human-in-the-loop, but the human is the actual business user who has the context. This keeps the process collaborative without increasing your security team’s workload.
The concern that "automation will break things" is contradicted by Highspot’s experience, where thousands of external data remediations occurred without a single business disruption—reducing unnecessary external file shares from Google Workspace by 55%.
The worry that "our environment is too complex" actually underscores why automated remediation is necessary—human analysts cannot manage the complexity of external data exposure or third party integrations across numerous SaaS apps at scale. And the fear that "our users will resist" was disproven at Lionbridge, where users actively participated in remediation of SaaS integrations when given the right tools and context.
During Lionbridge’s proof of concept with Valence, they uncovered over 1,000 SaaS-to-SaaS integrations across their global operations, most of which were independently adopted without security oversight. According to Doug Graham, Chief Trust Officer at Lionbridge, “the ability to automatically mitigate SaaS security risks is a game changer” that “eliminated manual and labor intensive workflows,” while educating users about risks.
Lionbridge revoked 95% of obsolete or inactive OAuth tokens immediately, with 20% revoked by business users themselves. They’ve since expanded remediation workflows to address external data oversharing, overprivileged and inactive user accounts, and unrestricted email forwarding rules.
Why Manual Remediation Fails
The economics simply don't work. Consider the math: If your team spends just 15 minutes reviewing and remediating each risky integration, and you have 5,000 such issues, that's 1,250 hours of work—more than 31 weeks of full-time work for one analyst. For external data shares, the challenge is even greater. With organizations having thousands, or even millions of shares, manual remediation becomes humanly impossible.
Meanwhile, new SaaS apps, new integrations, and data shares accumulate daily. Ask yourself a question: when was the last time you revoked an integration or unshared a file? The backlog grows faster than you can address it. This isn't a reflection on your team's capabilities—it's a fundamental SaaS scalability problem that no amount of hiring can solve.
From Manual to Automated
While concerns exist over security automation gone wrong, Highspot eliminated 38% of their external Google Workspace data shares on day one—with zero business impact. Within six months, they reduced their risk surface by 55% while freeing their security team for strategic initiatives. Lionbridge’s complex operation across 23 countries benefitted similarly. Automated remediation workflows transformed SaaS security into a collaborative process, engaging users without disrupting them.
Security as Competitive Advantage
In today's digital economy, security can no longer be a cost center or compliance function. Forward-thinking organizations like Highspot and Lionbridge have transformed SaaS security into a competitive advantage—enabling SaaS-first business agility while reducing risk.
The question isn't whether you can afford to adopt automated remediation workflows. Given the scale and sprawl of modern SaaS environments—and the risk posed by unmanaged data sharing and third-party integrations—can you afford not to?
Your manual processes aren't just inefficient—they're increasingly ineffective against the growing complexity of your SaaS ecosystem. Automated remediation workflows aren’t just the future of SaaS security—they’re the only viable path forward.
Find and fix SaaS risks. See how Valence transforms SaaS risk remediation.
Taming the Wild West of SaaS Data Sharing

SaaS applications have become the backbone of productivity and collaboration, but the convenience of cloud-based tools brings significant security challenges that often fly under the radar. As security leaders, it’s crucial to understand the risks of data sharing in SaaS to protect your organization’s most valuable assets.
Data from our recent survey shows that 58% of organizations experienced at least one SaaS-related security incident in the past year. This same report found that 94% of external data shares in SaaS applications were inactive, and also that 46% were shared to personal email accounts, exposing organizations to serious, unmanaged risk.
To reduce the frequency of SaaS security incidents, we must first bring order to the wild west of SaaS data sharing.
Let’s examine the critical data sharing concerns in SaaS every organization should address.
SaaS Data Sharing is Much More Expansive Than You Think
SaaS applications host vast amounts of critical data. Most of the attention is usually focussed on collaboration platforms like OneDrive, Sharepoint 365, or Google Drive. While these platforms account for a significant amount of typical data shares, almost every app, for example Salesforce, Slack, GitHub and Workday, has data sharing capabilities that is out of the security team’s purview.
The challenge in governing data sharing for these apps is compounded by the decentralized ownership of these apps, usually sitting in respective business units, as well as the diverse range of data sharing methods available, including internal features, external links, email, and APIs.
The types of data shared by these apps includes a range of sensitive information including personally identifiable information (PII) such as employee records, customer records, financial data, internal communication, intellectual property, including source code and blueprints to name a few.
You Can't Protect What You Can't See
For many security leaders, the most alarming aspect of SaaS data sharing is the profound lack of visibility. Traditional security tools were not designed for cloud-based, collaborative environments, leaving security teams in the dark about:
- Who has access to what data
- When and how often data is being accessed
- Where sensitive information is being shared
- What data is being downloaded or exported
This visibility gap makes it nearly impossible to detect anomalous behavior that might indicate a breach or data theft.
Long-lived Sharing
One of the most insidious risks in SaaS environments is long-lived sharing permissions. When employees set up sharing links or grant access to files and folders, these permissions rarely include an expiration date. This means that months or even years after the collaboration has ended, external parties may still have access to sensitive information. As organizational data grows exponentially, tracking these persistent access points becomes increasingly difficult, creating an expanding attack surface.
We routinely find millions of shared files with upwards of 90% of these data shares and access dormant. Conducting regular permission and sharing audits are essential practices to mitigate this risk. Security leaders should advocate for SaaS solutions that support automatic revocation of shared access based on organizational specific data security policies.
Conducting regular permission and sharing audits are essential practices to mitigate this risk. Security leaders should advocate for SaaS solutions that support automatic revocation of shared access based on organizational specific data security policies.
Open Link Sharing
Perhaps the most concerning feature of modern SaaS applications is the ability to create shareable links that grant access to anyone possessing the URL. While convenient, these links dramatically expand the potential attack surface.
Consider what happens when an employee creates an "anyone with the link can view" sharing option for a document containing customer data or intellectual property. That link might be:
- Forwarded in emails to unintended recipients
- Posted in public forums accidentally
- Discovered through web crawlers if included on public pages
- Found in browser history on shared or compromised devices
This exact scenario played itself out with the Japanese game developer Ateam, who as a result of a Google Drive sharing misconfiguration, exposed personal information of nearly 1 million people for over six years.

The lack of authentication requirements means these links could expose sensitive information to unauthorized parties, without leaving any audit trail of who accessed the data.
Sharing With Personal Email Accounts
Convenience often drives employees to share corporate data with personal email addresses – either their own for "work from home" scenarios or colleagues' personal accounts to circumvent access limitations.
This practice dramatically increases risk in several ways:
- Personal accounts lack enterprise-grade security controls
- Security teams have no visibility into or control over personal accounts
- Data shared to personal accounts remains accessible after employees leave an organization
Implementing strict data loss prevention (DLP) policies that prevent sharing to personal domains, combined with employee education about the risks, can help address this risk.
The Non-Human Identities Ecosystem
The interconnected nature of modern SaaS environments creates significant security challenges. A typical organization manages thousands of non-human identities–connections between SaaS applications utilizing OAuth tokens, API keys, or service accounts. These digital identities represent vulnerable entry points, especially due to the fact that security controls or authentication mechanisms are absent. The risk is heightened by the fact that these identities are granted with one-time, long lived authorization consents that rarely undergo review. Third-party access compounds this risk.
Vendors, partners, and contractors often receive access to critical systems without adequate vetting or restrictions. The Cyberhaven (2024) and Midnight Blizzard (2024) attacks demonstrated how dramatically supply chain vulnerabilities can impact organizations, with compromised SaaS vendors serving as potential entry points to thousands of customer environments.
Customers are often alarmed to find hundreds and thousands of third party integrations active with access to sensitive data, yet these connections have been dormant for months or even years. That is why it is essential for organizations to implement comprehensive vendor assessment protocols, limit third-party access to the minimum necessary, continuously monitor for suspicious sharing activity, and revoke unused integrations routinely, ideally on an automated, time-bound basis.
Consequences of Data Exposure
The combination of easy sharing, poor visibility, and persistent access creates the perfect conditions for sensitive data leakage. Whether through malicious intent or simple human error, the exposure of confidential information can have devastating consequences:
- Regulatory compliance violations and potential fines
- Intellectual property theft affecting competitive advantage
- Customer data breaches damaging trust and reputation
- Financial loss from remediation costs and potential litigation
Final Word
As SaaS adoption continues to accelerate, the security challenges associated with data sharing will only grow more complex. The combination of easy sharing, poor visibility, and persistent access creates the perfect conditions for sensitive data leakage. Whether through malicious intent or simple human error, the exposure of confidential information can have devastating consequences.
To effectively address these risks, security leaders must adopt a multi-faceted approach underpinned by SaaS security tooling that enables:
- Regular user access reviews and permission right-sizing
- The development and enforcement of clear data sharing policies with regular compliance reviews
- The ability to detect and revoke open link file sharing or sharing to personal email accounts
- Visibility and revocation capabilities over the third-party integrations ecosystem
- The capability to detect and respond to suspicious data sharing activities
Security leaders who address these risks now will be better equipped to protect their organizations while still preserving the collaboration benefits that make SaaS applications so valuable. The future of SaaS security lies in striking the right balance between empowering users with powerful collaboration tools and implementing the guardrails needed to keep sensitive data secure.
Find and fix SaaS risks. See how Valence brings order to SaaS data sharing.
The Rising Threat of Consent Phishing: How OAuth Abuse Bypasses MFA

A sophisticated attack vector known as “consent phishing” has emerged as a significant SaaS security threat. Unlike traditional phishing that targets credentials directly, consent phishing exploits legitimate authorization protocols that use OAuth 2.0 to gain persistent access to corporate SaaS resources.
Late last year it was disclosed that Google Chrome extension vendors were targeted in a consent phishing attack with 2.6 million end users impacted. This attack targeted at least 35 commonly used Chrome browser extensions including the cybersecurity firm Cyberhaven. Cyberhaven disclosed that an employee’s account was compromised in an earlier attack, which enabled threat actors to gain access to the Google Chrome Webstore. Attackers deployed consent phishing tactics, tricking users into granting permissions to a malicious OAuth application disguised as a legitimate "Privacy Policy Extension", allowing them to publish malicious versions of Chrome extensions. Other notable campaigns this year include attacks involving 12,000 GitHub repositories and Microsoft.
Consent phishing typically involves sending a socially engineered email to a victim’s mailbox. Microsoft email in particular seems to be highly targeted. Victims are lured with compelling and urgent messaging such as security alerts in GitHub. Once the victim approves the permissions request, the threat actor harvests the OAuth token, gaining full access to the resources via API, rendering multifactor authentication (MFA) useless.
Read further to understand this insidious threat and how best to safeguard against it.
How Consent Phishing Works
Here is a step-by-step sequence of such an attack:

1. Launch Phishing Campaign: A spear phishing campaign, usually using email, targets specific users, with a call to action that uses urgent messaging such as: “See security alert,” “Click here to view message,” “Upgrade account security,” etc.
2. Consent Request: After clicking the link, the user is redirected to a legitimate consent page, for example from Microsoft 365 or Google Workspace. Here, the permissions requested are detailed, usually giving the threat actor read and write permissions over emails, contacts, and files.

3. Authorization: The unsuspecting user reviews and accepts the requested permissions, believing the request is legitimate. Upon consent, the threat actors then receive an authorization code from the SaaS application, enabling them to create a new OAuth session token, which grants them access to the victim’s environment.
4. Access Token Acquisition: The OAuth token then allows API calls that interact with user data based on granted permissions, often with read and write, and with potential access to sensitive information—enabling them to manipulate APIs, exfiltrate data, or maintain persistent access.
Why MFA Fails Against OAuth Consent Phishing
While organizations might think they have adequate security controls in place protecting access to their critical SaaS applications, most commonly using MFA, with consent phishing these controls prove to be useless. Since the attackers leverage non-human identities that leverage OAuth 2.0 API-based access, MFA protections are rendered ineffective against the subsequent abuse of granted permissions.
Adding to the security challenge is the common lack of monitoring of 3rd party integration environments. This is often due to a lack of dedicated tooling, but also due to the complexity that these environments can entail.
The Technical Anatomy of OAuth Consent Phishing
The mechanics of consent phishing involve several critical components that are incredibly difficult to detect and that result in devastating breaches, often compromising an organization’s most sensitive data:
1. Unmonitored Non-Human Identities / OAuth Tokens: NHI’s like OAuth tokens and their lifecycle often fly under the radar, particularly from a creation, permissioning and integration monitoring vantage point.
2. Excessive Permission Scope: Threat actors request and succeed in getting highly privileged permission scopes like read and write access for email, contacts, and files.
3. Longer Dwell Times: Unlike compromised credentials that can be changed, OAuth tokens can provide longer dwell times due to their long-lived nature, providing access until explicitly revoked.
Security professionals must understand that standard security controls like conditional access policies typically evaluate risk at authentication time for human users, but fail to assess the security posture of applications requesting delegated permissions.
Final Word
As defenses evolve, so too will attack methodologies. It is likely that consent phishing campaigns are already leveraging AI to create convincing lures for victims. These types of attacks should be taken as a clear signal that the security mandate extends beyond protecting credentials to securing and monitoring the entire authorization layer of SaaS environments, including new 3rd party integrations and permission scopes.
To get a handle on this threat, security professionals should implement controls focused on third party SaaS integrations, which at a minimum should include regular audits and revocations of unauthorized OAuth tokens.
Taming the Beast: The 5 Essential Pillars of SaaS Security

Generative AI represents just one element of the broader SaaS revolution transforming enterprise IT. Most organizations are becoming SaaS-first enterprises, permanently displacing centralized IT architectures. This decentralized environment creates significant challenges for security teams striving to maintain cyber resilience.
Manual security audits cannot keep pace with daily configuration changes, rendering them ineffective. Traditional and first generation SaaS security approaches are merely point-in-time snapshots that fail to capture an organization’s true SaaS attack surface, and rarely help teams reduce risk or improve security posture in a continuous, scalable way. This explains why 58% of organizations suffered a SaaS security incident in the past year, citing key concerns over the ability to manage decentralized SaaS and the risk that this poses.
Read further to understand how to transform your SaaS security posture, shifting it from a reactive and unmanageable challenge to a strategic business enabler.
The Challenge: A Perfect Storm
Several converging factors are creating SaaS security challenges that result in the attack surface expanding daily and out of reach of security teams:
- Decentralized ownership: Your sales team owns the CRM tool, engineering manages their development tools, and HR controls workforce SaaS systems, with security teams often unable to monitor and remediate risks consistently, if at all.
- Visibility: Many tools only focus on sanctioned SaaS, resulting in an incomplete picture of the complete SaaS footprint as it pertains to the extent of shadow SaaS use and risk – with gen AI tools adopted by employees a case in point.
- Identity and privilege sprawl: Dormant employee accounts, guest users with excessive privileges, and hundreds of non-human identities from third-party integrations and service accounts continue to proliferate daily.
A Framework for Transforming Your SaaS Security
1. Discover Your Entire SaaS Ecosystem
Have visibility over all sanctioned and unsanctioned SaaS. Many SaaS security solutions only focus on sanctioned applications, this leaves dangerous blindspots for organizations particularly as it relates to unsanctioned SaaS adopted by employees. The latest wave gaining popular adoption by employees are gen AI tools, with some of these like DeepSeek, which pose significant cyber risk to the enterprise. This specific challenge was identified as a top 3 security challenge and looks to stay top of mind for the foreseeable future.
Discovery must be continuous and comprehensive, not a point-in-time exercise focussed only on sanctioned SaaS, but also include the discovery of unsanctioned SaaS. This continuous and comprehensive visibility is the foundation for reducing risk.ֿ
2. Secure All Human and Non-Human Identities
Secure all SaaS identities. Comprehensively track current employees, former employees, contractors, partners, as well as non-human identities, including service accounts, integrations, and OAuth tokens.
Answer 5 critical questions:
- Who has access to what, including what SaaS is being accessed locally without corporate SSO?
- Which accounts have privileged access?
- Which dormant accounts should be deprovisioned?
- Which integrations connect to sensitive data?
- Can you detect and be alerted when a human or non-human SaaS identity goes rogue?
3. Assess and Strengthen Security Posture
Evaluate security configurations against best practices for each application. This sounds easy, but proves to be a significant challenge across the hundreds of applications used in a typical environment. It is important to establish baseline configurations for each application and continuously monitor for drift.
Organizations should be monitoring for deviations from best practice as it relates to authentication and data security controls. Some of the aspects of authentication that should be monitored include password hygiene, MFA enforcement and identities with excessive privileges. When it comes to data security, you should pay careful attention to drift from data security policies, in particular, detecting any instances of file sharing with open links as well as risky and sensitive file sharing.
4. Remediate Data Exposure Risks Frequently
Target easy attack surface risk reduction wins with auto-remediation. Many existing SaaS security solutions do a great job lighting up all of the risks but do a very poor job of enabling security teams to remediate and reduce the attack surface on an ongoing and sustained basis. Choose a security solution that supports the streamlining of remediation workflows for each application. By identifying and removing unnecessary data access, for example revoking file-sharing from inactive identities, significantly reduces attack surface risk, while improving overall compliance posture.
5. Implement Continuous Threat Detection
Access management for SaaS alone isn't sufficient. Deploy threat detection capabilities for suspicious behaviors such as unusual login locations, impossible travel, mass downloads, or privilege escalation. Connect these detections to your SIEM or SecOps workflows for a coordinated response.
The Path Forward
SaaS security cannot be addressed through fragmented approaches. The volume, velocity, and decentralized nature of sanctioned and un-sanctioned SaaS adoption demands an operational framework supported by a purpose-built SaaS security solution.
When it comes to selecting a security solution, it is important to prioritize capabilities based on the realities of your environment and not on the limitations of what each vendor can provide. Choose a vendor that addresses SaaS risk in its entirety, focussing not only on visibility but also supporting remediation workflows that are loved by security teams. This approach is essential for enabling business agility while also having the necessary security in place.
It's time to find and fix SaaS risks. Click here for a demo.
Mitigating GenAI Risks in SaaS Applications

Artificial Intelligence (AI) tools have revolutionized the business landscape, offering unprecedented automation, efficiency, and innovation. Among these, Generative AI (GenAI) has gained particular traction for its ability to produce creative content, write code, and assist in decision-making. When integrated into SaaS applications, these tools can transform business operations. However, with this rapid adoption comes significant generative AI security risks, especially as organizations struggle to manage and secure these tools effectively.
DeepSeek: A Growing GenAI Risk in SaaS
DeepSeek, a Chinese GenAI platform, has rapidly gained adoption but is facing scrutiny over security and privacy concerns. Several countries have blocked DeepSeek from its app stores—there are widespread concerns across the US and Europe, with regulators in Italy blocking the app from Apple and Google stores amid an investigation into its data collection and storage practices. In France and Ireland, officials are examining potential privacy risks, while in the US, organizations like NASA, the U.S. Congress, and the Navy have already banned its use.
Key Security Concerns:
- Exploding Adoption and Shadow AI Risks: With rapid growth, IT/security teams may lack visibility into DeepSeek usage, raising concerns about sensitive data exposure.
- Privacy Concerns & Data Sovereignty: DeepSeek's privacy policy states that all user data, including chat history and personal information—well beyond what even other GenAI platforms collect—is stored in China, making it subject to Chinese laws and bypassing privacy regulations such as GDPR.
- Security Vulnerabilities & Third-Party Risk: DeepSeek, with limited funding and infrastructure, has already suffered security breaches. The company faced a large-scale cyberattack, believed to be a distributed denial-of-service (DDoS) attack, which led to a suspension of new registrations. Researchers at Wiz also uncovered an exposed DeepSeek database leaking sensitive user data, including chat logs and API secrets.
How Valence Helps Minimize DeepSeek AI Security Risks
SaaS Discovery & Shadow AI Detection: Valence automatically detects DeepSeek and other GenAI tools by analyzing various sources to enable security teams to identify both sanctioned and unsanctioned AI applications across their organizations
Secure Accounts & Permissions: Identify employees using DeepSeek and track OAuth scopes granted to assess potential risks
Proactive Security Partnership: Valence has proactively alerted customers to DeepSeek’s presence in their SaaS environments, reinforcing our role as a trusted security partner, not just a technology tool.Comprehensive Remediation Options: Security teams can take targeted actions to remediate and remove unnecessary SaaS-to-SaaS integrations and limit risky permissions.
Free Risk Assessment: Organizations can assess shadow DeepSeek usage and risky integrations with business-critical SaaS applications.
By leveraging SaaS Discovery, risk remediation, and proactive monitoring, Valence empowers security teams to mitigate the risks associated with emerging GenAI tools like DeepSeek—ensuring compliance, data security, and visibility across their SaaS environment.
The Double-Edged Sword of GenAI in SaaS
The widespread integration of GenAI tools with popular SaaS platforms like Microsoft 365, Google Workspace, and Salesforce presents a complex security challenge. According to the 2024 State of SaaS Security Report, 50% of security leaders have flagged GenAI governance as a critical SaaS security concern. The promise of automation and productivity through GenAI must be balanced against the significant risk these tools introduce.
While platforms like OpenAI’s ChatGPT offer immense utility, they often require extensive access to sensitive data within SaaS environments to function effectively. Without stringent oversight, this opens the door to potential data breaches, privacy violations, and unsanctioned access. That oversight, however, is not always so simple when it comes to SaaS security. One of the key challenges in managing the risks posed by SaaS-to-SaaS integrations, including GenAI tools, is the distributed ownership of SaaS applications across different business units. For instance, Salesforce may be managed by sales operations, outside of the direct control of IT and security teams. This decentralized ownership limits the visibility security teams have over these applications, making it difficult to track, assess, and remediate integration risks effectively.
What Is Shadow AI in SaaS?
Shadow AI refers to the adoption and use of AI tools by employees without formal IT or security approval. This unsanctioned use of GenAI tools within SaaS applications can create blind spots for security teams, leading to unmonitored data access and the risk of exposing sensitive information. With the rapid growth of these tools, especially free trials or low-barrier integrations, the presence of Shadow AI in SaaS environments is on the rise. Security teams must address this growing risk to prevent data leakage and maintain control over the organization’s SaaS security posture.
Top 5 Security Concerns with GenAI in SaaS
- Unsanctioned Use (Shadow AI) - A recent survey by The Conference Board found that 56% of US employees already use GenAI tools at work, often without IT or security oversight, creating visibility and control gaps. Free trials and readily available integrations can entice business users to adopt GenAI tools without proper oversight.
- Wide Access to Data - GenAI tools often require access to a broad range of data within SaaS environments, increasing the risk of exposure. According to the 2024 State of SaaS Security Report, 33% of SaaS integrations are granted sensitive data access or privileges to the core SaaS application. This broad and often unrestricted access raises the potential for data breaches and unauthorized access to sensitive information within platforms like Zoom recordings, instant messaging in Slack, or sales pipeline and customer data in Salesforce.
- Privacy Violations: Many GenAI tools collect user data for training purposes. Organizations could inadvertently expose their data or violate regulations like GDPR or CCPA if they don't carefully scrutinize the privacy policies and data usage terms of GenAI tools. More concerning, GenAI models can inadvertently leak sensitive information during outputs, compromising confidentiality..
- Lack of Transparency: Understanding how GenAI tools operate and make decisions can be challenging. This lack of transparency makes it difficult for security teams to identify and mitigate potential security risks.
- Business User Risks: While leveraging GenAI's potential, business users might overlook security considerations. This can happen during integration with core SaaS applications. Critical security decisions, like the level of data access granted to the GenAI tool or reporting the integration to IT, can be missed during this process, increasing security risks.
Governing GenAI in SaaS: Key Strategies
To address these risks, security teams must take proactive steps:
- Create a GenAI Security Policy: Define clear policies for generative AI security and adoption, including guidelines for data access, tool approval, and employee training.
- Centralized Visibility: Use a SaaS Security Posture Management (SSPM) platform to gain visibility into all GenAI integrations and manage their data access.
- Enforce Least Privilege Access: Apply the principle of least privilege to limit the data that GenAI tools can access.
- User Education: Educate employees on the risks of unsanctioned GenAI tools and best practices for safe integration.
- Continuous Monitoring: Stay updated on emerging GenAI trends and regularly assess the security of your GenAI-integrated SaaS environment.
How Valence Security Helps Manage GenAI Risks in SaaS
As the use of GenAI tools in SaaS applications grows, so too does the need for robust security controls. Valence offers a comprehensive SaaS Security platform for identifying and managing risks associated with both sanctioned and unsanctioned (Shadow AI) GenAI tools. Our platform provides deep visibility into GenAI integrations within your SaaS ecosystem, helping you uncover hidden tools that could expose sensitive data or violate internal policies.
Valence’s SSPM capabilities ensure you have centralized oversight of all SaaS-to-SaaS integrations, including GenAI tools, and enable you to enforce the principle of least privilege by managing access controls. For instance, Valence's detection capabilities can uncover GenAI tools that may have excessive access to emails, calendars, or even customer data. The platform's GenAI mapping filters reveal how these integrations are using sensitive data, allowing security teams to swiftly mitigate risks.
By analyzing factors like data access permissions and the functionalities of the tool, Valence helps prioritize remediation efforts and focus on the integrations posing the highest security risk. In addition, Valence helps security teams to identify recently unused GenAI integrations, which can be a signal that they are no longer active and can (and should) be revoked. For example, the dormant integration may have been set up by a former employee of the organization, but revoking those integrations / OAuth tokens was not part of the employee offboarding process. These overlooked integrations can continue to provide access, posing significant security risks if not properly addressed.
Remember the challenge of distributed ownership of SaaS mentioned earlier? By offering Role-Based Access Control (RBAC) for non-security SaaS administrators and fostering collaboration with business users, Valence ensures that security oversight extends across all business units. With Valence, security teams can gain centralized visibility and control over all SaaS integrations, ensuring that even those managed outside traditional IT boundaries remain secure. This centralized management is particularly critical for identifying and managing the risks posed by unsanctioned or dormant GenAI tools that could otherwise slip through the cracks.
By working closely with SaaS admins and business users, Valence facilitates context-driven risk assessments to ensure GenAI tools are used securely across the organization. Valence provides both guided and automated SaaS risk remediation, including the ability to automatically communicate with business users to clarify if there is a necessary reason for the integrations.
What Is The Future of Generative AI in Cybersecurity?
Of course, discussion of GenAI adoption and governance extends beyond SaaS applications. As Generative AI continues to evolve, so too will its role in cybersecurity. While the automation capabilities of GenAI tools offer promising opportunities for threat detection and response, they also open new attack vectors for cybercriminals. The challenge will lie in balancing innovation with generative AI security measures to ensure these tools are leveraged safely. AI-driven attacks, such as phishing schemes generated by GenAI, could become more sophisticated, making it essential for security teams to stay ahead of emerging threats. Ensuring secure and compliant usage of GenAI tools will be a central focus as we move into the future of cybersecurity.
Uncover Hidden GenAI Risks with Valence
Valence provides unparalleled insights into Shadow AI and SaaS risks related to GenAI tools, empowering security teams to regain control over GenAI tools and protect sensitive data. Our solution identifies risky integrations, helps monitor data access, and ensures that your organization's SaaS security aligns with internal policies and regulatory standards.
Take control of your SaaS environment and protect against the rising tide of Shadow AI and GenAI risks. Schedule a demo today to learn how Valence can help secure your SaaS applications.
Shining a Light on Shadow IT—Announcing Valence's SaaS Discovery Capabilities

As organizations rapidly adopt Software as a Service (SaaS) to drive innovation and productivity, a hidden challenge is growing alongside it: shadow IT. These are unsanctioned SaaS applications brought into the workplace without IT or security team approval, creating significant risks related to sensitive data exposure, compliance gaps, and governance challenges. Shadow generative AI (GenAI) tools further exacerbate these challenges by requiring broad data access and increasing the potential for data misuse.
To combat this, Valence Security is proud to announce the availability of our SaaS discovery capabilities, offering unmatched visibility into sanctioned and unsanctioned SaaS applications. By delivering a comprehensive SaaS inventory, Valence empowers organizations to mitigate shadow IT risks, improve governance, and enhance operational efficiency.
Why Now? Addressing the Long Tail of SaaS
Valence Security has long been a trusted partner for enterprises seeking to protect their most business-critical SaaS applications, including Microsoft 365, Google Workspace, Salesforce, GitHub, Okta, and others. Our SaaS Security Posture Management (SSPM) capabilities enable organizations to identify misconfigurations, manage human and non-human identity risks, and secure the sensitive data housed within these platforms.
But security is never static. In conversations with our customers, we heard a consistent request: help us uncover and govern the long tail of SaaS applications. These lesser-used, secondary or unsanctioned apps, adopted by individual employees or teams, often operate outside of IT oversight. The result? Blind spots that expose organizations to unmanaged identities, data risks, redundant tools, and compliance violations.
In response to customer demand, Valence developed our SaaS discovery capabilities to address this need, ensuring our customers can leverage a continuously updated inventory of all SaaS applications for comprehensive security and governance.
The Risks of Shadow IT and Shadow AI
Shadow IT introduces a wide range of risks that security teams cannot afford to ignore:
- Sensitive Data Exposure - Employees often upload sensitive data to applications that the security team is not monitoring or connect unsanctioned apps to sanctioned ones, potentially exposing sensitive data to unvetted third parties.
- Unmanaged Identities - Apps that are not governed by the corporate identity provider (IdP) or SSO often lack MFA enforcement, leaving local accounts vulnerable to unauthorized access and account takeover.
- Failed Offboarding - An ex-employee or contractor might have adopted a SaaS app while working with the company, with the account persisting long after their departure, posing long-term risks due to blind spots to the organization.
- Generative AI Risks - AI tools, like ChatGPT and MidJourney, are typically adopted as SaaS applications and amplify these risks by ingesting sensitive company data. Research shows between 31% and 38% of AI-using employees admit to entering sensitive work data into those AI tools—including customer details, employee information, and company financials—creating compliance and privacy challenges.
- Compliance Violations - Failure to monitor unsanctioned tools can result in non-compliance with industry regulations such as GDPR or HIPAA, or contradict industry standards like ISO, NIST, SOC2, and others.
These risks not only compromise your security posture but also inflate your attack surface, making effective management of SaaS sprawl essential.
Introducing Valence SaaS Discovery
Valence’s new SaaS discovery capabilities empower organizations to uncover shadow IT, mitigate risks, and maintain governance across the SaaS ecosystem. With Valence’s discovery engine leveraging integrations with IdPs and CASBs, SaaS-to-SaaS integration monitoring, email metadata, and browser logs, customers gain unmatched visibility into both sanctioned and unsanctioned apps—leaving no blind spots in the SaaS ecosystem. By leveraging multiple detection methods, Valence creates a comprehensive, continuously updated SaaS inventory.

Valence combines visibility with actionable insights to secure your SaaS environment holistically:
- Discover Shadow IT: Identify unsanctioned apps that bypass IT approval, exposing your organization to risk
- Monitor Shadow AI: Gain visibility into generative AI tools and reduce risks related to sensitive data ingestion
- Manage SaaS Sprawl: Build a continuously updated SaaS application inventory of all applications, whether sanctioned or not
- Strengthen Identity Security: Detect local accounts and applications outside of your your IdP, enforce MFA/SSO, and support comprehensive SaaS offboarding and lifecycle management
- Simplify Governance: Consolidate redundant tools and eliminate shadow apps to streamline operations and reduce costs
Beyond Discovery: Comprehensive SaaS Security
Valence’s new SaaS discovery capabilities seamlessly expand our holistic SaaS security platform, which also offers:
- SaaS Security Posture Management (SSPM): Valence continuously audits SaaS configurations to identify misconfigurations and detect configuration drift over time. Valence highlights risks such as widely shared files, inactive accounts, excessive admin access, and high-privilege SaaS-to-SaaS integrations. Security teams can align SaaS settings with industry standards like NIST, ISO, and CIS to prioritize action and maintain compliance. By addressing these issues, organizations can enforce security policies, protect sensitive data, and ensure governance across their SaaS applications.
- Risk Remediation: Valence’s unique "Remediation by Choice" approach combines guided steps, ticketing integrations, direct one-click fixes, automated workflows, and business user collaboration, enabling teams to address risks effectively. These extensive remediation capabilities make SaaS risk finding easy to operationalize and reduce the attack surface.
- SaaS Identity Threat Detection and Response (ITDR): Valence provides real-time visibility into human and non-human activities, enabling rapid threat investigation and response. By uncovering hidden risks and suspicious events, organizations can protect sensitive SaaS data and respond swiftly to identity-related threats.
Take Control of Your SaaS Ecosystem
As shadow IT and shadow AI continue to grow, the need for comprehensive SaaS security has never been clearer. Valence’s new SaaS discovery capabilities help organizations uncover hidden applications, mitigate risks, and strengthen their overall security posture.
Ready to see it in action?
Request a Demo today and take the first step toward eliminating blind spots in your SaaS ecosystem.
Strengthening Cloud Security from SaaS to Infrastructure: Valence Joins WIN—Wiz Integration Network

In today’s expanding cloud ecosystem, comprehensive protection demands securing not only infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) environments but also the critical layer of software-as-a-service (SaaS) applications. As a new member of the Wiz Integration Network (WIN), Valence extends its expertise in SaaS Security Posture Management (SSPM) to support Wiz customers in addressing critical SaaS risks.
Valence empowers organizations to secure their Wiz SaaS environment alongside other essential applications, manage misconfigurations, and review user access. With attackers increasingly targeting SaaS—58% of security leaders said they have been impacted by a SaaS breach over the past 18 months—this integration enables Wiz customers to fortify their SaaS environments and ensure stronger security across all cloud assets.
Beyond IaaS and PaaS: Addressing SaaS Risks in Modern Cloud Security
While securing IaaS and PaaS remains critical, today’s security teams face an expanding threat landscape that also includes critical SaaS applications. SaaS applications are treasure troves of sensitive data and privileged access, making them prime targets for attackers. While Cloud Security Posture Management (CSPM) capabilities identify and protect resources within IaaS services like Amazon Web Services (AWS), Microsoft Azure, or Google Cloud, it doesn’t address SaaS-specific challenges. Without dedicated SaaS Security Posture Management (SSPM), these applications can become attractive targets for attackers to gain entry into the cloud environment.
Valence monitors Wiz as a vital SaaS application, helping security teams strengthen identity and access controls and detect potential misconfigurations—just as they are also able to for applications like Salesforce, Slack, and Google Workspace or Microsoft 365.
Why Securing Your SaaS Applications with Valence Matters
Recent high-profile breaches, such as the Snowflake customer attacks and Microsoft's Midnight Blizzard incident, underscore the critical need for robust SaaS security. In the Snowflake breach, attackers exploited a lack of multi-factor authentication (MFA) to gain access to customer data. Similarly, the Microsoft Midnight Blizzard breach originated from an inactive account in a test environment without MFA that remained undetected. These incidents showcase the critical role of securing SaaS environments, not just from the SaaS provider's perspective but also from the customer's. These incidents highlight the importance of not only relying on the SaaS provider’s security but also strengthening the customer’s side of the shared responsibility model.
The Shared Responsibility Model for SaaS security outlines the division of responsibility between the SaaS provider and the customer. While the provider secures its infrastructure, the customer is responsible for managing security configurations, protecting data, and controlling user access within the SaaS application. This is where Valence supports Wiz customers—not only by securing their Wiz tenants, but also by extending protection to environments like Google Workspace, Microsoft 365, Snowflake, Slack, Salesforce, and many others.
The Benefits of a Unified SaaS and Cloud Security Approach
A core security challenge in securing SaaS environments is managing user identity and access. Valence’s platform optimizes identity security in critical Saas applications like Wiz by:
- Detecting Inactive Accounts - Identifying dormant accounts that no longer need access to Wiz’s resources, reducing potential attack surfaces
- Mitigating Overprivileged Access - Ensuring users have only the permissions they need, minimizing risks of privilege abuse and data exposure
Valence allows security teams to apply consistent security standards and visibility across their cloud environments. This partnership ensures that organizations protect their cloud security platform with the same vigilance they apply to SaaS applications—creating a unified, resilient defense.
Interested in learning more? Check out the Integration Brief and Request a Demo to see how Valence can secure your Wiz environment and other critical SaaS applications.
SaaS Security and IaaS Security—Why You Need Both

The rapid adoption of cloud computing over the past decade SaaS (Software-as-a-Service) and IaaS (Infrastructure-as-a-Service) has revolutionized how businesses operate. However, with this transformation comes a dual-edged sword: while these platforms offer unmatched flexibility and scalability, they also expose organizations to a growing array of security risks. Modern enterprises must navigate a complex ecosystem where misconfigurations, identity management issues, and data exposure can lead to devastating breaches. Addressing these challenges requires understanding the unique—and sometimes overlapping—risks associated with SaaS and IaaS environments.
Key Risks and Challenges in SaaS and IaaS Security
Identity Risks: Human and Non-Human
One of the most significant security challenges lies in managing identities—both human and non-human.
Human Identities: Implementing the Principle of Least Privilege (PoLP) is critical but notoriously difficult. In IaaS environments, roles and permissions often become overly permissive due to evolving business needs or fear of disrupting operations. IAM (Identity and Access Management) roles, which are intended to be scoped to specific resources, frequently expand beyond their intended boundaries, creating security risks. In SaaS environments, fragmented ownership and administration by business units complicate visibility and enforcement of access controls, leaving gaps that attackers can exploit. Weak or unenrolled authentication mechanisms - such as multi-factor authentication (MFA) - represents a significant risk of cloud identity security, both at the infrastructure level and SaaS level.
Non-Human Identities: Service accounts, API keys, and integration tokens introduce a different set of challenges. These non-human identities often operate without MFA or SSO protections, making them prime targets for attackers. Their always-on nature and high privilege levels mean that a single compromised token can have far-reaching consequences, including lateral movement across interconnected applications. Additionally, organizations struggle to detect anomalous activity in these accounts due to their continuous operation and broad access across multiple systems. For example, non-human accounts often have extensive permissions, which, if not regularly reviewed, can allow attackers to compromise sensitive systems undetected.
Misconfigurations
Misconfigurations are a persistent issue in both SaaS and IaaS environments. In IaaS, improper setup of storage buckets, overly permissive network access rules, and insufficient monitoring can expose sensitive data or allow attackers to gain unauthorized access. Similarly, in SaaS, misconfigured sharing settings or excessive user permissions can lead to unintended data exposure. As cloud environments become more dynamic, keeping configurations secure requires constant vigilance and automation.
Data Exposure
Data exposure is another critical risk, exacerbated by the decentralized nature of SaaS and IaaS. In SaaS platforms, external data shares often remain active long after their intended use, creating persistent vulnerabilities. For IaaS, sensitive data stored in improperly secured storage buckets or mismanaged databases can be accessed by unauthorized parties. These risks highlight the importance of continuous monitoring and lifecycle management for shared data.
Dynamic Cloud Environments
The speed and scale at which cloud environments evolve present additional challenges. Applications and integrations are frequently added, updated, or deprecated, often without security teams’ knowledge. This lack of visibility makes it difficult to identify potential vulnerabilities or ensure compliance with organizational policies.
Breach Examples: Lessons from the Field
Real-world breaches underscore the importance of robust SaaS and IaaS security practices. These incidents fall into three distinct categories:
Cloud/IaaS Breaches
- Capital One: A misconfigured AWS S3 bucket allowed a threat actor to exploit a vulnerability and access sensitive customer data, resulting in one of the largest breaches in financial services history. This incident revealed the critical importance of properly securing cloud storage and continuously auditing permissions.
- Toyota: Multiple data breaches stemming from cloud misconfigurations exposed customer and vehicle data. Toyota’s issues involved both insecure storage configurations and overly broad access permissions. For more details, see the summaries provided by CSO Online and SecurityWeek.
SaaS Breaches
- Microsoft Midnight Blizzard: One account without MFA in a test environment led to abused OAuth tokens and unauthorized access to Microsoft’s senior leadership’s corporate email in Microsoft 365. The Microsoft Midnight Blizzard breach is notable as it combines misconfigurations in both human and non-human identities, illustrating how multiple risks can combine to create dangerous attack paths.
- Snowflake Customer Breaches: Misconfigured authentication controls (lack of MFA) and weak access controls led to data exposure for multiple Snowflake customers. These Snowflake customer breaches emphasize the need for stringent access management and regular reviews of SaaS configurations.
- Learn more about the top 2024 SaaS breaches in this Valence Security blog.
Hybrid Breaches Exploiting SaaS and IaaS Gaps
- UNC3944 Attack: Attackers from UNC3944 exploited misconfigurations in an Okta SSO environment to breach both SaaS and IaaS layers. By leveraging gaps in both environments, the attackers demonstrated the importance of unified cloud security practices.
- GitHub OAuth Token Breach: Attackers had stolen OAuth user tokens issued to third-party vendors, Heroku and Travis-CI. These tokens were then used to download private data repositories from dozens of GitHub customers, including GitHub itself and npm, who had been using Heroku and Travis-CI-maintained OAuth applications.
These examples highlight the interconnected nature of cloud security and the need for comprehensive strategies to protect against evolving threats.
Understanding the SaaS and IaaS Security Landscape
SaaS Security: SaaS platforms deliver prebuilt applications via the cloud, managed almost entirely by the provider. Users are responsible for securing configurations, managing access controls, and safeguarding data shared or stored within these applications. Popular examples include Microsoft 365, Salesforce, and Slack.
IaaS Security: In contrast, IaaS solutions like AWS, Google Cloud Platform, and Microsoft Azure provide foundational computing resources, such as servers, storage, and networking, for users to build and run applications. Organizations bear significant responsibility for securing workloads, configurations, and data in these environments.
Both SaaS and IaaS platforms support critical business operations, but their security approaches vary due to differences in control, responsibility, and functionality.
Why SaaS Security Often Gets Less Attention
Despite the increasing reliance on SaaS for business operations, organizations often focus more on IaaS security. This disparity stems from several factors:
- IaaS Lacks Native Security Tools - While IaaS platforms grant organizations extensive control over their cloud infrastructure, SaaS platforms often create a false sense of security. Vendors manage application security, leading users to assume their data is inherently protected. However, this misconception can result in overlooked risks. Misconfigurations, which is the SaaS customer’s security responsibility, can expose sensitive information to breaches and exploitation.
- SaaS Often Lacks a Clear Owner - IaaS is typically managed by centralized IT teams with dedicated budgets for security tools, making it easier to assign ownership and accountability. SaaS, by contrast, is often purchased and managed by individual business units. Security responsibilities are fragmented, leaving IT or security teams to manage risks without clear ownership or budget alignment. This decentralized approach complicates SaaS security, as app owners often lack expertise in managing security configurations, third-party integrations, or user permissions.
- Organizations Rely on Inadequate SaaS Security Tools - Many businesses assume that existing tools like Single Sign-On (SSO) or Cloud Access Security Brokers (CASBs) sufficiently address SaaS security. While these tools play roles in managing access or monitoring certain configurations, they fall short of providing comprehensive visibility into SaaS risks. Dedicated SaaS Security Posture Management (SSPM) solutions are essential for monitoring configurations, third-party app integrations, and unused accounts.
Complementary Roles of SSPM and CSPM
To address security needs, organizations adopt solutions like Cloud Security Posture Management (CSPM) for IaaS and SaaS Security Posture Management (SSPM) for SaaS. These tools provide complementary benefits:
- CSPM: Automates the identification and remediation of misconfigurations in IaaS environments, ensuring compliance with security best practices.
- SSPM: Monitors SaaS environments for misconfigurations, unused data shares, and risky third-party app integrations, empowering organizations to secure SaaS ecosystems.
Together, these solutions enable businesses to address the full spectrum of cloud security risks.
Bridging the Gap in SaaS and IaaS Security
To mitigate these risks, organizations must adopt a proactive and holistic approach to cloud security. This includes implementing robust identity management practices, continuously monitoring for misconfigurations, and managing the lifecycle of data and integrations.
A More Holistic Approach to Cloud Security
A comprehensive strategy must address both human and non-human identity risks. For human identities, organizations should enforce MFA and integrate SSO wherever possible to reduce the attack surface. Regularly reviewing permissions and adhering to the Principle of Least Privilege are also crucial. For non-human identities, implementing token expiration policies, monitoring API activity, and restricting permissions to only what is necessary can significantly reduce risk.
In addition to identity management, organizations must prioritize visibility into both SaaS and IaaS environments. Tools that provide a unified view of configurations, permissions, and activity across platforms are essential. Automation plays a critical role in detecting and remediating issues quickly, minimizing the risk of breaches caused by misconfigurations or stale permissions.
Conclusion: Building Resilience in the Cloud
By focusing on the unique risks of both SaaS and IaaS, organizations can build a resilient cloud security strategy that protects critical assets and enables business growth. Real-world breaches offer valuable lessons, emphasizing the need for proactive measures and comprehensive tools to address the dynamic nature of cloud environments.
Learn more about Valence’s SaaS security capabilities today.
SaaS OAuth Attack Leads to Widespread Browser Extension Breach

A recent large-scale attack campaign targeting Google Chrome extensions, affecting up to 2.6 million users, underscores the urgent need for businesses to prioritize SaaS security, monitor OAuth tokens, and evaluate third-party integration risks.
What Happened?
A widespread attack compromised at least 35 Chrome browser extensions, including that of Cyberhaven, a cybersecurity company, exposing users to data theft and credential exfiltration. Key details include:
- Cyberhaven Incident: Hackers compromised Cyberhaven’s Chrome Web Store admin account to publish a malicious update. This update enabled attackers to exfiltrate sensitive data, such as session tokens and cookies. Cyberhaven’s disclosure provides additional insights into their response and ongoing security efforts.
- Consent Phishing Campaign: Attackers deployed consent phishing tactics, tricking users into granting permissions to a malicious OAuth application disguised as a legitimate "Privacy Policy Extension."
- Malicious Code Activity: The compromised extensions targeted sensitive data, including corporate credentials and Facebook Ads account information, through hidden code.
- AI Tools As An Attack Vector: Extensions like “AI Assistant - ChatGPT” and “GPT 4 Summary” were compromised, illustrating how attackers leveraged transitive trust to exploit high-privilege third-party integrations, including GenAI tools.
Understanding Consent Phishing
Consent phishing exploits OAuth consent flows, manipulating users into granting permissions to malicious applications without requiring credential theft. Here’s how it works:
- The attacker presents a legitimate-looking email with a link requesting consent to an OAuth application. In this case the email was posing to be from Google Chrome Web Store Developer Support.
- The OAuth application consent link requests access to the user’s permissions, such as the Google Chrome Web Store.
- By clicking "Allow," users unknowingly grant the attacker access to sensitive data or system APIs.
Unlike traditional phishing, consent phishing bypasses multifactor authentication (MFA) because it doesn’t request credentials. Instead, users are duped into approving access without realizing the implications. The method exploits both user trust in application authentication (including OAuth) as well as their readiness to click “Accept” without reading the permissions being granted. Once permissions are granted, attackers can:
- Access APIs and exfiltrate data
- Impersonate users within SaaS (and other) applications
- Bypass security controls without raising alarms
Supply Chain Attacks via Browser Extensions
The breach highlights how browser extensions can act as entry points for supply chain attacks. Extensions often require broad permissions, including access to credentials, browser data and session tokens—making them an attractive target for attackers. When compromised, they can act as conduits for attackers to infiltrate corporate systems. In a sense, browsers have become pivotal endpoints in modern cybersecurity.
Attackers target trusted third-party vendors to exploit transitive access, leveraging the permissions granted to extensions and their underlying SaaS platforms.
GenAI Tools: Opportunities and Risks
Many of the targeted Chrome extensions included AI-focused tools, such as "GPT 4 Summary" and "Search Copilot AI Assistant." This reflects an emerging trend of attackers targeting high-trust, high-privilege third-party vendors, including GenAI tools.
While GenAI tools unlock transformative capabilities, their adoption introduces unique security challenges:
- Shadow IT and Unsanctioned Use: Employees often trial free GenAI tools without IT approval, creating blind spots for security teams.
- Data Access Risks: GenAI tools require access to vast amounts of sensitive data across SaaS environments, such as sales pipelines, customer records, and messaging histories.
- Privacy Concerns: Free or lesser-known GenAI tools may collect user data for training purposes, risking regulatory violations and inadvertent data exposure.
- Rapid Innovation, Complex Security: The fast pace of innovation in GenAI creates a dynamic and challenging security landscape.
Attackers target these tools because of the significant access and privileges they require. Security teams must actively monitor shadow AI usage while enforcing least-privilege principles for sanctioned tools. Additionally, organizations should implement real-time monitoring for suspicious activities and unauthorized permissions to mitigate risks associated with GenAI adoption.
Secure Your SaaS-to-SaaS Integrations
OAuth tokens, often granted through browser extensions or third-party integrations, play a critical role in SaaS security. Organizations should:
- Provide Phishing Awareness Training: Educate users on the risks of malicious consent requests and how to identify them, or to first verify with the security team
- Monitor Token Activity: Regularly audit OAuth tokens to ensure they are active and appropriately scoped. In addition, utilize identity threat detection and response (ITDR) capabilities detect live abuse of tokens and other non-human identities
- Revoke Inactive Tokens: Revoke tokens linked to inactive or deprovisioned accounts to minimize risk
- Restrict Permissions: Grant the least privilege necessary for each token’s purpose
- Browser Security: Implement browser security policies and monitor extension activity
These measures help reduce risks but must be coupled with consent awareness training to address the root cause of many attacks: users unknowingly granting dangerous permissions.
How Valence Helps: Valence empowers organizations to identify, monitor, and manage OAuth tokens and other non-human identities (NHIs) across SaaS applications. By delivering detailed visibility and enforcing least-privilege access models, Valence helps security teams to reduce risks associated with over-privileged or inactive tokens. Through real-time monitoring and remediation capabilities, organizations can swiftly detect suspicious activity, reducing the likelihood of unauthorized access or breaches.
Conclusion
This attack campaign is another SaaS-focused breach, leveraging third-party integrations to exploit trust and gain access to sensitive environments. This incident highlights the broader challenges of SaaS security and the importance of:
- Regularly audit third-party integrations and browser extensions
- Educate users on the risks of consent phishing and shadow IT
- Implement robust SaaS security measures, including monitoring OAuth tokens and managing permissions
As businesses increasingly rely on SaaS applications, GenAI tools, and browser extensions, attackers are targeting these high-trust ecosystems to exploit gaps in security. To safeguard sensitive data, organizations must adopt comprehensive SaaS security strategies that address the growing complexity and dynamic risks of modern application environments.Have a question for Valence or want to conduct a complimentary risk assessment of your SaaS environment? Request one today.
How to Choose the Best SaaS Security Platform

The proliferation of Software-as-a-Service (SaaS) applications has revolutionized the way organizations operate, offering unparalleled scalability, accessibility, and efficiency. However, with these advantages come significant security challenges. From misconfigurations and overprivileged accounts to risky SaaS-to-SaaS integrations, today’s SaaS environments require robust security measures tailored to address their unique risks.
In this guide, we’ll explore what to look for in a SaaS security platform to help protect your organization against SaaS-specific threats and ensure seamless operations.
Understanding SaaS Security Risks
Recent high-profile SaaS breaches, such as Microsoft's Midnight Blizzard attack and the widespread and massive Snowflake customer breaches, highlight the urgency of addressing these risks. Understanding the risks inherent in SaaS environments is foundational to selecting the right security platform. These risks include:
Before diving into the features of an ideal SaaS security platform, it's essential to understand the primary risks organizations face in SaaS environments:
- Misconfigurations: SaaS applications often have complex and unique configuration settings. Misconfigured application settings can expose sensitive data or enable unauthorized access. In large organizations, with thousands of SaaS users and dozens of applications or more, managing these configurations is increasingly difficult.
- Overprivileged Accounts: Excessive permissions granted to users increase the risk of accidental or malicious data breaches. When you add to the risks of failed offboarding of SaaS accounts, these risks multiply.
- Inactive Non-Human Identities: SaaS-to-SaaS integrations using non-human identities such as service accounts, OAuth tokens and APIs are risky as multi-factor authentication (MFA) cannot be applied to them, they often are granted high privileges, and they typically remain active even after they are no longer needed, creating hidden security risks.
- External Data Shares: Unmonitored and inactive data shares can lead to unauthorized access and data leaks. Open link shares, those made available to "Anyone with the link”, can be significantly dangerous.
- Shadow IAM Accounts: Accounts that bypass single sign-on (SSO) systems remain unmanaged and pose significant security risks.
- SaaS Threat Detection: Suspicious user actitives—of both human and non-human identities—can be indicative of account takeover and/or data breach attempt in progress. Advanced threat detection and remediation capabilities, such as ITDR (Identity Threat Detection and Response), are crucial to identify and mitigate risks in real-time.
Key Features to Look for in a SaaS Security Platform
When evaluating SaaS security platforms, it’s important to focus on features that address common SaaS-specific risks, such as misconfigurations, overprivileged accounts, and shadow IAM. Here are the critical capabilities to prioritize:
To address these challenges, organizations need a SaaS security platform equipped with advanced functionalities. Here are the critical features to consider:
1. SaaS Security Posture Management (SSPM)
SSPM capabilities continuously monitor and manage the security posture of SaaS applications by detecting misconfigurations, tracking changes, and providing recommendations for remediation. Look for platforms that support:
- Configuration monitoring and drift detection
- Compliance alignment with industry standards
- Automation to streamline remediation efforts
2. Comprehensive Visibility
The platform should provide a holistic view of all business-critical applications and the following elements:
- SaaS-to-SaaS integrations
- User activity and permissions
- Non-human identities, such as API keys and OAuth tokens
- Data protection settings
3. Risk Remediation
Proactive risk remediation capabilities, such as automatic revocation of unused permissions and termination of inactive integrations or external data shares, are vital for reducing your attack surface.
4. Advanced Threat Detection
Identity Threat Detection and Response (ITDR) capabilities are critical for identifying unauthorized access attempts and anomalies in real time.
5. Ease of Deployment
Choose a solution that integrates seamlessly into your existing security stack and offers rapid deployment without requiring extensive configuration or maintenance.
6. Scalability
The platform should support all your SaaS applications, regardless of size or complexity, ensuring consistent security across the organization.
Comparing CASB vs. SSPM for SaaS Security
When evaluating SaaS security tools, understanding the differences between Cloud Access Security Brokers (CASBs) and SSPMs is critical:
- CASBs: Focus primarily on access control, data loss prevention (DLP), and threat protection. However, they fall short in monitoring SaaS configurations and addressing SaaS-to-SaaS risks.
- SSPMs: Offer advanced security capabilities, including configuration monitoring, non-human identity management, and compliance enforcement, making them essential for modern SaaS environments.
Organizations increasingly recognize the value of SSPMs, with adoption rates nearing parity with CASBs. For businesses relying on complex SaaS ecosystems, SSPMs provide the comprehensive protection needed to mitigate evolving risks.
Selecting the Right SaaS Security Platform
To choose the best SaaS security platform for your organization, consider the following steps:
- Identify Your Security Gaps: Conduct a thorough risk assessment of your SaaS environment to pinpoint security risks.
- Evaluate Features: Ensure the platform includes SSPM capabilities, real-time threat detection, and automated risk remediation.
- Check Compatibility: Verify that the solution integrates with your existing tools, such as SIEMs, IDPs, and endpoint security platforms.
- Assess Scalability: Choose a platform that can grow with your organization and support an expanding SaaS application portfolio.
- Prioritize Usability: Opt for a platform with an intuitive interface and actionable insights to empower your security team.
How Valence Security Can Help
Valence Security is at the forefront of SaaS security, offering a comprehensive platform designed to address today’s most pressing SaaS security challenges. Our solution provides:
- SaaS Security Posture Management (SSPM): Continuous monitoring and management of SaaS configurations, permissions, and integrations.
- Automated Risk Remediation: Fix misconfigurations, revoke unused permissions, and terminate inactive data shares. Valence’s flexible SaaS risk remediation capabilities empower security teams to efficiently address security risks and misconfigurations with a combination of guided remediation, automated workflows and business user collaboration.
- Advanced Threat Detection: Valence's SaaS security platform provides robust identity threat detection and response (ITDR) capabilities to address the unique challenges of securing SaaS environments. By offering comprehensive visibility into user activities, uncovering hidden and suspicious events, and enabling SaaS threat investigation, Valence empowers security teams to protect SaaS sensitive data and respond to threats rapidly.
Explore our SaaS Security platform here.
For detailed guidance on evaluating SaaS security solutions, download our SSPM checklist. Ready to see Valence in action? Request a demo today.
The Challenge of Distributed SaaS Management—Balancing Productivity and Security

The rise of SaaS applications has transformed the way organizations operate, enabling greater collaboration, agility, and efficiency. Business-critical tools such as Salesforce, HubSpot, Workday, NetSuite, and GitHub are essential for departments like sales, marketing, HR, finance, and R&D. These tools empower teams to work independently, adopt cutting-edge technologies, and innovate faster.
However, this same model poses significant SaaS security challenges for IT and security teams. Without centralized oversight, security professionals may lack the visibility, expertise, and control necessary to ensure SaaS applications are securely managed. This disconnect leaves organizations exposed to risks, from misconfigured applications to unauthorized data access, and creates roadblocks when managing risks and responding to security incidents.
In this blog, we’ll explore the benefits of distributed SaaS management for organizations, delve into the security risks it introduces, and outline actionable steps security teams can take to address these challenges while maintaining productivity and collaboration.
What Is Distributed SaaS Management?
Distributed SaaS management refers to the practice where individual business units or departments independently select, manage, and administer SaaS applications, rather than relying on centralized IT oversight. This model supports agility and tailored tool adoption but often introduces security and governance complexities.
Benefits of Distributed SaaS Ownership
The decentralization of SaaS application management allows departments to choose and administer the tools best suited to their needs. This flexibility brings several advantages:
1. Tailored Tool Adoption
A decentralized approach to SaaS management allows departments to make decisions that align with their specific goals. Marketing teams can deploy platforms like HubSpot or Asana to streamline campaigns, while R&D departments may prioritize tools such as GitHub or Jira to enhance software development workflows. By granting ownership of SaaS applications to the departments that use them, organizations enable their teams to work more efficiently and adopt cutting-edge technologies.
2. Reduced Bottlenecks
This independence fosters productivity by allowing teams to select and manage applications without waiting for IT’s approval or support. For example, a finance team can implement an expense management tool to improve budgeting processes without delays, while HR departments might adopt Workday to streamline recruitment and onboarding. This flexibility reduces bottlenecks and ensures that critical operations aren’t hindered by reliance on IT.
3. Innovation Enablement
Decentralization promotes innovation by allowing departments to experiment with emerging technologies. Whether it’s marketing leveraging AI tools to enhance campaign strategies or sales teams integrating customer relationship management (CRM) tools to improve client engagement, this freedom allows organizations to stay competitive in fast-changing markets.
SaaS Security Risks in Distributed SaaS Models
While distributed SaaS management drives efficiency and innovation, it also creates complex security risks. Security and IT teams often struggle to maintain visibility, governance, and control over a sprawling SaaS ecosystem, leading to several key challenges:
1. Lack of Visibility Into SaaS Usage
IT and security teams typically oversee core applications like Microsoft 365 or Google Workspace but may lack visibility into department-specific tools like Salesforce, Workday, or GitHub. This fragmented view makes it difficult to:
- Identify which applications are in use
- Track user accounts, permissions, and access levels
- Monitor sensitive data sharing or external integrations
2. Security Misconfigurations by Non-Security Admins
SaaS administrators in business units often prioritize ease of use over security, unintentionally creating security risks. Common missteps include:
- Configuring local user accounts that bypass corporate Single Sign-On (SSO) policies
- Granting broad permissions to third-party integrations without understanding their risks
- Misconfiguring data sharing settings, exposing sensitive information to external parties
For example, a marketing team adopting a GenAI-powered content tool may inadvertently grant it access to proprietary customer data without IT oversight.
3. Limited Application Expertise in Security Teams
Conversely, security teams often lack in-depth knowledge of department-used SaaS applications. Without familiarity with tools like Salesforce, Workday or GitHub, they may struggle to:
- Understand application-specific risks
- Provide tailored security guidance to business units
- Assess the business impact of potential misconfigurations
This knowledge gap complicates risk prioritization and remediation efforts, leading to inefficiencies and delays.
Shifting From From Blame to Responsibility in Securing Distributed SaaS Distributed SaaS Applications
Andy Ellis, Partner at YL Ventures and former CSO at Akamai, describes the security challenges of distributed SaaS management succinctly:
“Business units have disintermediated IT, yet they still have a security problem they don’t want to deal with. The CISO’s team often becomes the scapegoat, taking blame for security issues that arise because IT and security teams are locked out of managing these applications. SaaS applications like HubSpot or Salesforce are often invisible to IT, with business units pushing back on any security involvement. In today’s SaaS-native world, IT’s role is evolving—moving away from traditional tasks like deploying and patching servers to primarily managing security risks in SaaS environments.”
Ellis emphasizes the importance of collaboration: “Security teams need to shift their mindset from saying, ‘We didn’t deploy this, so it’s not our responsibility’ to ‘If the business is using it, it’s a business application, and our job is to secure it.’”
Bridging the Gap - Strategies for Secure Distributed SaaS Management
Valence Security provides a centralized SaaS security platform designed to address the challenges of distributed SaaS management while preserving the benefits of decentralization. By offering robust tools for visibility, collaboration, and control, Valence empowers security teams, SaaS admins, and business users to work together effectively and securely.
Centralized Visibility Across SaaS Applications
Valence enables organizations to consolidate visibility across all their SaaS applications, from Microsoft 365 and Google Workspace to department-specific tools like Salesforce, NetSuite, and GitHub. With a unified view of user accounts, permissions, integrations, and configurations, security teams can quickly identify misconfigurations, overprivileged accounts, and risky external data shares. This comprehensive visibility eliminates blind spots and allows security professionals to take proactive measures to protect their organization.
Role-Based Access Control (RBAC) for Streamlined Management
Valence’s platform includes robust RBAC capabilities, allowing organizations to assign tailored access permissions to SaaS admins and security teams. This ensures that each team has the appropriate level of access to perform their responsibilities without compromising security. For example, SaaS admins can manage configurations and integrations for their applications, while security teams retain oversight and control over critical settings and policies. The Valence platform can also be used to provide clear, actionable guidelines for SaaS admins, helping to facilitate training on secure SaaS configuration practices. As a result, this simplifies security management for non-security experts.
Automating Risk Remediation To Reduce Burdens
SaaS administrators often hesitate to engage with security concerns—but what if managing SaaS risks, especially remediation, became far simpler? Valence makes this possible by combining ease of use with automated configuration monitoring and risk remediation. The platform identifies and resolves misconfigurations, excessive data shares, and risky integrations, significantly reducing the burden on teams.
Valence also empowers organizations to create policies that notify employees via Slack or email before changes occur, enabling direct engagement and timely remediation. By providing security teams with multi-choice remediation options and fostering collaboration with business users, Valence not only streamlines risk mitigation but also enhances SaaS security. This approach minimizes manual effort while boosting ownership and accountability among business users, creating a more secure and efficient SaaS environment.
Fostering Collaboration Between Teams
Valence fosters stronger collaboration by promoting transparency and shared responsibility across the organization. Security teams can partner with SaaS admins to implement best practices, while business users gain the tools and knowledge needed to make secure decisions. By shifting from a gatekeeper role to that of an enabler, security teams can build trust and cooperation, ensuring that security becomes a shared priority.
More Productive, More Secure with Valence
The distributed SaaS management model offers undeniable benefits for innovation and efficiency but requires a proactive approach to security. By fostering collaboration, consolidating visibility, and leveraging automation, organizations can secure their SaaS environments without compromising productivity. Discover how Valence Security helps you achieve this balance. Request a Demo today!
SaaS Security Best Practices and Strategies for 2025

The adoption of Software as a Service (SaaS) has revolutionized how businesses operate, offering scalability, flexibility, and cost savings. However, as the use of SaaS continues to expand, so do the associated security risks. From data breaches to misconfigurations, the challenges facing organizations in securing SaaS applications are evolving. As we approach 2025, it’s crucial for security professionals to refine their strategies and adopt best practices to protect their SaaS environments.
In 2025, securing SaaS applications and the data they manage will require sophisticated strategies and technologies to mitigate evolving threats. This post explores the key strategies, best practices, and tools for securing SaaS applications, with a focus on SaaS data security, SaaS-to-SaaS integrations, and mitigating common SaaS security challenges.
Why SaaS Security Is a Growing Concern
The convenience of SaaS applications—accessibility from anywhere, scalability without significant infrastructure investment, and easy collaboration across teams—has made them the backbone of modern organizations. However, this shared model of data access and management increases the attack surface for cyber threats.
SaaS platforms store sensitive data across multiple tenants, making them attractive targets for cybercriminals. Furthermore, SaaS applications are often integrated with other tools, creating complex ecosystems that can amplify security risks. Data breaches and security misconfigurations remain some of the most pressing threats to organizations leveraging SaaS solutions. These risks underscore the need for a multi-layered security approach to protect against unauthorized access, data loss, and cyber threats.
Understanding SaaS Security Challenges
SaaS security has become a critical concern for organizations relying on cloud-based applications to manage everything from communication to customer data. Below are some of the most pressing challenges:
SaaS Misconfigurations
SaaS misconfigurations are one of the leading causes of security breaches in SaaS environments. Incorrect access control settings, improperly configured APIs, and other configuration errors can expose sensitive data to unauthorized users. As organizations integrate more third-party applications, the risk of misconfigurations grows, potentially creating vulnerabilities that cybercriminals can exploit.
Sensitive Data Exposure
The interconnected nature of SaaS platforms means that sensitive data is often stored in multiple locations, shared between systems, and accessible to a broad range of users. This complexity increases the risk of accidental data exposure, especially when data is not properly shared, stored, or protected. Without proper controls in place, sensitive information can be inadvertently exposed to those who should not have access.
External Data Sharing Risks
External data sharing, particularly within platforms like Google Drive, OneDrive, or Salesforce, can expose sensitive information if not managed properly. Overly permissive sharing settings or sharing with external users who no longer require access can inadvertently compromise data security. Organizations need to regularly audit inactive shares and set policies to ensure that only authorized users have access to shared data.
SaaS-to-SaaS Integration Risks
Many organizations rely on multiple SaaS applications that integrate with each other to streamline workflows. While these integrations enhance operational efficiency, they also create a complex web of interdependencies that can be difficult to monitor and secure. If mismanaged, SaaS-to-SaaS integrations can provide attackers with pathways to compromise multiple systems simultaneously, significantly escalating the impact of a breach.
Uncontrolled Access and Shadow IAM
In decentralized SaaS environments, managing user permissions can be challenging. Shadow Identity and Access Management (IAM)—where users create local, unmanaged accounts that bypass centralized security controls—introduces significant security gaps. These shadow accounts can remain active even after an employee departs, creating a hidden vulnerability. Additionally, weak authentication methods, such as unenforced Multi-Factor Authentication (MFA) or Single Sign-On (SSO), can make it easier for attackers to gain unauthorized access using only a username and password.
Managing Permissions and Roles
With many users accessing SaaS applications, it's crucial to ensure that permissions are properly set and maintained. Mismanagement of permissions can lead to overprivileged accounts, which in turn increases the risk of data leakage or unauthorized access to sensitive information. Moreover, failing to fully offboard former employees from all connected SaaS applications is a common issue, often exacerbated by local accounts, multiple identity management systems, and manual processes that are difficult to track and enforce.
Insufficient SaaS Security Monitoring
SaaS environments are dynamic, frequently updated, and often integrated with other systems. Without continuous monitoring, organizations may miss critical early signs of a security breach. Detecting anomalies and other threats—such as unusual data access patterns or unauthorized login attempts—is essential for minimizing breach risks and ensuring timely response.
Shadow SaaS and Unmanaged Risk
It’s crucial to have visibility into all SaaS applications connected to your enterprise accounts. Employees often sign up for and use unsanctioned SaaS applications to meet work needs, bypassing IT oversight and security protocols. This "shadow SaaS" introduces blind spots and potential risks that can undermine the security of the broader SaaS environment.
Best Practices for Securing SaaS Applications in 2025
To mitigate these risks and strengthen SaaS security, organizations should adopt the following best practices:
1. Multi-Factor Authentication (MFA)
Implementing multi-factor authentication (MFA) is one of the most effective ways to protect against unauthorized access. By requiring users to provide additional verification beyond just a password, MFA makes it significantly harder for attackers to gain access to sensitive SaaS applications.
2. Zero Trust Architecture
A Zero Trust approach is critical for SaaS security. The Zero Trust model operates on the principle of “never trust, always verify,” ensuring that no user or device is trusted by default, regardless of their location. This model emphasizes continuous authentication, strict access controls, and a principle of least privilege, reducing the attack surface in SaaS environments.
3. SaaS Security Posture Management (SSPM)
SSPM capabilities help organizations manage and continuously assess the security posture of their SaaS applications. By automating the discovery of misconfigurations and vulnerabilities, SSPM platforms enable organizations to proactively mitigate risks before they lead to a breach. These tools also provide visibility into SaaS-to-SaaS integrations and help enforce security policies across all applications.
4. External Data Share Audits
Regular audits of external data shares ensure that no sensitive data is exposed due to outdated or improper sharing settings. By identifying and closing inactive shares, businesses can significantly reduce the risks associated with data exposure.
5. SaaS Security Awareness and Training
While technology plays a significant role in SaaS security, users also play a key part. Regular training on security best practices, such as recognizing phishing attempts and creating strong passwords, helps reduce the likelihood of human error compromising the system.
6. Comprehensive SaaS Security Monitoring
Robust monitoring tools can provide real-time insights into SaaS security. These tools should track user activity, monitor data access, and detect anomalies in real-time. By combining automated monitoring with human oversight, organizations can ensure they are quickly alerted to potential SaaS security threats and take action before damage is done.
How Valence Security Helps
Valence Security is designed to help organizations tackle the most challenging SaaS security risks, from misconfigurations to shadow IAM. Our platform offers the following capabilities:
- Automated SaaS Risk Detection: Valence’s SaaS Security Posture Management (SSPM) capabilities automatically identifies misconfigurations and potential security RISKS across your SaaS apps. This proactive approach ensures that issues are caught before they can be exploited by attackers.
- Continuous Monitoring: With Valence’s SaaS security monitoring tools, you gain full visibility into your SaaS environment, including real-time tracking of SaaS-to-SaaS integrations and user activities. This helps prevent unauthorized access and mitigates the risk of breaches.
- SaaS Data Security: Valence’s platform provides the ability to scan for exposed data across multiple SaaS platforms, including external data shares, risky third-party integrations, or identity-based misconfigurations, helping to ensure that sensitive information is protected from unauthorized access.
- SaaS-to-SaaS Integration Management: As organizations integrate more SaaS applications, managing these connections becomes increasingly complex. Valence’s platform enables secure SaaS-to-SaaS integrations by identifying and addressing risky configurations.
- Streamlined Remediation: Valence’s platform helps security teams quickly remediate SaaS security risks through a mix of guided steps, one-click fixes, and automated workflows and providing actionable insights into potential gaps. This reduces manual workloads and accelerates the response to emerging threats.
Why SaaS Security Posture Management (SSPM) is Essential for 2025
As SaaS adoption continues to rise, so do the risks associated with managing multiple interconnected applications. SSPM is becoming an essential security tool for organizations to monitor and manage the security of their SaaS environments. It allows businesses to continuously assess and improve their security posture, reduce human error, and ensure compliance with industry standards.
The complexities of modern SaaS environments require a holistic, automated approach to security. SSPM provides the scalability, visibility, and agility needed to secure these environments effectively.
Request a Demo
Ready to take your SaaS security to the next level? Valence Security offers a comprehensive SaaS Security platform designed to identify, monitor, and remediate SaaS security risks. Contact us today to schedule a demo and see how we can help you safeguard your SaaS applications for 2025 and beyond.
Key Risks of Software as a Service and How to Manage Them

As organizations increasingly adopt Software as a Service (SaaS) applications, they gain scalability, flexibility, and ease of use. However, the rapid adoption of SaaS also introduces unique security risks that can jeopardize sensitive data, compliance efforts, and operational continuity. Understanding these key SaaS security risks and implementing targeted strategies to address them is critical for securing SaaS environments effectively.
The Challenge of Identity Management in SaaS
Identity and access management (IAM) is foundational to SaaS security, yet it is also one of the most challenging areas. Risks associated with SaaS identity management include:
- Overprivileged Accounts: Employees often retain access to sensitive data or systems far beyond their job requirements. This overprovisioning can inadvertently expand the organization’s attack surface.
- Shadow IAM Accounts: Local accounts created outside of centralized Single Sign-On (SSO) systems, such as unmanaged GitHub accounts, bypass lifecycle management. These unmanaged accounts can persist after an employee leaves, creating significant blind spots in security.
- Weak Authentication Practices: Despite the availability of robust authentication tools, many organizations fail to enforce Multi-Factor Authentication (MFA) consistently, leaving accounts vulnerable to compromise.
How to Address These Risks: Adopt strong IAM protocols, enforce the Principle of Least Privilege, and conduct periodic audits to identify and revoke unnecessary access. Prioritize implementing MFA across all user accounts to reduce the likelihood of credential compromise.
Protecting SaaS Data from Persistent Threats
Sensitive information stored in SaaS applications is a lucrative target for cyber attackers. Without proper safeguards, data security risks in SaaS can multiply.
- Excessive External Sharing: Files shared externally using settings like "anyone with the link" can remain accessible indefinitely, increasing the risk of unauthorized access.
- Dormant Shares: Data shared for temporary collaboration often becomes orphaned, with no monitoring or expiration policies in place. Valence’s 2024 State of SaaS Security Report found that over 90% of external file shares are inactive but remain accessible.
How to Address These Risks: Regularly audit file-sharing permissions, restrict external sharing, and enforce expiration dates for shared links. Combine policy-based governance with automation to detect and disable unused shares proactively.
Misconfigurations: A Silent SaaS Security Threat
SaaS platforms are highly dynamic, which makes them prone to misconfigurations. Common examples include overly permissive access controls, unlimited cloud sessions, and settings that are enabled by default but not aligned with security policies.
Another problem is configuration drift. Over time, SaaS environments deviate from established security baselines due to new features, user changes, or updates. This drift can create hidden vulnerabilities that attackers exploit.
How to Address These Risks: Use automated tools for continuous configuration monitoring and remediation. Establish secure baseline configurations for all SaaS applications and review them regularly to ensure alignment with your security policies.
Risks from SaaS-to-SaaS Integrations
SaaS-to-SaaS integrations enhance productivity but also introduce new vectors for attack. These integrations often rely on non-human identities (NHIs) such as API keys and OAuth tokens.
- Unmanaged Tokens: If not regularly rotated or revoked, tokens can provide unauthorized access to sensitive systems.
- Excessive Permissions: Integrations often request broad access rights that exceed their functional requirements, increasing exposure.
How to Address These Risks: Implement strict access controls and monitor all active integrations for excessive permissions. Revoke tokens linked to inactive integrations or employees and adopt tools that provide visibility into SaaS interconnectivity.
SaaS Lifecycle Management: The Hidden Cost of Inactive Accounts
When user accounts, integrations, and data shares are not properly decommissioned, they can linger as unmonitored security vulnerabilities. Risks associated with SaaS lifecycle management include:
- Inactive Accounts: Accounts that are not deactivated during employee offboarding can become backdoors for attackers.
- Orphaned Integrations: SaaS-to-SaaS integrations tied to inactive accounts may retain access to critical systems and data long after their intended use.
How to Address These Risks: Automate the deprovisioning process for both user accounts and SaaS integrations. Use centralized visibility tools to identify inactive accounts and orphaned integrations promptly.
The Rising Risks of Shadow SaaS and GenAI
The rapid rise of generative AI (GenAI) tools integrated with business-critical SaaS applications introduces both transformative potential and significant security challenges. These tools often create a complex landscape where both sanctioned and unsanctioned AI (shadow AI) can bypass traditional security measures.
GenAI tools often require broad access to sensitive data across multiple SaaS platforms to function effectively, raising serious concerns about data privacy and security. This level of access can inadvertently expose sensitive information or lead to unauthorized data usage, making oversight and management of these tools a critical priority for security teams.
How to Address These Risks: Organizations must address these risks by implementing policies to manage GenAI adoption, closely monitoring SaaS-to-SaaS integrations involving GenAI tools, and providing employees with secure, approved alternatives.
The Compliance and Regulatory Landscape
Organizations must ensure their SaaS applications meet regulatory requirements, such as HIPAA, SOC 2, or ISO 27001. Mismanagement can result in non-compliance, financial penalties, and reputational damage.
How to Address These Risks: Establish comprehensive compliance checklists and align SaaS application configurations with industry standards. Leverage tools that provide automated compliance monitoring and reporting to streamline audits.
How Valence Helps Lower Saas Risk Exposure
Valence Security simplifies and fortifies SaaS security by providing comprehensive visibility, continuous monitoring, and automated remediation for the unique challenges of SaaS environments. Our platform is designed to address the following areas:
- Identity and Access Management: Discover and remediate overprivileged accounts, inactive users, and shadow IAM accounts.
- Data Security: Identify and secure dormant or risky external data shares to minimize the risk of exposure.
- Configuration Management: Continuously monitor for misconfigurations or configuration drift, ensuring compliance with security baselines.
- Non-Human Identity Management: Detect and revoke unnecessary or risky SaaS-to-SaaS integrations and API tokens.
- Lifecycle Management: Automate offboarding processes to ensure accounts and integrations tied to departed employees are deprovisioned.
- Shadow SaaS and GenAI Risks: Gain visibility into unauthorized AI tools, assess their access permissions, and ensure secure alternatives are available for your teams.
Want to learn more about how Valence’s SaaS Security Posture Management (SSPM) platform can help secure your SaaS ecosystem? Read more about our SSPM capabilities or request a demo today.
Strengthening SaaS Applications with Secure Non-Human Identity Management

Non-human identities (NHIs), such as service accounts, API keys, and OAuth tokens, are an essential yet often overlooked part of the digital workforce. As SaaS applications grow more complex, so too does the network of NHIs linking different platforms. While these identities automate workflows, they also pose unique challenges for SaaS security teams, especially as their volume and interconnectedness increase.
The rise of decentralized ownership of SaaS applications—where different business units, such as marketing, sales, human resources and R&D independently manage their own tools—has further complicated this problem. As business units adopt SaaS solutions like HubSpot, Salesforce, Workday, or GitHub without involving IT or security teams, organizations face fragmented visibility and control, increasing their vulnerability to threats.
Security teams must closely monitor these NHIs, which vastly outnumber human identities. The 2024 State of SaaS Security Report reveals the scale of the challenge: for every human identity, there are 8.6 non-human identities on average! These third-party SaaS integrations, and the NHIs that power them, create several new security challenges for organizations.
NOTE: A slightly different version of this article first appeared in Forbes in June 2024 and can be read here.
Expanding Complexity - Managing SaaS-to-SaaS Integrations in An Increasingly Connected Ecosystem
The power of SaaS lies in its ability to easily connect and automate workflows between applications with third-party integrations. These SaaS integrations leverage NHIs to exchange data and functionality, making tasks faster for everyone. Examples of popular SaaS integrations connected to core platforms include Superhuman with Google Workspace, Calendly with Microsoft 365, and Gong with Salesforce.
While these integrations improve the efficiency of business operations, they add complexity to SaaS security.
The Distributed Ownership Challenge
In many organizations, each department is responsible for selecting and managing the SaaS tools it relies on. While this approach fosters innovation and agility, it can also create gaps in security.
This distributed ownership is particularly problematic for SaaS-to-SaaS integrations. Often occurring without security team involvement, these integrations result in fragmented visibility over which applications are interconnected, in addition to access control challenges. Security teams struggle to protect these integrations and, in some cases, are unaware of critical misconfigurations or other risks.
Non-human identities often sit at the intersection of these integrations. These identities enable applications to communicate with one another automatically, yet they rarely receive the same attention as human accounts. Inadequate visibility into these non-human identities exacerbates the issue. When service accounts are misconfigured or left unchecked, they can expose an organization's infrastructure to risk without detection.
Moreover, non-IT SaaS administrators often lack the expertise to configure integrations securely, while business users may overlook security risks altogether.
Key Risks in SaaS-to-SaaS Integrations
- Over-Privileged Access: When a SaaS user adopts a new integration, part of the process is enabling access privileges to the core SaaS platform. Granting third-party integrations more access than necessary can expose sensitive data. The 2024 State of SaaS Security Report identified that 33% of integrations have access to sensitive data, often exceeding their actual needs. With nearly 2,000 integrations in the average organization, this presents significant risk.
- Inactive Integrations: Third-party SaaS integrations require ongoing lifecycle management, from initial adoption to eventual retirement, but a significant portion of integrations become inactive over time. This means that an API key or OAuth token is valid, but not used by the connected application. This leaves unused integrations with valid access privileges, creating security risks.
- Supply Chain Risk: The security posture of the vendor behind a third-party application can impact overall security. If a third-party application has poor security hygiene, data handling procedures, access controls, and incident response protocols, a security incident can easily compromise the SaaS environment.
High-Impact SaaS Breaches That Targeted Non-Human Identities
Traditional identity security best practices don’t typically work for non-human identities. Unlike human users, NHIs often lack robust security measures like multi-factor authentication.
Interestingly, the State of SaaS Security Report found that 94% of security executives believe they have a process in place to manage NHIs. Yet, recent high-profile breaches demonstrate a critical gap between perception and reality
- Microsoft Midnight Blizzard - Nation-state attackers exploited a legacy OAuth application with full permissions to Microsoft's production environment, granting them access to sensitive data, including emails and documents from senior leadership.
- Cloudflare - Following a breach at Okta, attackers used stolen service tokens and credentials to gain administrative access to Cloudflare's Atlassian instance. Cloudflare’s security team had performed a forensics analysis and rotation of 5,000+ production credentials, yet missed 4 credentials of a service token/account that belonged to SaaS applications. The attackers were able to expose source code despite these extensive credential rotations.
- Dropbox Sign - Attackers compromised a service account used by Dropbox Sign, gaining access to a treasure trove of user data, including emails, usernames, and general account settings. They also were able to access customer API keys and OAuth tokens, potentially impacting customers.
SaaS Security as an Enabler - Shifting the IT and Security Mindset
I recently discussed SaaS security with Andy Ellis, Partner at YL Ventures and former CSO at Akamai. He emphasized the importance of security teams adopting an enabling mindset where they act as collaborators, rather than gatekeepers.
Rather than adopting a "gatekeeper" mentality—where the security team’s job is to block access to third-party SaaS applications—Andy suggested security teams should embrace a more collaborative, "enabler" role. In this model, security teams actively support the business by providing tools, guidance, and best practices for adopting and integrating new SaaS tools securely.
Andy shared:
"The security team should focus on being a business enabler. For example, instead of blocking third-party SaaS integrations, provide employees with an onboarding tool that helps them understand which applications are essential—and already supported—for their role. This tool could include a curated list of SaaS tools they’re likely to need, with instructions on how to access them securely and set up proper integrations. Shifting to a proactive, enabling model helps employees feel supported rather than restricted. When the security team is seen as a resource rather than a roadblock—helping employees set up and configure integrations securely—it fosters collaboration, not conflict."
When employees know they can turn to security for guidance on how to use SaaS applications safely, it reduces the tendency to bypass security protocols altogether. This shift transforms security teams into trusted partners, promoting secure productivity in everyday business operations, while reducing risks tied to SaaS integrations.
Building Robust Defenses Against Non-Human Identity Risks
Non-human identities often fall into the cracks between traditional identity management systems and SaaS application environments. Without proper oversight, these identities can quickly accumulate, with service accounts or integration keys being granted broad access across systems. Solutions must focus on addressing this challenge from multiple angles:
The reliance on third-party integrations’ non-human identities necessitates a shift in how we approach SaaS security. Some recommendations include:
- Visibility and Discovery: The first step in securing non-human identities is identifying and mapping out where they exist within the SaaS ecosystem. Organizations need tools that can automatically detect these identities and catalog their associated permissions.
- Lead with Least Privilege: Just like with human users, the principle of least privilege should apply to NHIs. Grant only the minimum access required for each NHI to function.
- Focus On Lifecycle Management: Ensure unnecessary access of vendors with API and service accounts access is promptly removed upon termination—leverage automated tools to enforce such removal.
- Vet Third-Party Vendors: Conduct rigorous assessments of vendors behind SaaS-to-SaaS integrations. Inquire about their security practices, data handling procedures, access controls, and incident response protocols. Prioritize vendors with a proven track record of security hygiene.
- Continuous Monitoring: Regularly monitor NHI activity for suspicious behavior. Security teams should implement robust SaaS Security Posture Management (SSPM) practices to detect misconfiguration and configuration drift related to NHIs as well as SaaS Identity Threat Detection and Response (ITDR) capabilities to detect abnormal behavior which could potentially indicate a security incident. Failing to manage these machine identities exposes organizations to significant SaaS risks such as data breaches and unauthorized access.
- Educate and Empower: Foster open communication between security teams, SaaS administrators, and business users. Create clear security policies and work with the business units to ensure they properly enable the business, while keeping the data secure, including proper management of NHIs.
How Valence Helps Secure Non-Human Identities
Valence provides a powerful solution for managing the growing security risks associated with non-human identities across SaaS applications. By offering comprehensive visibility into NHIs, SaaS-to-SaaS integrations, and their access privileges, Valence enables organizations to reduce their SaaS security risks and implement an effective SaaS Security Posture Management strategy.
Valence’s platform identifies over-privileged, inactive, or risky NHIs within SaaS-to-SaaS integrations, ensuring access controls adhere to the principle of least privilege. Through automated insights and real-time monitoring, Valence detects and mitigates risks before they lead to a breach, safeguarding your organization’s SaaS data security.
By collaborating with SaaS admins and business users, Valence also provides the context needed to properly manage and remediate security gaps within these critical integrations. A great example of this is how Lionbridge leveraged Valence to streamline its security processes around NHIs. Using Valence’s remediation workflows, the company was able to revoke 95% of obsolete or inactive tokens almost immediately. Notably, more than 20% of these tokens were revoked directly by business users with guidance provided through Valence’s platform. Business users provided justification for an additional 5% of tokens, and 75% were automatically revoked after the security team deemed them obsolete.
With Valence, your organization can:
- Gain comprehensive visibility into NHIs across your SaaS applications
- Identify and remediate over-privileged, inactive, or risky integrations
- Reduce your organization's attack surface and improve overall SaaS security
- Collaborate effectively with SaaS admins and business users
Ready to see how Valence can help your team manage non-human-identity risk in SaaS applications? Schedule a demo!
Elevating SaaS Security Posture Management: Key Strategies

SaaS applications such as Google Workspace, Microsoft 365, Salesforce, Slack, GitHub, and others have become essential to modern business operations. While these tools drive collaboration and productivity, they also introduce unique security challenges. The complexity of managing distributed SaaS environments—often administered by multiple business units without centralized IT oversight—further complicates securing these applications.
This decentralized ownership model makes SaaS configuration management a significant challenge, leaving room for misconfigurations, excessive permissions, and risky integrations. To address these issues, SaaS Security Posture Management (SSPM) has emerged as a critical solution for organizations aiming to mitigate SaaS risks and protect their sensitive data.
What is SaaS Security Posture Management (SSPM)?
SaaS Security Posture Management (SSPM) involves the continuous monitoring, analysis, and remediation of security risks across SaaS applications. It helps organizations identify risks such as misconfigurations, overprivileged accounts, weak authentication, risky SaaS-to-SaaS integrations, and excessive data sharing.
By automating the discovery and remediation of these risks, SSPM empowers security teams to enforce best practices and maintain compliance without the burden of manual oversight. Following SSPM best practices ensures a proactive approach to securing these critical business tools.
Why SaaS Security Demands Extra Vigilance
Today’s businesses rely on both mission-critical SaaS applications (e.g., Microsoft 365, Google Workspace, Salesforce, ServiceNow) and secondary SaaS tools (including many GenAI tools) adopted by specific teams or individuals. The increased adoption of these tools, the realization, including at the Board level, that businesses “run on SaaS”, combined with the various SaaS risks that could create data exposure—all of these have led to a prioritization of SaaS security in recent years.
The Risks in SaaS Environments
Even with strong security measures like Multi-Factor Authentication (MFA) and Single Sign-On (SSO), SaaS applications remain vulnerable to various risks:
- Misconfigurations: Improper settings, such as inactive account permissions or overly permissive data sharing, can expose sensitive information.
- Overprivileged Accounts: Users and roles often retain excessive permissions, violating the Principle of Least Privilege.
- SaaS-to-SaaS Integrations: Core SaaS applications frequently integrate with other applications through OAuth tokens, APIs, and service accounts. These non-human identities are critical for automation and workflows but can become a security liability if unmanaged or tied to inactive accounts.
- Fragmented Visibility for Security Teams: Different business units often manage their own SaaS tools, leading to inconsistent security configurations and limited visibility for central security teams.
Given these challenges, SSPM solutions are essential for organizations seeking to secure their SaaS ecosystems comprehensively.
Key Strategies to Elevate SaaS Security Posture
1. Gain Comprehensive Visibility
The first step to improving your SaaS security posture is achieving complete visibility across all applications. SSPM solutions help uncover both mission-critical applications like Salesforce and secondary tools adopted by specific teams. This includes mapping SaaS-to-SaaS integrations and identifying non-human identities, such as service accounts and unused OAuth tokens.
Comprehensive visibility enables organizations to:
- Detect misconfigurations and risky integrations.
- Monitor dormant accounts and permissions.
- Understand how third-party apps interact with sensitive data in platforms like Google Workspace and Microsoft 365.
2. Automate Risk Remediation
Manual remediation of SaaS risks is time-intensive and often impractical, especially in decentralized environments. Automation is key to keeping pace with the scale and speed of SaaS adoption.
With SSPM, security teams can:
- Revoke excessive permissions and deactivate unused service accounts.
- Eliminate risky open-sharing settings, such as public document links in Google Drive or SharePoint.
- Address orphaned OAuth tokens from inactive accounts to minimize exposure.
Automation ensures consistent enforcement of security policies without disrupting business workflows.
3. Secure SaaS-to-SaaS Integrations
SaaS ecosystems thrive on integrations that enhance productivity. However, these integrations also expand the attack surface. Platforms like GitHub, Slack, and Atlassian often connect to other tools via APIs, OAuth tokens, or direct integrations.
Effective SSPM strategies for managing SaaS-to-SaaS integrations include:
- Identifying and removing inactive or unnecessary integrations.
- Auditing all integrations to ensure they meet security standards.
- Continuously monitoring non-human identities for signs of compromise.
4. Address the Complexity of SaaS Configurations
SaaS applications offer a vast array of features and settings, many of which can create security risks if misconfigured. For example, ServiceNow may have default configurations that allow excessive external access, or Slack may retain inactive workspaces that still store sensitive messages.
Given the distributed ownership of these applications, security teams often struggle to track and standardize configurations across multiple platforms. SSPM simplifies this by:
- Providing a unified view of all security settings across SaaS tools.
- Highlighting misconfigurations that deviate from best practices.
- Offering tailored recommendations to remediate risks effectively.
5. Enforce the Principle of Least Privilege
Overprivileged accounts are a common problem in SaaS environments. Employees or service accounts often retain access to tools they no longer need, creating unnecessary risk.
SSPM solutions can enforce least privilege access by:
- Identifying accounts with excessive permissions in tools like Salesforce and GitHub.
- Automatically downgrading roles or revoking unnecessary access.
- Implementing workflows for business owners to justify exceptions.
The Business Case for SSPM
As businesses continue to adopt SaaS applications at scale, the risks associated with these tools will only grow. High-profile breaches have shown that SaaS misconfigurations and insecure integrations can lead to devastating consequences, from data theft to operational disruptions.
An SSPM solution addresses these challenges by:
- Streamlining SaaS Security Management: Centralizing visibility and control over applications like Microsoft 365, Slack, and Atlassian.
- Reducing Risks from Non-Human Identities: Managing OAuth tokens, APIs, and service accounts tied to integrations.
- Enhancing Operational Efficiency: Automating the identification and remediation of risks without adding to the workload of security teams.
Selecting the right SSPM tools is critical to addressing SaaS risks effectively. When evaluating SSPM vendors, organizations should consider both the depth and breath of application coverage, the level of risk remediation capabilities (beyond only ticketing and a list of manual steps to include automation), scalability, compatibility with your existing security stack, and more.
Valence Security stands out as a leading SaaS security platform with extensive SSPM functionality, offering unmatched capabilities in securing SaaS environments. By simplifying SSPM security, Valence provides the tools and expertise needed to protect your SaaS ecosystem.
Start Elevating Your SaaS Security Today
The complexity and distributed ownership of SaaS environments demand a proactive approach to security. By investing in SSPM, organizations can reduce risks, improve compliance, and protect sensitive data across their SaaS ecosystem.
Ready to take control of your SaaS security? Check out our SSPM Checklist or request a demo to learn how Valence Security can help secure your SaaS environment.
2024 SaaS Security Breaches: Lessons Learned

As 2024 draws to a close, it's evident that the SaaS landscape has become both a cornerstone of business productivity and a growing target for sophisticated cyberattacks. This year’s high-profile breaches underscore the importance of robust SaaS security strategies to protect human and non-human identities, secure SaaS-hosted data, detect misconfigurations, and monitor SaaS audit logs for potential signs of breach attempts.
What’s a SaaS Data Breach?
A SaaS data breach occurs when unauthorized entities exploit security gaps within SaaS platforms to access sensitive information. These breaches can result from misconfigurations, compromised credentials, insecure third-party integrations, risky data sharing, or other causes. The 2024 SaaS breaches we’ve observed highlight how quickly attackers can exploit even minor security lapses to cause significant harm.
Below, we explore five significant SaaS breaches from 2024 and the critical lessons security teams can take away to better protect their SaaS ecosystems.

1. Microsoft Midnight Blizzard Breach: A Wake-Up Call for Holistic SaaS Security
In January 2024, the nation-state actor Midnight Blizzard exploited a series of misconfigurations within Microsoft’s environment to breach sensitive company emails.
The attackers initiated the breach with a password spray attack on a human account lacking multi-factor authentication (MFA), gaining access to a non-production Microsoft 365 test tenant. They exploited a legacy OAuth application—an unmanaged non-human identity—with full privileges to access Microsoft’s production environment. To extend their foothold, they created additional malicious OAuth applications and granted them access using newly created user accounts. The threat actors authenticated to Exchange Online, targeting corporate email accounts while obfuscating their activity through residential proxy networks, using legitimate user IP addresses to mask their actions.
Impact: The emails accessed include the corporate email accounts of Microsoft’s senior leadership, cybersecurity, and legal teams. Sensitive emails and attached documents were exfiltrated, including high-value corporate communications likely linked to business strategies and legal matters. In a followup update posted in May, Microsoft wrote that “In recent weeks, we have seen evidence that Midnight Blizzard is using information initially exfiltrated from our corporate email systems to gain, or attempt to gain, unauthorized access. This has included access to some of the company’s source code repositories and internal systems. To date we have found no evidence that Microsoft-hosted customer-facing systems have been compromised.”
Key Lessons Learned:
- Prioritize MFA Everywhere: Human accounts without MFA remain low-hanging fruit for attackers. A "default to MFA" approach should be applied across all human identities.
- Audit Non-Human Identities: Legacy applications and tokens often go unnoticed but can provide attackers with privileged access. Regular audits to identify unused or overly permissive non-human identities are crucial.
Remove Dormant Resources: Dormant accounts, inactive data shares, and unused tokens are not benign. Security teams must proactively remove unnecessary resources to shrink the attack surface.

2. Cloudflare’s Atlassian Breach: Supply Chain Risks in SaaS
After a previous Okta breach in October 2023, attackers leveraged compromised credentials to breach Cloudflare’s Atlassian platforms (Bitbucket, Confluence, and Jira), gaining access to sensitive data, including source code.
Leveraging credentials leaked during the Okta compromise, the attackers exploited overlooked service tokens and service account credentials tied to SaaS applications, including one that granted the application Smartsheet administrative access to Cloudflare's Atlassian systems. While Cloudflare's security team conducted a comprehensive forensic analysis and rotated over 5,000 production credentials, four critical credentials tied to service tokens and SaaS integrations were overlooked, providing attackers with a pathway to escalate their access.
Key Lessons Learned:
- Enforce Privilege Management: Service accounts should follow the principle of least privilege, ensuring they only have access necessary for their tasks.
- Strengthen Third-Party Integrations: Connections between SaaS platforms should be carefully managed, and privileges reviewed frequently.
Automate Credential Rotation: Manual credential management can miss critical gaps. Automated processes for credential rotation and deprovisioning are essential to minimize risk.

3. Snowflake Customer Breaches: The Importance of Shared Responsibility
This attack campaign targeted customers of Snowflake, including AT&T, Santander Bank, and Ticketmaster. While initial reports suggested a breach in Snowflake’s infrastructure due to a vulnerability, it was later clarified that the breaches were due to customer-side issues, mainly the lack of enforced MFA, allowing access with just a username and password and leaving them vulnerable to dictionary or password spray attacks.
Impact: These incidents exposed sensitive data and severely impacted customer trust and operational security:
- AT&T - Over 109 million customer call and text records were leaked, including metadata and detailed logs, in one of the largest telecom data breaches in history
- Santander Bank - Personal information for more than 12,000 U.S.-based employees, including Social Security numbers and payroll bank account details, was exfiltrated
- Ticketmaster - Millions of customer records, including names, contact information, and additional sensitive data, were stolen
Attack Method: Snowflake clarified that its platform was not compromised. Instead, attackers exploited customer-managed accounts with weak security configurations, including:
- Stolen Credentials: Many accounts relied on single-factor authentication, allowing attackers to leverage compromised passwords to gain access
- Misconfigured Permissions: Some accounts were overly permissive, granting broad access to sensitive databases
“We have not identified evidence suggesting this activity was caused by a vulnerability, misconfiguration, or breach of Snowflake’s platform…This appears to be a targeted campaign directed at users with single-factor authentication.” — Joint statement by Snowflake, CrowdStrike, and Mandiant
Snowflake later announced in response to the attack campaign that MFA will be mandatory for all new Snowflake human users starting in October 2024.
Key Lessons Learned:
- Understand the Shared Responsibility Model: SaaS providers are responsible for securing the application infrastructure, but customers must enforce strong security configurations, including MFA, privilege management, and strong data security practice. Read more about the Shared Responsibility Model in SaaS Security.
- Regular Configuration Audits: Misconfigurations are a leading cause of breaches. Implement continuous monitoring to detect and remediate risky configurations.
- Configuration Management is Complex: The complexity of managing security across multiple SaaS applications highlights the need for specialized SaaS posture management capabilities to identify misconfigurations and enforce security best practices. The Snowflake breaches—impacting large enterprises with mature cybersecurity teams— emphasizes that even when a provider's platform is secure, improperly managed customer environments can still lead to devastating consequences.

4. Dropbox Sign Breach: Non-Human Identities Under Fire
In April, attackers breached Dropbox Sign, compromising sensitive customer data and exposing security challenges in securing non-human identities (NHIs) like service accounts, API keys and OAuth tokens.
Attack Method: The attackers gained unauthorized access to an automated system configuration tool within Dropbox Sign’s backend. They compromised a service account with elevated privileges, enabling access to the customer database. Mismanagement of this non-human identity was a key factor in the breach:
- Exploitation of Privileges: The service account's broad access permissions allowed attackers to reach sensitive systems.
- Weak NHI Protections: Insufficient authentication and monitoring for the compromised account facilitated unauthorized access.
Dropbox has since reset user passwords, logged out all Dropbox Sign users, and initiated a full rotation of API keys and OAuth tokens to mitigate further risks.
Impact: The breach affected all users of Dropbox Sign and even third parties who signed documents but never created accounts.
- Stolen Data: The attackers accessed a wide array of information, including:some text
- For all users: Emails, usernames, and general account settings.
- For subsets of users: Phone numbers, hashed passwords, API keys, OAuth tokens, and even multi-factor authentication (MFA) information.
- For third parties: Names and email addresses of individuals who signed documents but were not registered Dropbox Sign users.
While no evidence suggests that attackers accessed document contents, templates, or payment information, the breach exposed a trove of metadata critical to both personal and organizational security.
Key Lessons Learned:
- Enhance NHI Security: Non-human identities, such as service accounts and API tokens, should be protected with strong authentication measures, including conditional access policies and periodic rotation.
- Monitor SaaS Audit Logs: Detailed monitoring can provide early warning signs of malicious activity involving NHIs or unauthorized data access.
Proactively Decommission Resources: Expired or unused OAuth tokens must be automatically revoked to prevent exploitation by attackers.

5. Internet Archive Breach: Stolen Tokens Strike Again
The Internet Archive suffered two breaches within a two-week span, both stemming from compromised access tokens. Attackers exploited an exposed GitLab authentication token to access sensitive source code, user databases, and additional credentials, including API tokens for the organization’s Zendesk support system.
- First Breach: Involved stolen GitLab tokens exposed in a configuration file since December 2022. The attackers used this to steal user data from 33 million accounts, download 7TB of source code and related files, and even modify site functionality.
- Second Breach: Leveraged the unrotated Zendesk API token, granting access to 800,000+ support tickets dating back to 2018. Many tickets contained sensitive information, such as uploaded personal identification documents submitted for page removal requests from the Wayback Machine.
Key Lessons Learned:
- Secure Tokens at Every Stage: Token management must include encryption, secure storage, and periodic rotation to mitigate risk.
- Implement Zero Trust Principles: Assume all access attempts could be malicious, verifying user and token legitimacy for each request.
- Regular Forensic Reviews: Post-breach analysis should extend to related tokens and accounts to uncover any lingering vulnerabilities.
Key Themes from 2024 SaaS Breaches
- Configuration Management is Non-Negotiable
Misconfigurations, often overlooked, remain a top vector for attacks. Automated tools can help security teams maintain compliance with SaaS security best practices. - Non-Human Identities are a Major Threat Vector
As breaches targeting NHIs like OAuth tokens and API keys increase, robust identity governance must extend beyond human users. - Shared Responsibility Requires Shared Accountability
SaaS providers and customers must collaborate to enforce a strong security posture. Customers must be vigilant in securing their environments while leveraging the tools and guidance provided by SaaS vendors. - Proactive Monitoring and Threat Detection are Crucial
Monitoring SaaS audit logs for anomalous activity and implementing threat detection mechanisms are essential to mitigate evolving risks.
The Path Forward: Securing SaaS in 2025
As organizations expand their SaaS usage, the attack surface grows. Security teams must adopt a comprehensive SaaS security strategy that includes:
- Continuous monitoring and automated remediation of misconfigurations.
- Robust identity governance for human and non-human identities
- Least-privilege access controls and regular reviews of privileges
- Enhanced token and credential management
- Employee training on SaaS security best practices
The breaches of 2024 serve as a stark reminder of the dynamic SaaS threat landscape. By learning from these incidents, organizations can strengthen their defenses and build resilient SaaS ecosystems for the challenges of 2025 and beyond.
Explore How Valence Can Help Secure Your SaaS Applications
The 2024 SaaS breaches underscore the growing complexity of securing modern SaaS environments. Valence Security empowers organizations to address these challenges head-on, offering tools to uncover misconfigurations, manage non-human identities, and enforce security best practices across your SaaS ecosystem.
Request a demo and see how Valence can help you identify risks, simplify remediation, and build a more resilient SaaS security posture for 2025 and beyond.
SSPM and DSPM Better Together—Enriching SaaS Security Risk Management with Cyera’s Data Security Platform Classification and Contextualization

As organizations rely more on SaaS applications to store sensitive data, the security stakes have never been higher. Beyond file storage in platforms like Google Drive or OneDrive, SaaS applications also house a wide range of sensitive data: meeting records in Zoom, private communications in Slack, legal documents in Docusign, source code in GitHub, customer personally identifiable information (PII) in Salesforce, financial data in NetSuite, and much more.
These applications offer a range of data-sharing functionalities, enabling users to share data both internally and externally or connect it to other third-party applications through integrations. With these capabilities, however, comes a heightened risk landscape that requires vigilant data security.
To address these risks, Valence is excited to announce a new integration with Cyera, a leader in Data Security Posture Management (DSPM). By combining Valence’s SaaS Security Posture Management (SSPM) capabilities with Cyera’s insights around sensitive data, we’re empowering security teams to manage SaaS security with greater context and precision.
What is Data Security Posture Management (DSPM)?
Data Security Posture Management is a modern approach to securing sensitive information in the cloud. Introduced as a formal category by Gartner in 2022, DSPM solutions were developed to meet the unique needs of cloud-native environments and address the limitations of legacy data security tools. DSPM identifies, classifies, and assesses risks associated with sensitive data—such as personally identifiable information (PII), personal health information (PHI), financial records, intellectual property, and more—while offering insights into security and compliance challenges.
One of Cyera’s Data Security Platform’s core capabilities is its DSPM engine, which classifies and monitors sensitive data across various environments, including cloud-based and SaaS applications. Cyera’s support of SaaS applications, in which some of the most sensitive data is stored like Google Workspace, Microsoft 365, Salesforce, and Box, among others, enables security teams to quickly identify and understand where sensitive information, like PII and financial data, resides within their SaaS environments.
Data Security Challenges in SaaS
Data security is complex. Traditional data loss prevention (DLP) solutions were primarily designed for on-premises environments, and not for the cloud. In fact, Cyera’s 2024 DSPM Adoption Report reveals that 87% of organizations find their current data discovery and classification tools inadequate, underscoring a significant gap in visibility and control over sensitive information.
SaaS applications present distinct security challenges due to distributed ownership and complex permissions. Risks of data exposure rise sharply when misconfigurations occur alongside sensitive data shares, excessive privileges, or overly-permissive SaaS-to-SaaS integrations—risks that often go undetected without comprehensive visibility into both the SaaS environment and associated sensitive data.
Consider these real-world cases of sensitive data exposure through SaaS misconfigurations:
- Ateam’s Google Drive Misconfiguration - Japanese game developer Ateam inadvertently left sensitive data of nearly one million individuals exposed for over six years due to a Google Drive setting configured to "Anyone with the link." This setting essentially removed access controls, allowing open internet access to files containing names, emails, phone numbers, and customer management numbers, available to anyone who found the link.
- Microsoft’s Midnight Blizzard Breach - Attackers exploited multiple misconfigurations in Microsoft 365, leveraging an unprotected test tenant lacking MFA. From there, they accessed an OAuth token with elevated privileges, granting access to corporate mailboxes. The attackers then created additional malicious OAuth apps to escalate access within Microsoft’s corporate environment, a “toxic” attack chain that enabled deep infiltration.
Valence’s integration with Cyera provides CISOs with a consolidated view to assess and remediate these risks across SaaS applications. By integrating Cyera’s DSPM capabilities into Valence’s SaaS Security platform, Valence customers can close these security gaps, delivering a more holistic and proactive approach to SaaS security.
Enriching SaaS Security with Data Context Through Cyera Integration
The integration with Cyera brings critical data security context and classification to the Valence platform, allowing organizations to manage SaaS security more effectively by correlating data sensitivity with SaaS risk posture. With Cyera’s data classification insights seamlessly integrated into Valence, customers can now identify, assess, and prioritize SaaS risks with enriched data visibility. Key benefits of this integration include:
1. Enhanced SaaS Risk Scoring with Data Sensitivity Context
Valence’s SSPM capabilities provide risk scoring for each SaaS application risk, allowing security teams to prioritize and address the most critical first. With the Cyera integration, these risk scores are enriched with data sensitivity insights. Valence can now analyze the sensitivity of data exposed through various risk points—including external data shares, inactive or over-entitled accounts, high-privilege third-party integrations, and weak authentication. By correlating the data sensitivity with the exposure level, security teams can focus their efforts on the highest-risk assets.

2. Advanced Risk Remediation for Data Misconfigurations in SaaS
Valence’s platform delivers a range of powerful remediation options, from automated workflows to guided, user-driven actions, allowing organizations to address sensitive data risks across their SaaS applications with precision. With the additional data context from Cyera, Valence enables users to take remediation actions on SaaS sensitive data risks directly from the Valence platform. For example, files containing PII shared externally via Google Drive or OneDrive can be flagged and automatically revoked if they remain inactive or shared with unauthorized users for over an extended period (e.g., 60 days). Additionally, Valence provides guided remediation steps, direct one-click fixes within the platform, and collaboration tools to engage business users when necessary, ensuring that security teams have the flexibility to address risks effectively without manual intervention in each SaaS application.

3. Enhanced Identity Threat Detection and Response (ITDR) for Sensitive Data Protection
Beyond preemptively remediating risks, Valence excels at detecting real-time threats. With the more enhanced sensitive data risk context, Valence’s ability to monitor and detect suspicious activities within SaaS environments becomes even more impactful. By combining Cyera’s data sensitivity insights with Valence’s identity monitoring, organizations can detect anomalous behaviors—such as privilege escalation attempts, excessive permissions granted to OAuth tokens, or high-volume, high-frequency data-sharing activities. This enables security teams to identify potential data breach attempts and address threats proactively, protecting sensitive information.
For both current Valence customers and those considering SSPM or SaaS security solutions, the Cyera integration represents a powerful addition to Valence’s platform, strengthening its capabilities and addressing the gaps commonly found in non-integrated traditional security solutions.
As SaaS adoption continues to grow, so do the challenges of securing sensitive data in the cloud. Valence’s integration with Cyera empowers security teams to safeguard sensitive information in SaaS environments with unmatched precision and efficiency.
To see the Valence-Cyera integration in action, schedule a demo today.
Escape the SaaS House of Horrors

It’s the height of spooky season, and there’s no better time to talk about the spine-chilling risks lurking in your SaaS environment. But don’t worry—you don’t have to let these spooky threats turn your business into a haunted house. Let’s shine a light on these hidden dangers and share practical tips to keep your SaaS ecosystem safe from the horrors of misconfigurations, weak visibility, and risky external data shares. Get ready for a survival guide that will help you navigate through these spooky threats and emerge unscathed!
The Ghosts of Misconfigurations Past 👻
Just like the ghost stories that send shivers down your spine, SaaS misconfigurations can haunt your environment without you even knowing it. Improper permissions or unmonitored security configurations can lead to unauthorized access, compliance violations, and massive data leaks. These “invisible ghosts” may be lying in wait, just one oversight away from unleashing chaos. It’s no wonder that 43% of security leaders cite SaaS configuration complexity as a top challenge - SaaS platforms have grown more complex over time, making them a fertile ground for potential missteps.
Tip: Regularly audit your SaaS security posture to identify and fix misconfigurations before they become a threat. Use SSPM capabilities to automate these checks across all your applications and ensure compliance with industry standards and best practices.

Beware the Monsters of Fragmented SaaS Visibility 🧟♂️
Think of fragmented visibility in SaaS environments as a lurking monster—hidden in the shadows and waiting to pounce. With SaaS tools owned and administered by different business units (think Sales managing Salesforce, HR managing Workday), your IT and security teams are left in the dark. In fact, half of security executives identify this distributed ownership as one of their top SaaS security challenges. Without centralized control, securing configurations and managing data access becomes a nightmare. These risks open the door to misconfigurations and security blind spots that could haunt you and your business for years. It’s time to tame the monster of fragmented ownership before it grows into an even bigger threat.
Tip: Set up a centralized process for visibility and control over all SaaS applications. Foster open communication between security teams and non-security SaaS admins to coordinate security measures and current risks, and share educational messages with business users about SaaS security best practices.

The Tangled Web of SaaS-to-SaaS Connections 🕸️🕷️
As your business expands its SaaS footprint, the web of SaaS-to-SaaS integrations grows too—just like a spider's web. While these integrations can streamline workflows, they can also become weak points that attackers can exploit. Unmonitored, overly privileged or dormant integrations may open backdoors, leading to breaches. The recent Microsoft Midnight Blizzard breach is a prime example: one of the primary attack vectors were the non-human identities that power these integrations. Attackers abused a legacy test OAuth application with full access to mailboxes and to read emails, then created additional malicious OAuth applications and granted them access to Microsoft’s corporate environment. Just like a spider carefully maintains its web, you need to keep a close eye on these connections to ensure they don’t become gateways for malicious activity. Who’s crawling through your web of integrations unnoticed?
Tip: Regularly review and audit all SaaS-to-SaaS integrations to avoid dormant or overly privileged connections. Consider mapping all integrations and setting policies for regularly assessing and revoking unused connections.

Masked Identity Risks in SaaS 🎭🧛♀️
In a crowded costume party, it’s hard to tell who’s really behind the mask—and your SaaS environment is no different. Mismanaged identities and weak identity controls can allow attackers to masquerade as legitimate users. Without strong enforcement of MFA and SSO, it’s easy for these "masked figures" to blend in, steal credentials, and escalate their privileges, as seen in the Snowflake customer breaches. Once inside, they can cause chaos by accessing sensitive data unnoticed. Proper lifecycle management of your SaaS identities and enforcing MFA/SSO are essential to unmask these threats before they slip past your defenses.
Tip: Strengthen your SaaS Identity security by enforcing MFA and SSO across all applications. Ensure proper lifecycle management for all identities to prevent attackers from exploiting dormant or under-secured accounts.

The Horror of External Data Shares Gone Wrong 💀
One of the scariest risks in SaaS security is the uncontrolled sprawl of external data shares. Just like opening your door to trick-or-treaters, you never know who might get inside. Sometimes, it’s giving the keys to enable “anyone with the link” to view sensitive data—as in the Ateam Google Drive misconfiguration that left sensitive data exposed—or perhaps it’s shared with private, non-corporate emails. Furthermore, If external file shares go unmonitored or dormant links remain accessible, sensitive information could fall into the wrong hands, leading to serious exposure risks.
Tip: Monitor external data shares regularly, setting expiration dates on links and using tools to detect and clean up dormant shares. Establish policies to keep sensitive data under control, whether that’s limiting access or restricting sharing outside corporate domains.

How to Avoid a SaaS Horror Story 🔐
The good news? These spooky threats don’t have to keep you up at night. With the Valence SaaS Security Platform, you can detect and address misconfigurations, strengthen visibility across SaaS applications, govern SaaS-to-SaaS connections, and eliminate risky external data shares—all before they turn into nightmares.
Here’s how Valence can help you fight off the frights:
- SaaS Configuration Management: Continuously analyze and enforce security configurations to detect misconfigurations and ensure compliance with best practices.
- SaaS Identity Security: Protect your business from identity-based threats by ensuring proper lifecycle management of SaaS identities, enforcing MFA/SSO, and managing privileges across all SaaS apps.
- SaaS-to-SaaS Integration Governance: Govern third-party integrations and service accounts to ensure that no dormant or risky connections can sneak in through the cracks.
- SaaS Data Protection: Secure your data by automating the identification and elimination of risky external data shares, so you’re always in control of who has access to your most sensitive information.
- SaaS Threat Detection: Monitor both human and non-human identities, detect suspicious behavior, and identify potential threats before they escalate.
Don’t Let Your SaaS Security Turn Into a Horror Show! 🎃
This Halloween, don’t let hidden risks haunt your business. With Valence’s powerful SaaS Security Platform, you can banish the ghosts, monsters, and masked threats in your SaaS environment—turning your security story from a nightmare into a success.
Ready to stop the scary threats in your SaaS environment?
Let Valence help you exorcise those risks and safeguard your data—book a demo today!

Lifecycle Management in SaaS Security: Navigating the Challenges and Risks

The rapid rise of Software-as-a-Service (SaaS) has transformed business operations, offering unprecedented flexibility and scalability. However, this shift brings its own set of security challenges, particularly when it comes to managing the lifecycle of SaaS applications and their associated resources such as identities. Effective lifecycle management is crucial in safeguarding against threats and ensuring that security measures keep pace with the evolving landscape of SaaS.
This blog post delves into the key challenges of account deprovisioning, dormant SaaS-to-SaaS integrations and non-human identities, and unused but still available external data shares, and explores how Valence Security can help alleviate these challenges and strengthen your SaaS security posture.
The Importance of Lifecycle Management in SaaS Security
Lifecycle management encompasses the entire span of an application's existence, from initial deployment to eventual decommissioning. In the context of SaaS security, it involves managing user access, integrations, and data sharing throughout their lifecycle. Poor lifecycle management can leave organizations exposed to significant security risks, including unauthorized access, data breaches, and compliance violations.
A recent Gartner report stresses that lifecycle management in SaaS security simply cannot be ignored. Industry experts are increasingly emphasizing the critical nature of addressing lifecycle management comprehensively to prevent security gaps.
Challenges in SaaS Security Lifecycle Management
1. Account Deprovisioning and Offboarding
One of the most critical aspects of SaaS lifecycle management is timely account deprovisioning. The infamous 2020 Drizly data breach, where an attacker exploited an un-revoked GitHub account intended to be granted for one-day access from a 2018 hackathon, serves as a stark reminder of the consequences of lax offboarding practices. When employees or contractors leave an organization, their access to SaaS applications must be promptly revoked to prevent potential misuse. Despite the availability of automated offboarding processes, gaps often persist, and just offboarding from the corporate SSO is typically insufficient due to direct local access granted in SaaS applications.
According to the 2024 State of SaaS Security report, 93% of security teams claim to have automated processes for offboarding ex-employees and contractors. However, data reveals a different reality: In platforms like Google Workspace, about 6% of accounts remain inactive without any recent logins, and 4% of these have admin privileges. This creates a window of opportunity for attackers to exploit dormant accounts.
A significant challenge in this area is managing "Shadow IAM," which refers to unmanaged or local accounts that are not linked to the company's Single Sign-On (SSO) system or identity provider (IdP). When users create accounts directly within SaaS applications without going through SSO, these accounts can remain unmanaged if the IT team focuses only on accounts tied to the corporate IdP. Consequently, when an employee is offboarded, their SSO-linked accounts may be deactivated, but these unmanaged, local accounts can be left untouched. This oversight can create security risks, as these accounts, which may retain access privileges, remain active and unmonitored.
2. Inactive Non-Human Identities
Non-human identities, such as service accounts and API keys, play a vital role in integrating various SaaS applications. However, inactive or unused non-human identities can pose serious security risks. The 2024 State of SaaS Security report highlights that 65% of integrations in platforms like Microsoft 365 are inactive but still hold valid API keys or OAuth tokens. These forgotten integrations often become entry points for attackers.
In the Cloudflare breach publicized in February 2024, attackers exploited overlooked service tokens and accounts that were compromised during a previous Okta breach. Despite rotating more than 5,000 production credentials and performing an in-depth forensic analysis, the Cloudflare security team missed one service token and three service accounts that were presumed to be unused. This oversight, involving only four out of 5,000+ credentials, ultimately contributed to the breach, illustrating that every credential counts in maintaining security.
Similarly, the Microsoft Midnight Blizzard attack further exemplifies the risks associated with unmanaged non-human identities. AAmong the numerous attack vectors, attackers exploited a legacy test OAuth application—a non-human identity—that had full access to Microsoft’s corporate production Microsoft 365 tenant, including the ability to read emails. This demonstrates how even outdated or seemingly benign non-human identities can become significant security liabilities if not properly managed.
Inactive integrations often result from failed Proofs of Concept (PoCs). When organizations trial new SaaS solutions, they grant temporary access which, if not properly decommissioned, can leave lingering vulnerabilities. Managing and auditing these integrations is crucial to prevent unauthorized access and potential breaches.
Additionally, some security teams might offboard a SaaS user or former employee but fail to disable OAuth tokens or third-party integrations set up by the user. These overlooked integrations can continue to provide access, posing significant security risks if not properly addressed.
3. Inactive and Unused External Data Shares
External data sharing is a common feature in SaaS applications, enabling collaboration and information exchange. However, it also presents risks if not managed properly. We all have shared files, folders, and recordings, but rarely do we ever “unshare that file” beyond the time it’s needed. The 2024 State of SaaS Security report reveals that a staggering 94% of external data shares are inactive, with no recent access by external users. Additionally, 22% of these shares utilize open links, exposing sensitive information to anyone with the link.
Inactive external shares can pose significant security risks. For instance, a misconfigured Google Drive folder exposed personal data of nearly one million individuals. Ensuring that external data shares are regularly reviewed and deactivated when no longer needed is crucial for maintaining data security.
How Valence Security Can Enhance SaaS Lifecycle Management
Effective lifecycle management requires a comprehensive approach to identify and mitigate risks associated with inactive accounts, dormant integrations, and unsecured data shares. Valence Security, a recognized Leader in SaaS Security Posture Management (SSPM) capabilities, offers a robust solution to address these challenges and enhance your SaaS security posture.
1. Comprehensive User Offboarding
Valence Security streamlines the user offboarding process by identifying and eliminating security risks associated with inactive accounts and over-privileged users. Our platform detects unmanaged identities, including those not tied to corporate SSO, and ensures that access privileges are updated or revoked as needed.
As a centralized SaaS security platform, Valence is also able to correlate identity information from multiple sources, including SSO, productivity suites, HR, and business applications. This comprehensive view helps identify issues in the offboarding process and ensures a more secure user lifecycle.
In addition, Valence empowers security teams with automated offboarding workflows, including policy creation that instructs if a human account has been offboarded, then to disable all non-human identities (OAuth tokens, API keys) or external data shares created by that account. These automation capabilities, combined with visibility into account access and privileges, help organizations reduce the risks of unauthorized access, account takeover and unnecessary data exposure.
2. Managing Non-Human Identities and Integrations
Valence Security helps organizations manage non-human identities and integrations effectively. Valence tracks and identifies and remediates dormant integrations, ensuring that obsolete API keys and OAuth tokens are promptly deactivated. Valence provides both guided and automated remediation, including the ability to automatically communicate with business users to clarify if there is a necessary reason for the integrations.
Read how Lionbridge revoked 95% of inactive tokens without any manual effort.
By integrating with over 60 business-critical SaaS platforms, Valence provides visibility into integrations and facilitates their secure management.
3. Reducing Risk from External Data Shares
Valence simplifies the management of external data shares by identifying and analyzing shared data across various platforms. Our platform helps organizations identify inactive shares, assess their risk levels, and remove or notify share owners about unused shares. By providing continuous monitoring and automated cleanup, Valence reduces the risk of data exposure and promotes secure sharing practices.
Conclusion
Lifecycle management in SaaS security is a critical component of maintaining a robust security posture. Challenges such as ineffective account deprovisioning, dormant non-human identities, unmanaged integrations, and inactive external data shares can create significant security risks. Valence Security offers comprehensive solutions to address these challenges, providing organizations with the tools needed to manage user access, integrations, and data sharing effectively.
By leveraging Valence’s advanced capabilities, organizations can enhance their SaaS security posture, reduce the attack surface, and user Identity Threat Detection and Response (ITDR) capabilities to protect sensitive data from potential threats. For a demonstration of how Valence can support your SaaS security lifecycle management, schedule a demo today.
Mastering SaaS lifecycle management is not just about preventing breaches; it’s about ensuring that your security measures evolve alongside your SaaS environment. With Valence Security, you can navigate these challenges with confidence and maintain a strong, secure SaaS infrastructure.
Why Application-Specific Passwords are a Security Risk in Google Workspace

The digital world is constantly changing, and with it, the methods used to secure sensitive information. Decisions made years ago continue to shape today’s landscape. The inception of Gmail by Google marked a pivotal moment in history, setting the foundation for the Google Account as we know it today. Unfortunately, the platform’s early choices still cast a shadow on today’s security posture for everyone who uses it.
This blog post will look at security risks of Application-Specific Passwords (ASPs) in Google Workspace and will provide security tips to address those risks, thereby strengthening Gologle Workspace security.
The Problem with Legacy Email Protocols (IMAP & POP3)
In the early days of email, protocols like IMAP and POP3 were the standard for accessing emails on external devices. While suitable at the time, these protocols rely solely on username and password for authentication, offering no support for modern Multi-Factor Authentication (MFA) methods. This creates a security gap as attackers only need a valid username and password to access a user's email. It also makes them susceptible to unauthorized access when used with cloud-hosted services.
Google named this concept "Less Secure Apps" (LSAs). LSAs are any applications that rely solely on username and password for access, bypassing Google's robust security measures like MFA. In fact, LSAs required you to share or reuse your own Google/Gmail password, against recommended security practices. Google plans to completely phase out support for LSAs by September 2024.
App-Specific Passwords (ASPs)
As a somewhat more secure alternative to LSA, to try and bridge the gap between the security demands of modern applications and the limitations of older systems, Google introduced App-Specific Passwords. These 16-character, high-entropy passwords were designed for a single application and offered an additional layer of security over traditional username/password combinations. However, while an improvement over LSAs, ASPs come with their own set of security risks.
Security Risks of Application-Specific Passwords
ASPs, while intended as a security enhancement, introduce several security risks that can compromise account security.
- MFA Is Not an Option - Unlike your Google Workplace account password now, ASPs bypass MFA entirely, leaving your account vulnerable if compromised.
- Limited Administrative Control - Google Workspace administrators cannot easily manage ASPs created by users, making it difficult to enforce security policies.
- Legacy Device Compatibility - ASPs are often used with outdated devices like "iPhone6" or "Blackberry," which may have weaker security protocols themselves.
- Brute Force Attacks - The fixed length (16 characters) and lack of special characters in ASPs make them more susceptible to brute-force attacks compared to stronger passwords.
- Increased Attack Surface: Each ASP represents an additional entry point for malicious actors. As the number of ASPs grows within an organization, so does the potential attack surface.
Security Tips: Securing and Moving Beyond ASPs
To address the challenges posed by ASPs, organizations should implement the following recommended practices:
- Enforce Strong Password Hygiene: If ASPs remain authorized in your SaaS environment, implement strict password policies. Discourage password reuse, enforce password rotation, and consider using password managers. ASPs, unlike standard passwords, do not typically undergo automatic rotation, increasing the risk of compromise over time.
That said, it’s best to move beyond ASPs into more modern authentication methods, which we’ll address now.
- Prioritize Modern Authentication: Transition to OAuth, API keys or similar authentication methods whenever possible. These methods offer granular control over data access, reducing the risk of unauthorized actions.
- Regular Security Audits: Conduct routine assessments to identify and revoke unused or suspicious ASPs. This involves:some text
- Checking Google Workspace Settings: Verify that "Less Secure App Access" is disabled to prevent unauthorized access through older applications.
- Scrutinizing ASP Usage: Analyze user accounts for excessive ASP creation or usage patterns that indicate potential risks. ASPs can be easily shared or copied, leading to unauthorized access. Additionally, dormant ASPs, those not used for extended periods, present a prime target for attackers and should be eliminated.
- Employee Education: Raise awareness about the risks associated with ASPs and the importance of following security best practices in Google and other Saas applications.
By combining these strategies, organizations can significantly reduce the likelihood of successful attacks targeting ASPs and protect sensitive data.
Valence Security: Your Partner in SaaS Security
Valence Security offers a comprehensive SaaS Security Platform that empowers organizations to navigate the complexities of securing their SaaS applications. Our platform provides real-time visibility into ASP usage, allowing you to identify and remediate ASP-related risks, and strengthen Google Workspace security.
We can identify existing ASPs, then create automated policies to revoke either all ASPs, or specifically target newly discovered ASPs, or inactive and dormant ASPs. Additionally, our solution facilitates automated collaboration with business users to gather justifications for retaining any ASPs, ensuring that only necessary and secure applications remain active.
Contact us today to learn how Valence Security can help you secure your Google Workspace environment (and that of other business-critical SaaS applications) and embrace a future-proof security posture.
Strengthening Your Third Party SaaS Risk Management with Valence and OneTrust

In today's interconnected world, SaaS applications play a critical role in facilitating business operations, enhancing collaboration, and connecting the global workforce. However, along with their myriad benefits come complexities, particularly in terms of security and risk management. As the adoption of SaaS applications continues to soar, organizations face the challenge of managing these applications effectively, especially when they are managed outside of the purview of IT and security teams.
The Challenge of TPRM Programs:
One of the pressing issues faced by CISOs is the lack of comprehensive visibility into third-party relationships and their associated risks. Particularly on their minds right now is how to govern GenAI applications, which are increasingly offered as SaaS applications, and can be easily integrated with core SaaS platforms, often without the review of IT or security teams.
Despite implementing third-party risk management (TPRM) programs and solutions, organizations often struggle to maintain visibility and control over their SaaS ecosystem post-deployment. This results in misconfigurations, unidentified and unmanaged applications, and risky and high-privileged SaaS-to-SaaS integrations that can expose sensitive data to unauthorized users. All these leave organizations vulnerable to security breaches and regulatory compliance violations.

Valence and OneTrust: Continuous Feedback Loop in TPRM
To address these challenges, Valence Security and OneTrust have partnered to create a seamless integration between SaaS Security Posture Management (SSPM) and TPRM, bridging the gap between risk managers and security analysts. This collaboration enables organizations to establish a continuous feedback loop, ensuring that security teams are informed about new vendors discovered within the ecosystem and can take immediate action to mitigate risks.
By implementing the joint solution, our customers can:
- Perform a comprehensive third-party cyber risk assessment
Valence Security’s comprehensive discovery of the organization’s SaaS human and non-human identities together with the TPRM context form OneTrust will provide comprehensive visibility to the level of privilege that each integration has as well as uncovering any unsanctioned vendors, dormant integrations, and any previously onboarded vendors with continued access to the systems.
- Implement seamless and continuous risk management
Each business unit and employee tends to unknowingly create new integrations either through new SaaS procurements or through OAuth consents. Each time a new SaaS application is connected by the organization’s user Valence Security will discover the connection ensuring that there is no gap in undetected third party vulnerabilities.
- Automate this-party risk remediation
Security teams can often create a barrier and a lag in communication between the time that the security analyst discovers a new vulnerability and when the risk team is made aware of it. Valence’s automated remediation capability helps bridge the gap by streamlining security processes by automating actions like notifying OneTrust of new vendors, eliminating or getting business user justification for integrations, or triggering vendor offboarding based on risk assessments.
Stop flying blind! Take control of your SaaS security posture with the powerful integration between Valence Security and OneTrust.
Learn More and see how this solution can strengthen your TPRM program today!
Understanding the Shared Responsibility Model in SaaS

The recent attacks targeting data in customers of Snowflake, a SaaS application focused on data storage, serve as a critical reminder of the importance of understanding the Shared Responsibility Model in SaaS security. While initial reports claimed threat actors had breached Snowflake's production system to compromise data at companies like Santander Bank and Ticketmaster, the situation unfolded differently.
Snowflake clarified that there was no internal vulnerability or misconfiguration within their platform exploited. Mandiant, who subsequently conducted an independent investigation, found no evidence “to suggest that unauthorized access to Snowflake customer accounts stemmed from a breach of Snowflake's enterprise environment.” Instead, attackers gained unauthorized access to Snowflake customer environments through two main methods:
- Compromised Customer Credentials: Attackers obtained login credentials for Snowflake accounts, likely through unrelated cyberattacks like malware infections or previous data breaches. These stolen credentials might have been for personal or work accounts, reused across different platforms.
- Lack of Multi-Factor Authentication (MFA): The threat actors were able to successfully target accounts with single-factor authentication. Armed with the stolen credentials with a high level of access, they had a clear path to access the Snowflake customer environments. Even with compromised credentials, additional security measures like MFA can significantly hinder attackers. Unfortunately, the targeted Snowflake customer accounts lacked MFA, allowing attackers relatively easy access once they had valid login credentials.
This incident underscores a critical aspect of SaaS security: the Shared Responsibility Model.
.jpeg)
What is the Shared Responsibility Model?
The Shared Responsibility Model in SaaS defines the security boundaries between the SaaS provider (a SaaS vendor like Snowflake) and its customers. It outlines the specific security controls each party is responsible for within the SaaS ecosystem. Imagine the security of your SaaS environment as a well-maintained bridge. The SaaS provider builds the core structure, ensuring a strong foundation (physical, application, and network security). However, the railings, signage, and upkeep (data security, access controls, user behavior) are your responsibility as the customer.
SaaS Security is a Collaborative Effort
SaaS Provider Responsibilities
In the Shared responsibility Model, the SaaS provider is responsible for securing the underlying infrastructure of the application. Breaking it down into more detail, the provider is responsible for:
Secure Platform Design: Designing a secure platform with robust features like strong password policies and MFA prompts, nudging customers towards best practices and reducing reliance on user enrollment. Building MFA into cloud services by design is a cornerstone of the Cybersecurity and Infrastructure Security Agency’s secure-by-design principles. Enforcing MFA by default whenever possible. Notably, Snowflake’s CISO Brad Jones talked vaguely about future plans to require customers to implement MFA, something other SaaS providers like Microsoft have begun to do.
Physical Security: This includes securing data centers, with access control systems and security cameras, as well as implementing environmental controls like fire suppression and temperature regulation to protect hardware.
Network Security: Securing the network infrastructure with firewalls and intrusion detection/prevention systems, and segmenting the network to isolate customer data and prevent unauthorized access.
System and Application Security: Regular patching and updating operating systems and databases, implementing secure coding practices, and data encryption at rest and in transit are crucial.
Vulnerability Management: The SaaS provider should continuously scan for vulnerabilities and prioritize remediation. Any critical vulnerabilities must be communicated to customers immediately.
Incident Response: A documented plan for detecting, responding to, and recovering from security incidents, with clear communication to customers.
SaaS Customer Responsibilities
While Snowflake is responsible for offering a secure platform, SaaS customers, like those in the recent incidents, are ultimately responsible for securing access to the data in their accounts. This includes enforcing strong authentication, restricting network access, and implementing basic security hygiene. Responsibilities include:
Enforcing Strong Authentication: Implement strong authentication measures including MFA and Single Sign-On (SSO) for all accounts and enforce strong password policies with regular rotations.
Securing Data: This includes data encryption, knowing where your data resides and which is of a sensitive nature, and implementing monitoring capabilities to see when data is transferred or shared both internally and externally.
Granular Access Controls: Follow the principle of least privilege (PoLP), granting users only the access they need. Regularly review and audit access, and ensure proper user lifecycle management (including offboarding from all applications). Deprovisioning dormant accounts helps to reduce the attack surface.
Maintaining Hygiene: Educate users on cybersecurity best practices (phishing awareness), vet third-party application security practices, and monitor user activity for suspicious behavior.
Governing SaaS-to-SaaS Integrations: Carefully evaluate the security posture of third-party SaaS applications before integrating them, understand and govern data flows between integrated SaaS applications. In addition, closely audit non-human identities (API keys, OAuth token, and service accounts) that power these integrations and revoke inactive and unnecessary ones.
Threat Monitoring and Threat Hunting: Continuously monitor user activity for anomalies and suspicious behaviors that might indicate a potential breach. Proactively hunt for threats within your SaaS environment to identify and address hidden vulnerabilities. Mandiant created a useful threat hunting guide for Snowflake customer environments.
Implementing the Shared Responsibility Model:
Effective implementation of the Shared Responsibility Model requires both parties to be proactive. Customers should leverage the security features offered by the SaaS provider and prioritize data security practices. SaaS vendors, in turn, should continuously improve their security posture and educate customers on best practices.
Beyond the Model - Additional Considerations
- Regular Risk Assessments: Conducting regular risk assessments of SaaS environments identifies potential vulnerabilities and facilitates proactive mitigation strategies.
- Communication and Transparency: Open communication between customers and vendors is essential for building trust and addressing security concerns effectively.
By understanding and implementing the Shared Responsibility Model, both customers and SaaS providers can create a robust security posture in the cloud, minimizing the risk of such breaches.
How Valence Security Can Help
Valence Security offers a comprehensive SaaS security platform specifically designed to address SaaS security challenges, including misconfigurations on the customer’s side of the Shared Responsibility Model. Our platform uniquely combines the capabilities of SaaS Security Posture Management (SSPM), SaaS risk remediation and SaaS Identity Threat Detection and Response (ITDR), and can help you:
- Gain SaaS Visibility: Identify SaaS misconfigurations (including configuration drift), risky SaaS-to-SaaS integrations, and improper data shares within your SaaS environment.
- Manage Access: Support enforcement of SSO and MFA, govern non-human identities, and manage user offboarding efficiently.
- Remediate Risks: Address security issues with both manual and automated remediation capabilities. This includes tools to strengthen collaboration between security teams, SaaS admins, and business users, helping to provide critical context into SaaS security risks and scale remediation efforts with minimal overhead.
- Continuous User Activity Monitoring: Our platform goes beyond configuration monitoring and remediation. We can identify suspicious user activity, such as data downloads from atypical IP addresses, that could indicate a compromised account. This allows you to take swift action and prevent potential breaches.
- Automate Best Practices: Valence helps you to simplify security processes, reduce the need for SaaS admin expertise of each individual platform, and support internal and regulatory compliance efforts.
See how Valence can help you secure your SaaS environment. Beyond Snowflake, Valence covers dozens of business-critical SaaS applications. Schedule a personalized demo with our team to discuss your specific needs.
The Danger of Sharing Files with “Anyone with the Link”: Examining a Risky Google Drive Misconfiguration

Often when it comes to security, a significant risk results from an action that is so easy that we tend to overlook the risk itself. Sharing a file using the “anyone with the link” option is the equivalent of leaving a treasure chest unlocked, overflowing with sensitive customer data. Unfortunately, it's a surprisingly common occurrence in cybersecurity, and the treasure chest in question is often data stored in a SaaS application.
Based on Valence research, a concerning 22% of external data shares utilize “open links”, meaning anyone with the link can access the data. Compounding this issue, 94% of these open link shares are inactive.
SaaS misconfigurations, mistakes or ill-advised practices in how SaaS applications are set up, can leave data vulnerable and organizations exposed. One of the most risky of these misconfigurations are open link data shares, which we’ll explain more in this article.
A case in point: Ateam's costly Google Drive misconfiguration
In December 2023, Japanese game developer Ateam learned this lesson the hard way. A misconfiguration in their Google Drive account left personal data of nearly one million people exposed for over six years! The culprit? A misconfiguration that allowed “Anyone with the link” to view files stored in their Google Drive. That setting essentially removes access controls and makes the file available to anyone on the internet who stumbles upon the link or deliberately finds it for malicious purposes. This means that for over half a decade, sensitive information like names, email addresses, phone numbers, and customer management numbers were accessible to anyone who stumbled upon the link.

The potential consequences of such a breach are significant. Exposed data can be used for identity theft, phishing attacks, or even sold on the dark web. Ateam's incident highlights a critical security concern: the ease with which sensitive data can be unintentionally exposed due to misconfigurations in SaaS applications.
Why are SaaS misconfigurations so common?
Organizations of all sizes and from all industries are susceptible to SaaS misconfigurations due to the complexity of SaaS environments and the dynamic nature of user permissions. SaaS applications come with a vast array of features and settings. Keeping track of them all can be a challenge for even the most experienced IT teams. Typical misconfigurations are lack of MFA/SSO enforcement, overprivileged third-party access, unsecure default sharing settings, publicly available data, and many more.
The 2024 State of SaaS Security Report underscores this point, with 43% of security executives citing the "Complexity of SaaS configurations" as a top security challenge.
Further compounding the issue is the dynamic nature of user permissions. Permissions are constantly being added, removed, and modified as employees come and go, and projects evolve. Configuration drift, or the tendency for configurations to deviate from security practices over time, can create security risks that go unnoticed unless actively monitored and addressed.
The dangers of open link sharing
The Ateam incident involving Google Drive serves as a cautionary tale for managing external access in cloud storage. While easy sharing features like "anyone with a link" exist across many platforms (from file storage platforms like Dropbox to communication tools like recordings in Zoom), they can be risky. While convenient, this method bypasses essential access controls, essentially leaving data wide open for anyone to exploit. Organizations can significantly reduce the risk of accidental data exposure by implementing stricter access controls. This includes granting access only to specific users, for defined purposes, and for the minimum amount of time necessary.
Recommendations to prevent open link data shares
So, how can organizations prevent these costly “Open Link” misconfigurations and protect their sensitive data? Here are some key recommendations:
- In general, avoid open link shares: It’s highly recommended for SaaS users to avoid sharing via "anyone with the link." While the convenience is clear, and perhaps the wider risk is seen as unlikely, it’s preferable to share files with individual users or user groups.
- Adhere to the Principle of Least Privilege (PoLP): Least privilege should serve as a foundational best practice. Grant users only the minimum level of access required to perform their jobs. Avoid blanket access controls and regularly review and update permissions, including deleting inactive data shares.
- Data Governance Policies: Establish clear policies for data classification, access control, and data sharing. Regularly review and update these policies to stay ahead of evolving threats.
- SaaS Security Posture Management (SSPM): Consider implementing an SSPM solution to go beyond user access control and analyze configurations within each SaaS application to identify and address security risks before they are exploited.
- User Education: Train employees on secure data sharing practices within SaaS environments. This includes avoiding open link sharing, understanding access control settings, and reporting suspicious activity.
How Valence Security Can Help
Valence Security offers a comprehensive SaaS security platform specifically designed to address SaaS security challenges, including misconfigurations. Our SSPM platform can help you:
- Gain complete visibility into your SaaS environment and identify misconfigurations, including improper data shares.
- Review user access, enforce SSO and MFA, govern non-human identities and service accounts, and manage user offboarding efficiently.
- Remediate SaaS risks with both manual and automated remediation capabilities.
- Continuously monitor user activity and detect suspicious behavior.
- Automate security best practices and support regulatory compliance efforts.
See how Valence can help you secure your SaaS environment. Schedule a personalized demo with our team to discuss your specific needs.
Read other critical insights from the 2024 State of SaaS Security Report
Open link shares and other misconfigurations are just one of the many focus points of the 2024 State of SaaS Security Report. The report explores the many challenges, potential security risks, and the best practices related to SaaS security. Download the full report today.
2024 State of SaaS Security Report Shows A Gap Between Security Team Confidence And Complexity of SaaS Risks

Valence Security has released the 2024 State of SaaS Security Report. Among the primary themes we saw in the report—which combines an industry survey with data collected by Valence from hundreds of real enterprise SaaS applications—is a clear gap between security leaders’ confidence in their existing programs and processes to protect their SaaS application environment, and a contrasting reality that reflects the complexity and diversity of SaaS security risks. The report highlights concerning trends like rising SaaS breaches, misconfigured security controls, overexposed SaaS-hosted sensitive data, overprivileged third-party integrations including GenAI tools, and more.
A gap between security confidence and a rise in SaaS breaches
Security leaders are prioritizing SaaS security, with 96% identifying it as a high or top priority. Furthermore, 93% of respondents reported an increase in their organization's budget for SaaS security compared to previous years. Alongside focus and investment, confidence in current security programs remains high, with 84% expressing "extreme" or "very" high confidence.

Despite this, over half (58%) of organizations experienced a SaaS security incident within the past 18 months. Recent high-profile SaaS breaches, such as the Microsoft Midnight Blizzard attack and the Cloudflare breach, underscore the vulnerability of SaaS environments and the potential for widespread disruption. These incidents demonstrate the need for a reality check and a shift towards proactive, automated security measures to protect SaaS-hosted data, strengthen management of human and non-human identities, and reduce attack surfaces in SaaS.
The need for a dedicated SaaS security program
The report reveals a critical need for a dedicated SaaS security program. The sheer number and complexity of modern SaaS applications, combined with distributed management practices, creates a constantly evolving security landscape. Traditional security teams struggle to keep up with manual processes like security checklists or periodic audits.
Top challenges and recommendations
The report delves into the specific challenges that security leaders face when securing SaaS applications. These challenges can lead to misconfigurations, inconsistent security practices, and difficulty in maintaining control over SaaS deployments and third-party integrations.
It also includes recommendations for reducing SaaS security risks, from maintaining an inventory of SaaS applications and performing continuous monitoring, aligning configurations with industry best practices, to adhering to PoLP and cleaning up unused accounts, third-party integrations and inactive data shares.
Discover How to Secure Your Business-Critical SaaS at RSA 2024

Give us 15 minutes and we'll help you find and fix your SaaS risks.
SaaS applications are increasingly more complex and managed decentrally. In turn, it's increasing misconfiguration, identity, data, and SaaS-to-SaaS integration risks.
To empower your business to securely adopt SaaS, you need to create a SaaS security infrastructure similar to what you created for IaaS. We'll walk you through what you need to quickly and easily do this with
- SaaS Security Posture Management (SSPM)
- Identity and Access Management
- Third-Party SaaS Risk Management:
- Policy driven remediation, not just automated ticketing
Book a meeting with one of our experts and make the most of your time at RSA.
Join one of our events to connect with other SaaS security leaders.
- CSA AI Summit Start Up Panel, Monday, May 6th, 8:00am - 8:45am, Moscone South, Level 3, Room 302. Register here
- YL Ventures Cocktail Event on Tuesday, May 7th, 6:00 PM - 9:00 PM (at capacity)
- Microsoft Booth (Microsoft Booth #6044N, Moscone North
- MISA Demo Station: Wednesday, May 8th, 11:00 AM - 12:00 PM
- Start Up Theater: Wednesday, May 8th, 12:30 PM - 12:50 PM
- Pitch for Charity event on May 8th at 4:20pm. Location: 100 1st St 6th floor, San Francisco, CA 94105. Attend
We look forward to seeing you in San Francisco!
Cloudflare Hacked Following Okta Compromise

Cloudflare disclosed that the Okta breach that occurred several months ago led to a suspected ‘nation state attacker’ gaining unauthorized access to their Atlassian servers. According to Cloudflare, the attackers that gained their initial access due to the Okta compromise back in October, were able to leverage a service token and service account credentials to access Cloudflare’s Atlassian servers. This exposed Cloudflare’s sensitive data such as Jira tickets, wiki pages, source code, and potentially more data sources.
This breach disclosure comes several days after Microsoft published a recent incident that led to unauthorized access to their corporate email by Russian state-sponsored threat actor Midnight Blizzard (also known as NOBELIUM or APT29). Even though the source of the breach is significantly different, the attackers used similar techniques that leveraged human and non-human identities to build their attack vector. The number of incidents that involve SaaS applications and their identities have skyrocketed in 2023 and seems like this trend is continuing into 2024.
What do you need to know?
- Back in October 2023, Cloudflare shared that it was breached due the Okta compromise
- Following the Okta compromise, the Cloudflare security team performed an in depth forensics analysis and rotation of more than 5,000 production credentials
- Unfortunately, the team missed 4 credentials of a service token and service accounts that belong to SaaS applications and other services
- Almost a month after the original breach, the threat actor used these credentials to gain access to the Cloudflare servers
- The attackers were able to access Jira tickets, wiki pages, source code and other data
- The attackers then established persistency by making administrative changes in Cloudflare’s environment
- One of these changes triggered an alert that initiated an investigation by the Cloudflare security team that remediated the threat
Non-human identities and where to miss them
Following the Okta compromise, the Cloudflare security team assumed the attackers had limited access, but was extra cautious regarding the potential blast radius of that breach. The team rotated more than 5,000 production credentials and performed in depth forensic analysis of their systems. The team missed during the credential rotation one service token and three service accounts that were leaked during the Okta breach. These credentials weren’t rotated because they were assumed to be unused. It’s unfortunate, but in this case it was enough to miss 4 out of more than 5,000 credentials to lead to this breach - every credential counts!
In our 2023 SaaS Security Report we reported that on average, over half (51%) of an organization’s SaaS third-party integrations are inactive. In most cases, security teams assume the inactivity means no risk - this is obviously not the case. In many cases non-human identity tokens that are inactive or even were never used in the past, are still stored somewhere. It doesn’t matter whether it’s in your internal systems or a third-party vendor’s systems - if they fall in the hands of a bad actor, they can use them to gain unauthorized access to your environment. The rule of thumb here should be simple - if it’s inactive and not needed - revoke it, don’t take the chances.
It’s all connected - the interconnectivity of business applications
Once the attackers had access to these credentials, they were able to leverage the Moveworks service token to authenticate through the Cloudflare gateway and into their internal systems. From there, the attackers leveraged a service account credential that was granted to allow the SaaS application Smartsheet to have administrative access to Cloudflare’s Atlassian. The attackers were able to access Jira tickets and wiki pages hosted on the Atlassian server. This exposed sensitive information about Cloudflare’s internal security practices such as secret rotation, MFA bypass, network access, password resets, remote access, and more.
Valence has been referring to the risks of business applications or SaaS applications interconnectivity for many years. API keys, non-human identities, OAuth tokens, SaaS-to-SaaS, service account, third-party apps, no/low-code automation workflows, and many other integration forms are leveraged by organizations to increase productivity and automate their day-to-day tasks. These integrations are typically not treated with the same security measures that human identities have. For example, you can’t enforce MFA or SSO or any form of strong authentication on a non-human. In addition, enforcing least privilege access is difficult due to complex relationships with other identities and lack of data from the business application vendors. Lastly, monitoring activities and detecting anomalous activities is challenging due to the amount of actions these integrations perform and the lack of proper data collection. Managing the relationships between your business applications is critical more than ever in our modern hyper-automated enterprise.
Beyond non-human identities - the need for holistic risk management
The attackers didn’t stop with Jira tickets and wiki pages. They knew that they needed to establish persistence that would allow them to continue their attack effort even if the credentials they originally used were no longer available or valid. The attackers leveraged the Smartsheet service account to create a new Atlassian account that mimicked a regular Cloudflare user and added it to several Atlassian groups. The attackers then leveraged a Jira plugin to install a command and control tool to ensure they kept their connectivity to the Atlassian server. This allowed them to attempt to further move laterally within the Cloudflare environment, access Atlassian Bitbucket sources code repositories, and more. Eventually the attackers added the Smartsheet service account to an administrator group which triggered the Cloudflare security team, initiated the investigation and incident response, and eventually led to removal of all the threat actor’s access.
Even though this breach involves a combination of SaaS and on prem business applications, it shows the importance of managing holistic risks when it comes to these applications. The attackers leveraged non-human identities to gain access to sensitive data, create new human accounts and make high privilege administrative configuration changes to gain access to sensitive applications and move laterally within the enterprise environment. These types of breaches require security teams to gain an understanding of their various resources within applications and to ensure they contextualize their posture management and threat detection efforts with the required information. Connecting between the dots of all related configurations, risks and changes is crucial to properly prepare for a potential breach and to effectively respond in case of a breach.
Valence - find and fix your SaaS risks
With the Valence SaaS Security Platform, security teams can now gain holistic understanding of their SaaS risks across identities (human and non-human), data shares, SaaS-to-SaaS integrations and misconfigurations. The platform provides instant insights into SaaS security posture, connecting between the various risks and allowing security teams to prioritize their SaaS risks and detect real-time threats. Valence goes beyond the traditional SaaS security posture management (SSPM) and provides advanced remediation capabilities that allow security teams to effectively remediate SaaS risks - whether if it’s inactive resources such as tokens or accounts, or high risk items that weren’t properly vetted. This is done in collaboration between the security team and the SaaS admins that manage business-critical SaaS applications such as Atlassian, Salesforce, GitHub, Workday and dozens more.
In the Cloudflare example, security teams that leverage Valence could monitor the suspicious activities and indicator of compromise (IoC) in the attacker’s behavior. Making high privilege administrative configuration changes, using inactive tokens, adding users, changing permissions, and other activities can be monitored by Valence and provide the appropriate alerting. Valence also enables proactive defense measures that can detect risky configurations such as inactive integrations, high privileged accounts and more that allows security teams to remediate the risk before it’s leveraged by malicious actors.
Learn more about the Valence platform and how it can assess your SaaS risks with our free risk assessment that can uncover unnecessary resources that you can remove to reduce your risk surface.
The Latest Microsoft Midnight Blizzard Breach is a Wakeup Call for SaaS Security
.png)
Microsoft recently published new guidance on the nation-state attack that they initially disclosed on January 19. According to Microsoft, the Russian state-sponsored threat actor Midnight Blizzard (also known as NOBELIUM or APT29) was able to leverage a test tenant account and a legacy OAuth application to gain access to corporate email accounts, including members of senior leadership, cybersecurity team, legal team, and others, and exfiltrated some emails and attached documents.
Microsoft Midnight Blizzard Attack: What Do We Know?
- The attackers initially gained access via a password spray attack to non-production test tenant account (human identity) that didn’t have MFA enabled
- To avoid detection, the attackers leveraged a legacy test OAuth application (non-human identity) that had full access to mailboxes and to read emails
- The threat actor created additional malicious OAuth applications and granted them access to Microsoft’s corporate environment using newly created user accounts
- The malicious OAuth applications authentication to Microsoft Exchange Online and target Microsoft corporate email accounts
- The attackers used residential proxy networks to obfuscate the source of their attack and leverage IP addresses of legitimate users
While there are probably still more unknowns than knowns regarding this breach, the early Microsoft disclosure, which included a Form 8-k filing on a major or material event to the U.S. Securities and Exchange Commission (SEC), discloses important information that can help organizations to improve their SaaS security posture. Below we’ll discuss a few key initial learnings from the disclosure, what organizations can do about it, and whether or not this is a one time breach (hint: it’s not). We’ll continue to follow details about the breach and will update accordingly.
Microsoft Midnight Blizzard Attack: Vulnerability or Misconfiguration?
This breach appears to be a classic SaaS/cloud focused breach that doesn’t leverage vulnerability exploitation, zero days or any manipulation of incorrect software logic. The initial Microsoft posts mostly focus on misconfigurations that were performed on the customer side of the shared responsibility model (even though the customer and vendor are the same here, it could have happened to any Microsoft customer). The attackers performed multiple changes to the tenant configurations including leveraging a test tenant account that didn’t have proper multi-factor authentication (MFA) configuration, abusing legacy OAuth applications that were over privileged, creating new human and non-human identities, and more. All of these actions can be used for legitimate purposes and are the responsibility of the customer or the user of the SaaS application to ensure they are properly configured.
The attackers were able to move from human to non-human identities and to move from a test non-production environment to the production corporate environment. This highlights how when it comes to SaaS applications, gaining a holistic view of your posture across your identities (human and non-human), third-party integrations, security configurations, and other misconfigurations is critical to ensure critical data is secure. SaaS applications, like Microsoft 365, hold the most critical data and privileges in modern enterprises so ensuring the security team manages potential attack paths that can leverage the complexity and interconnectivity of these applications is now more critical than ever.
Should I care about my test environment?
We often hear from customers that they are less concerned about their test environments - whether it's a development environment, a sandbox environment, or anything similar. Too often we encounter situations where production data is copied to these test environments for testing purposes or engineers grant production access to code, applications or automation that they are developing in the test environment before deploying it to production. In this case, the attackers identified a legacy test OAuth application that allowed them to elevate their access from a test environment to the Microsoft corporate environment. Later on, the attackers leveraged such access to grant themselves the Office 365 Exchange Online full_access_as_app role, which allows access to mailboxes.
Even though non-production environments are typically considered less important than production environments - it is important to ensure proper monitoring of their security configurations and activities. Attackers will often look for the weakest link in an organization’s security posture - which in this case was a series of configurations that allowed both the initial access due to lack of MFA and the privilege elevation from the test environment to the corporate environment. To avoid such misconfiguration risks, we always recommend that developer and sandbox environments are treated similar to production environments in terms of the enforced security controls. A great start would be ensuring identities have least privilege and strong authentication, reducing unnecessary interconnectivity with production systems, and removing unneeded confidential or sensitive data from these systems.
Why should I enforce proper lifecycle management?
Another common misconfiguration that we see in SaaS applications are abandoned resources - which could be dormant accounts, legacy API/OAuth tokens, inactive external data shares, and more. Too often, security teams treat these unused resources as low risks since they are not used by the business. The main reasoning for that is that the assumption is that the used resources have a higher likelihood of getting stolen by a threat actor. While this may be true, the return on investment (ROI) on removing the unnecessary resources is in many cases significantly higher. If a resource is unused, in many cases the business wouldn’t mind if it’s removed or disabled, which can reduce the potential attack surface with little to no friction to the business users.
Once again this is a case where the attackers were searching for the weakest link in the SaaS security posture. Used resources typically mean tighter security controls such as MFA, more rigorous monitoring for abnormal activity, etc., where abandoned resources are often, as the name entitles, just abandoned. Attackers recognize these resources are likely a blindspot for security teams and leverage them to gain unauthorized access and remain undetected. Therefore, we strongly recommend enforcing lifecycle management for any SaaS identity, token, data share, security configuration, etc. to reduce unnecessary access and risk and reduce the likelihood of a blindspot. Implement manual or automated regular review of your SaaS configurations to ensure you timely remove anything that you see as a risk or that is no longer necessary for your business.
Is this a one time SaaS-focused breach?
Unfortunately, this case is not the first and not the last SaaS breach that will leverage similar techniques. The same threat actor also recently targeted Microsoft Teams users and gained unauthorized access to corporate emails at Hewlett Packard Enterprise (HPE). They also used similar OAuth applications abuse techniques in the infamous 2020 Solarwinds breach and based on Microsoft’s Threat Intelligence team “Midnight Blizzard is also adept at identifying and abusing OAuth applications to move laterally across cloud environments and for post-compromise activity, such as email collection”. But leveraging SaaS misconfigurations, abusing abandoned resources and targeting non-human tokens is becoming a common practice by threat actors - large and small.
The Drizly data breach that led to the FTC taking action against the CEO of the alcohol delivery company is another example of similar patterns. In this case, the company granted GitHub access to an executive for a one-day hackathon and never removed that access, even when the executive moved to a different subsidiary. To make things worse, the account did not have MFA configured and did not have a unique complex password. This allowed a malicious actor to reuse credentials obtained from another breach to gain unauthorized access to the executive’s GitHub account and therefore to Drizly’s GitHub repositories. The attacker then leveraged credentials, source code and vulnerabilities they discovered to gain access to Drizly’s production environment - including databases containing millions of records of user information - which led to exfiltration of more than 2.5 million records.
These are just several of dozens of SaaS breaches that were disclosed over the past few years.
Microsoft Security Breach: How Valence Can Help
Valence empowers security teams to find and fix their SaaS risks. By combining in-depth coverage of multiple SaaS security use cases - from identity security, third-party integration governance, data protection and security configuration management - Valence provides a holistic approach to improving SaaS security posture. The Valence SaaS Security Platform combines SaaS security posture management (SSPM), threat detection and advanced remediation capabilities to ensure security teams can prioritize the most pressing findings and collaborate with SaaS admins and business users to remediate them.
Contact our team of SaaS security experts to get a free SaaS risk assessment which includes detection of risks and misconfigurations such as abandoned resources.
Empowering SaaS Incident Response with Valence and Microsoft Sentinel

As businesses increasingly rely on SaaS applications, their distributed ownership and intricate configurations are inadvertently exposing them to the risk of misconfigurations and devastating breaches. The decentralized nature of SaaS ownership often results in a lack of visibility into critical activities, making it difficult for security teams to effectively detect and respond to threats. Unauthorized access, exploiting human identities and third-party tokens, adds an extra layer of complexity to an already intricate security landscape. This is where the synergy between Valence Security and Microsoft Sentinel comes into play.
A Unified Defense
We all know time is of the essence when it comes to containing breaches. The integration between Valence and Microsoft Sentinel, a cloud native Security information and event management (SIEM) and Security orchestration, automation, and response (SOAR) platform, not only allows security teams to respond to SaaS threats with unprecedented speed and accuracy, but it delivers critical data and context from Valence’s SaaS Security platform, to enrich existing incident response workflows and minimize the breach risk to begin with.
1. Respond to SaaS Threats
By integrating SaaS risks detected by Valence with Microsoft Sentinel, organizations can create dedicated SaaS security incident response workflows, such as temporarily terminating admin access of users with compromised devices. This proactive approach ensures that potential threats are identified and addressed swiftly, reducing the likelihood of a breach.
2. Proactive Threat Detection
By seamlessly integrating signals from Valence's SaaS Security Platform into Microsoft Sentinel, you not only receive timely notifications of any malicious activities brewing within your SaaS applications but also gain the ability to respond effectively. Leverage the power of Microsoft Sentinel's workflows to orchestrate a precise and swift response, turning potential threats into mere blips on your security radar.
3. Detect Sophisticated Cross-security Attacks
By aggregating SaaS threats with cross-security ecosystem threats from various sources, including endpoints and cloud platforms, organizations can construct in-depth attack analyses. This holistic view enables security teams to identify patterns, correlations, and sophisticated attack vectors that might otherwise go unnoticed, and proactively manage existing vulnerabilities.
By combining Valence's SaaS Security with Microsoft Sentinel, organizations can now fortify their defenses, detect threats more effectively, and respond to SaaS security threats with unparalleled precision.
Now customers can easily discover integrations with Microsoft Sentinel, and others, within the MISA partner catalog.
Combine CrowdStrike Falcon with Valence Security SSPM to Combat Endpoint-to-SaaS Threats

Valence is excited to partner with CrowdStrike, empowering security teams to protect the growing endpoint-to-SaaS risk surface. The integration correlates SaaS security risk signals with CrowdStike’s endpoint security signals to improve overall security posture, threat detection, and incident response processes – Valence + CrowdStrike has you covered.
Distributed Infrastructure -> Distributed Attack Vectors
Breaches continue to be on the rise. In its 2023 Global Threat Report, CrowdStrike highlights a 95% increase in cloud exploitation cases in 2022 — a trend that correlated with increased adoption in cloud assets, including a 41% increase in SaaS application use. The combination of modern distributed infrastructure and increased SaaS usage creates endless new opportunities of unmonitored access to corporate data and processes. To exploit cloud environments, adversaries can’t rely solely on vulnerabilities and therefore leverage misconfigurations, human error, social engineering, credential theft and other attack methods to compromise critical business data and applications in the cloud.
In many cases, the initial access point that attackers leverage is a compromised device that contains high-privilege access or credentials to a sensitive application. Now more than ever, it is critical to bring together endpoint and SaaS application monitoring to ensure a holistic security posture and incident response plan, reducing the chances of a breach and rapidly containing potential damages.
Identify, Correlate, and Contain the Blast Radius
In today’s fast-paced digital landscape, the security of SaaS platforms is paramount. One of the threats faced by organizations stems from compromised endpoint devices, leading to a SaaS breach. The burning question arises: How can we swiftly and effectively correlate these incidents? The answer lies in associating compromised devices with user activities, permissions and SaaS configuration drifts. This correlation not only sheds light on the breach’s scope but also provides crucial insights into its potential blast radius.
Powered by native AI and world-class intelligence, the CrowdStrike Falcon® platform delivers real-time attack indicators, threat intelligence, and detailed enterprise visibility for enhanced security. You can now improve your understanding of a security incident’s blast radius to quickly mitigate risks by correlating Valence’s SaaS security posture management (SSPM) and SaaS threat detection from core SaaS applications with Falcon’s rich endpoint and user insights. Easily analyze a compromised user’s device, their SaaS privileges, and activities performed by the user before and after a potential breach to rapidly assess risk for effective response.
Unify Your Endpoint and SaaS Security Operations
With the Valence Security and CrowdStrike integration, security teams can improve their threat management processes by detecting compromised users’ SaaS permissions access and their recent SaaS activities. Security teams can:
- Expedite containment: Quickly identify and contain critical threats by combining CrowdStrike Falcon device insights with Valence’s core SaaS application risk signals, including user access privileges, to accelerate security operations
- Enrich threat investigations: Improve investigations by easily understanding incidents end-to-end, from initial endpoint compromise to malicious activities in SaaS applications, such as changing configurations, massive downloads of data, and other malicious activities
- Automate remediation: Swiftly remediate SaaS misconfigurations with automated workflows triggered when CrowdStike alerts to a compromise, including actions like termination of user data access and shares, and removal of integrations to other critical applications
- Improve security posture: Leverage the Valence platform to continuously analyze the Falcon platform data, providing visibility into potential misconfigurations such as unenforced SSO, weak authentication without MFA, over-privileged users, unauthorized third-party integrations, and more
Stay tuned for more updates on how the partnership continues to strengthen our commitment to your organization’s security.
Find us in the CrowdStrike marketplace!
Minimize the Breach Blast Radius with Valence Security and SentinelOne

SaaS breaches often originate from compromised endpoint devices. Wouldn't it be nice if you could quickly correlate such incidents? By associating the compromised device with its users' activities, permissions, and any SaaS misconfigurations, you could gain greater insights into the scope of a breach and understand its potential blast radius.
Today we proudly announce our strategic partnership with SentinelOne, a global leader in AI cybersecurity, securing endpoints, cloud workloads, containers, identities, and mobile and network-connected devices. This partnership helps organizations to enrich threat investigations by correlating user activity across endpoints and SaaS apps, providing holistic endpoint-to-SaaS context. The solution is now available as the first SaaS Security partnership on the Singularity Marketplace!
The impact of integrating endpoint and SaaS security can have is evident in recent incidents like the CircleCI breach. The breach originated from the compromise of a CircleCI engineer's laptop and rapidly spread to their SaaS applications, including GitHub. What makes such attacks particularly dangerous is that they can bypass identity security by stealing valid session tokens from the compromised endpoint user. Detecting such an attack becomes possible only when the compromised device signal is quickly correlated with the user's SaaS permissions, which is precisely what our combined solution offers.
To highlight the potential damage such breaches can do, our 2023 State of SaaS Security Report found that on average there are 54 shared resources on any given SaaS platform (e.g. files, folders, Sharepoint sites) per employee, and 193,000 shared resources per company. Multiply that by the number of employees and endpoint(s) per employee, and suddenly your organization’s exposure risk exponentially increases.
Valence Security and SentinelOne: holistic endpoint to SaaS context
The new Valence Security and SentinelOne integration combines risk signals from SaaS applications and enterprise endpoint devices. With the combined solution joint customers can detect what compromised users can do in SaaS applications and what recent activities were performed by compromised user accounts.
Enrich threat investigations:
By enriching endpoint device risk signals identified by SentinelOne with risk signals from core SaaS applications such as Salesforce, Microsoft 365, Slack, and GitHub derived from the Valence platform, security teams can assign higher criticality to endpoint vulnerabilities that, for example, are associated with users with admin access to SaaS applications - resulting in a faster containment of a breach if it were to occur.
Analyze the blast radius:
Correlating threat events that occur at the endpoint with threat events from SaaS applications detected by the Valence platform helps security teams better understand the scope of a speech. As an example, security analysts can discover endpoint user behavior such as critical information access and theft from core SaaS applications to determine the scale of an event.
Automate remediation:
Set up automated remediation workflows triggered through SentinelOne. These workflows respond to endpoint-generated events containing SaaS-related risks associated with identities, integrations, and data access.
Secure SentinelOne:
SaaS-based cybersecurity platforms host some of the most sensitive organizational data, which can serve as an attack vector to critical assets. The Valence platform analyzes SentinelOne’s management platform, enabling security teams to gain visibility into potential risks and misconfigurations such as unenforced SSO, weak authentication without MFA, over-privileged users, unauthorized third-party integrations, and more.
Learn more about our partnership with SentinelOne!
Valence Security Is a Proud Participant in the Microsoft Security Copilot Partner Private Preview

New York, US — [11/15/2023] — Valence Security today announced its participation in the Microsoft Security Copilot Partner Private Preview. Valence Security was selected based on their proven experience with Microsoft Security technologies, willingness to explore and provide feedback on cutting edge functionality, and close relationship with Microsoft.
“AI is one of the defining technologies of our time and has the potential to drive meaningful, step-change progress in cybersecurity,” said Ann Johnson, corporate vice president, Microsoft Security Business Development. “Security is a team sport, and we are pleased to work alongside our Security Copilot partner ecosystem to deliver customers solutions that enhance cyber defenses and make the promise of AI real.”
Valence Security is working with Microsoft product teams to help shape Security Copilot product development in several ways, including validation and refinement of new and upcoming scenarios, providing feedback on product development and operations to be incorporated into future product releases, and validation and feedback of APIs to assist with Security Copilot extensibility. To learn more, read the announcement.
“Securing SaaS applications requires security teams to gain knowledge and understand the threat landscape across a wide range of complex SaaS applications. Combining Valence’s SaaS security platform with Microsoft Security Copilot AI interface bridges these gaps efficiently, reducing the required level of expertise and training on each individual SaaS”, said Shlomi Matichin, CTO and Co-founder, Valence Security. “In the past few years, we’ve seen a significant rise in the number of SaaS breaches that leverage SaaS identities, third-party integrations and misconfigurations to gain unauthorized access to sensitive data. Joint customers can significantly improve their SaaS security posture and improve their incident response speed and efficiency, setting a new standard for SaaS security.”
Security Copilot is the first AI-powered security product that enables security professionals to respond to threats quickly, process signals at machine speed, and assess risk exposure in minutes. It combines an advanced large language model (LLM) with a security-specific model that is informed by Microsoft's unique global threat intelligence and more than 65 trillion daily signals.
About Valence Security:
Valence is the first company to offer advanced SaaS Security Posture Management (SSPM), combined with automated remediation and business user engagement. The Valence platform manages risks associated with data shares, SaaS-to-SaaS integrations, identities, and other misconfigurations. With Valence, security teams can engage with their business users to contextualize and remediate SaaS risks in dozens of SaaS applications such as Microsoft 365, Salesforce, GitHub and Workday, ensuring secure SaaS adoption, while accelerating business productivity and SaaS adoption. Visit valencesecurity.com for more information.
Five Lessons Learned From the Okta Breach
.jpg)
On September 29th, 2023, security vendor 1Password discovered unauthorized activity in their Okta tenant. An employee unexpectedly received an email that they had requested a report listing Okta administrators. A 1Password employee had recently uploaded a HTTP Archive (a HAR file), which is a browser session logging format that is typically used for troubleshooting, to Okta’s support portal. After the Okta logs didn’t indicate that their support team accessed the HAR before the breach occurred, 1Password suspected the employee’s account was compromised or that malware on an employee’s laptop was responsible.
On October 2nd, 2023, security vendor BeyondTrust discovered and stopped an attack against them. This occurred only minutes after sharing a HAR file with Okta’s support staff. This wasn’t a coincidence. The attackers found ways to bypass BeyondTrust’s admin policies by performing API actions, leveraging the fact that non-human identities typically don’t have the same level of restrictions and security controls. BeyondTrust suspected Okta had been compromised and told them as much.
On October 18th, 2023, security vendor Cloudflare discovered attacks on their systems and traced them back to Okta. Again, a Cloudflare employee had recently created an Okta support ticket that included a session token. And like the others, Cloudflare notified Okta of a possible breach of their systems.
While 1Password had been assured there was no unauthorized access on Okta’s side and turned the focus of their investigation to their own employee that had uploaded the HAR file, BeyondTrust and Cloudflare insisted that Okta was the source of the compromise.
On October 20th, 2023, Okta publicly announced that they had discovered unauthorized access in their support case management system. They note that all impacted customers were notified. Without more information from Okta, however, we don’t have the full picture, and don’t know how many other customers were affected. It’s quite possible the list is longer than just 1Password, BeyondTrust, and Cloudflare.
There is a pattern here: identity and security vendors. Okta, 1Password, BeyondTrust, and Cloudflare are all security vendors with products that protect some aspect of enterprise identities: authentication, passwords, and/or authorization. They also hold very high privileged access to their customer environments and in some cases, hold the “keys to the kingdom”, making them a very lucrative target for attackers.
Lesson 1: Protect Your Session Tokens
When troubleshooting issues with SaaS applications, it’s difficult to understand what’s happening on a customer system without access to the full session information. As such, it is common for support to request HAR files during the troubleshooting process.
A HAR file is simply a recording of a browser session. As it records everything, it is common for it to include sensitive data, like credentials and auth tokens. While Okta’s documentation for producing HAR files includes a warning to remove sensitive data before sharing it with them, it doesn’t appear that this advice was commonly followed, or enforced.

Recommendations:
- Build security defenses that don’t trust post MFA session tokens as the only line of defense - as mentioned in our recent blog, attackers are stealing these tokens to bypass MFA which is commonly used as the main security strategy.
- Employees should be aware that HAR files may contain sensitive data, and should make efforts to sanitize them before sharing with external parties. Tools for automating this process, like HAR Sanitizer, are readily available.
- Vendors commonly requisition HAR files from customers should assume mistakes will be made, warnings ignored, and/or steps skipped. As such, they should also make an effort to scrub sensitive data from HAR files upon receipt of these files.
Lesson 2: Monitor for Unusual Behavior
At least three of the vendors targeted by Okta’s attackers succeeded in catching the attacks against them quickly. BeyondTrust detected the attack using its own Identity Security Insights tool, as an attacker created new accounts within the Okta tenant. A 1Password employee received an email saying they generated a report on administrative accounts (that they did not generate) and quickly reported the anomaly. Cloudflare is less specific about how they detected the attack, but the trend here is clear - their detection controls worked as expected.
Recommendations:
- Detective controls should include notifications when new accounts are created, on any significant changes to administrative access/authorization, and any strange behavior coming from accounts with admin-level privileges.
- Ensure you’re collecting all the forensic data necessary to determine the cause and source of an attack. In recent breaches, we commonly see that logs are either not enabled, or don’t go back more than a few weeks, creating a blind spot for investigations.
- Employees should be trained to spot and report suspicious behavior - people are a detection control also!
Lesson 3: SaaS Vendors Are Common Targets
A troubling trend we’ve noticed is that attackers are recognizing the value of scale that comes from targeting the trusted third-party vendors. As most companies have adopted a shared responsibility model in the move to cloud and SaaS, the cloud and SaaS vendors become attractive targets. Especially SaaS applications that are trusted with high privileged access. Why compromise one target, when compromising part of the supply chain will get you access to thousands of potential targets?
Security vendors are targets, and clearly, they’re also customers of other security vendors. 1Password, BeyondTrust, and Cloudflare were all customers of Okta, and it’s entirely possible that Okta is/was a customer of each of them. Security vendors gain the same benefits of efficiency and scale from using SaaS and third parties as anyone else.
Recommendations:
- Assume some of your vendors will be breached (not just security vendors) and plan accordingly. Determine the potential impact of each compromise and ensure you have compensating controls in place.
- Determine what steps you can take to minimize the impact of a vendor or supply chain compromise. In this scenario, all three of the vendors affected by Okta’s breach applauded the principle of least privilege or zero trust principles and controls to minimize the impact of the breach on their systems. The result? All three of these vendors state their own compromises were limited such that their own customers weren’t impacted.
- Monitor your SaaS security posture - SaaS vendors leave it to the customer to leverage their security controls. Understand and maximize the native SaaS security configurations vendors offer. SaaS Security Posture Management (SSPM) tools can make SaaS security knowledge accessible, manage SaaS risks, and detect configuration drifts.
Lesson 4: Zero Trust Principles Work
1Password, BeyondTrust, and Cloudflare each mention that their application of Zero Trust principles helped either slow or mostly contain each of their respective attacks.
- BeyondTrust: “Custom policy controls blocked the attacker's initial activity…”
- 1Password: “This activity was confined to our Okta instance…”
- Cloudflare: “Cloudflare’s Zero Trust architecture protects our production environment, which helped prevent any impact to our customers.”
Recommendations:
- Study how attackers pivot between cloud systems, identity systems, and SaaS applications - don’t underestimate the power of non-human identities such as API keys and OAuth tokens.
- Engineer detections to alert of potential attempts to pivot between systems - including with SaaS-to-SaaS activities.
- Put controls in place to limit an attacker’s ability to pivot
- Separate administrative or superuser privileges from user accounts - this makes it possible to put tighter controls on accounts with administrator privileges without impacting productivity for normal user accounts.
Lesson 5: MFA isn’t a binary control
For many years, security experts have pushed for organizations to enable MFA wherever possible. In 2023, it’s clear that this advice needs to get more specific. Attackers have successfully compromised and evaded lower level multi-factor authentication options, like one-time codes sent to phones via SMS. Cloudflare specifically calls out higher-quality MFA controls as an advantage here (referring to the use of security keys):
“Cloudflare’s use of hard keys for multi-factor authentication stopped this attack”
However, MFA can’t be used everywhere. BeyondTrust notes that, while their MFA controls prevented the attacker from accessing their Okta instance via the Web-based interface, the attackers were able to perform malicious actions via Okta’s API. Since APIs are intended to be used programmatically (e.g. by a script, or application) MFA can’t be used, as there’s typically no human to respond to prompts for additional authentication factors.
Recommendations:
- Ensure MFA is enabled and enforced for ALL interactive user accounts.
- Use higher quality MFA whenever possible.
- Apply extra monitoring to non-human identities that cannot be protected by MFA.
Conclusion
Detecting, preventing, and responding to attacks in SaaS requires additional visibility and preparation. Proper governance will reduce the amount of opportunities for attackers to exploit. Applying Zero Trust principles will minimize an attacker's ability to move laterally between SaaS applications, clouds, and other environments. One of the most important things we can do is study attacks when they happen and search for lessons to be learned from them.
See the Valence Platform in action
Learn how Valence's SaaS Security Posture Management (SSPM) solution can assist with many of the recommendations listed throughout this blog.
In 20 minutes, learn how you can:
- Discover all your users, permissions and integrations
- Define SaaS security policies and enforce them with automated workflows
- Scale remediation workflows by engaging with business users
- Quickly remediate data, identity, SaaS-to-SaaS integration and misconfiguration risks
Schedule a demo now to see the platform in action.
Cloud Security - from IaaS to SaaS, from CNAPP to SSPM

Cloud security is no longer about only securing cloud infrastructure. With the rapid rise of SaaS applications and their evolution toward becoming one-stop-shop platforms, cloud security has entered a new phase where organizations need to better understand both their cloud infrastructure security posture and SaaS security posture. Whether simply adopting SaaS applications for productivity and collaboration or by moving all workloads to the cloud, organizations are increasingly adopting cloud services, in one form or another. SaaS Security, however, is complicated by the decentralized nature of SaaS management across multiple business units.
We’re now one step closer to closing the gap in this cloud security frontier by bridging cloud and SaaS security posture management through our collaboration with Orca Security. Together, Valence and Orca provide seamless security oversight for misconfigurations and vulnerability risks across cloud infrastructure and SaaS applications, reducing the risk of lateral attacks that can take place between SaaS and cloud environments.
In the past few years, many security teams increasingly focused on protecting production environments - primarily IaaS (AWS/Azure/GCP) and application security. Our increasing dependency on SaaS applications such as GitHub, Okta, Jira, Slack, and others, created a growing attack surface that could also affect the organization’s crown jewels and revenue generation. Attackers constantly search for the weakest link, probing across companies’ multifaceted attack surface. Often, SaaS application security posture is overlooked, creating entry points for attackers (through phishing, for example) or providing adversaries with lateral movement opportunities.
Let’s examine the Heroku and Travis-CI breach as an example of how a lateral move from a SaaS breach to the cloud can easily take place.
During this incident, the attackers gained access to Heroku and Travis-CI’s secrets, which included GitHub OAuth tokens that were granted to them, by customers, for legitimate purposes. The attackers then abused the tokens, gained unauthorized access to dozens of GitHub organizations, and downloaded data. This included GitHub’s own private npm repositories, which also led to the discovery and abuse of AWS API keys and access to AWS S3 storage.
Without the integration of the risk data and telemetry from an SSPM like Valence, and a CNAPP like Orca Security, these types of risks could continue to easily go unnoticed within many cloud-dependent organizations.
Bringing together the power of SSPM and CNAPP
Bringing together the power of SaaS security posture management (SSPM) and cloud native application protection platform (CNAPP) provides organizations with an unmatched visibility into their entire SaaS and IaaS risk footprint. By implementing our joint solution, you will:
- Gain visibility and context to identify misconfigurations, vulnerabilities, critical data leakage gaps, third-party integrations, and identity risks in both IaaS and SaaS environments.
- Explore toxic combinations of risks and attack vectors that leverage the interconnectivity between SaaS and IaaS identities and APIs to conduct lateral movement attacks between cloud environments.
- Protect Orca Security as a business critical SaaS application, ensuring Orca’s security posture is optimized to protect identities, integrations, and other valuable access into customer cloud environments.
Learn more about how the Valence and Orca partnership can provide a holistic viewpoint into all of your cloud security. Solution Brief
Top Security Recommendations for SaaS Applications
.jpg)
This is the seventh and final entry in my blog series based on the 2023 State of SaaS Security Report. The first introduced the report. The second focused on SaaS breaches. The third focused on data security. The fourth opined on SaaS identities. The fifth explores SaaS misconfigurations. The sixth surfaced SaaS integration insights. Finally, this one brings everything together with our SaaS security recommendations.
Check out the 2023 State of SaaS Security Report
Throughout this series, we’ve written about the importance of SaaS security. Nearly every business has critical SaaS apps today. SaaS-related breaches are real and increasing in frequency. We dove deep into the SaaS challenges related to data security, identities, misconfigurations, and integrations. While we’ve included some recommendations in each of these six prior posts, this post will focus entirely on recommendations, bringing all of our advice together into one comprehensive post.
1. SaaS-to-SaaS Integrations
We’ll start with integrations - one of the most eye-opening areas in SaaS security. Most organizations suspect there will be some integrations they’re unaware of, but are consistently surprised when they see the actual volume of user-consented integrations - often 10x more than expected.
Once this initial batch of unfamiliar integrations has been reviewed and acted upon, we recommend reviewing new integrations as employees onboard them. In line with our philosophy to enable the business, we propose quickly reviewing new integrations and understanding the business case after the integration has been enabled. The concern is that the old method of requiring business justification before allowing employees to create integrations had a chilling effect on using integrations altogether, preventing potential productivity gains.
When reviewing new integrations, consider vendor reputation. Ensure the permissions, roles, or scopes requested by the integration match what the integrations need, or is the vendor requesting more than they need? Also, consider configuration and monitoring options. Is it possible to use this integration securely, and within regulatory requirements? Can critical events be logged and monitored? Finally, request business justification from the consenting employee, to understand why this integration is important to them and/or the business.
Our final integration recommendation is to regularly remove any integrations that aren’t being used, are unnecessary, or cannot be used safely, or in line with compliance or regulatory requirements. Also, ensure these integrations only have the privileges they require. Remove any extraneous privileges, or create custom roles for these integrations to limit their access to the SaaS application they’re connected to.
2. SaaS Identities and Permissions
With integrations under control, we have a few recommendations related to identities. Review accounts with high levels of privilege or administrative access. Reduce these privileges when necessary, and ensure roles are correct. For example, when someone moves jobs within an organization, often their access privileges and/or role should change as well.
This is an excellent opportunity to ask questions like, “do we really need 147 global admins?” When working with our customers, we see no magic number for administrator roles. In some cases, we see a ratio of 1 admin per 25 employees, and in others, the ratio is 1 for every 100.
A recurring theme in our recommendations revolves around closed-loop processes or lifecycles. For example, deactivating SaaS accounts should be part of offboarding an employee who has left the company. Investigate idle accounts, particularly if the employee isn’t on vacation and doesn’t otherwise have a reason to not generate activity on company systems.
Finally, a centralized identity provider (IdP) can help manage security settings by offloading them. Instead of relying on a SaaS application’s native identity security controls (like multifactor authentication), using SAML or other forms of single-sign on, allow these authentication requirements to be pushed off to an IdP such as Okta, OneLogin, or Microsoft Entra ID.
3. External SaaS Data Shares
Sharing a document prior to a meeting is one of the most common external data-sharing scenarios. Having access to this document is critical for the attendees of that meeting. It’s unlikely, however, that anyone thinks to unshare the document once the meeting concludes.
On one hand, hundreds of thousands of external data shares are evidence that an organization is thriving and getting productivity gains out of its SaaS file storage solution. On the other hand, if 90% of those external data shares haven’t been accessed in over 90 days (which is the average, according to our research), that’s evidence of a data-sharing lifecycle problem. If the shares aren’t being used, they’re not providing any value to the organization. We recommend unsharing these unused data shares to reduce this potential attack surface.
Another method of sharing external data is by creating email forwarding rules. This is a common tactic used by attackers to exfiltrate sensitive company data. Look out for any email forwarding rules pointing to personal email accounts, or email accounts on domains or providers commonly used by attackers or in countries that your company doesn’t do business in.
4. SaaS Misconfigurations and Compliance
Every SaaS application is unique. Log formats differ. APIs differ. The information available varies. The customer’s ability to manage, monitor, and configure the service varies. Some charge extra for security features. Others include them in the base price.
To secure SaaS, it’s necessary to learn each platform and understand all the features, possible settings, and configurations (that’s a lot to ask a security team, which is one of the reasons we built the Valence SaaS Security Platform and its SSPM functionality). Aligning them to best practices, standards, and compliance requirements such as ISO, NIST or CIS, or company policy adds to this challenge. Not all SaaS configurations have security implications, and not all security options have compliance significance.
Even when configurations have been investigated and corrected to the most secure options, drift can happen. We recommend regularly monitoring for configuration drift and understanding the reasons behind changes.
5. SaaS Threat Detection
Threat detection is one of the trickiest security goals to accomplish in the world of SaaS, for a variety of reasons. While APIs make it easy to retrieve information from the SaaS vendor, or implement changes, sometimes the necessary logs or events for threat detection aren’t enabled or monitored. Since storage incurs a cost for SaaS vendors, logs may be disabled by default, or stored for a limited amount of time.
In addition to each SaaS vendor being unique, so is each customer. This complicates threat detection, as something that might be totally normal for one customer, could be a critical event for another. It’s difficult to avoid having to customize threat detection for each SaaS platform, scenario, and customer.
We recommend ensuring SaaS logs are enabled, monitored, and stored for an appropriate period of time. It’s also necessary to understand how the business is using these applications. Something that might look suspicious to a SOC analyst, could be the result of a totally normal, legitimate job function. Finally, we recommend studying SaaS-related breaches, data leaks, and incidents. As attackers turn more attention to SaaS, it is necessary to understand their attack tools and methods in order to spot them.
Wrap Up
Thus concludes our seven-part series expanding on our 2023 State of SaaS Security Report! We hope you’ve enjoyed this deeper dive into the topics explored by this report, as these blogs have served as a sort of ‘director’s commentary’. Check out the full report for more details, real-world examples of SaaS security challenges, and a more concise, 14-point checklist of recommendations from the Valence Threat Labs team.
Validate Cyber Insurance’s Preferred Security Controls in Your Critical SaaS

In today's rapidly evolving cybersecurity landscape, the surge in cyber threats and the wealth of available data on cyber posture and incidents have posed a unique challenge for the cyber insurance industry. As the number of attacks continues to rise, insurers face the daunting task of assessing and helping its clients mitigate cyber risks efficiently. To address this challenge, insurers have sought to distill their risk analysis into a concise set of 5 to 12 statistically significant key controls. While these controls provide a valuable framework, they’re no guarantee that organizations will implement controls effectively.
While these key controls serve as a starting point to identify critical technology needs, they frequently result in a binary checklist approach during the risk assessment process. This approach often overlooks the vital aspect of verifying whether these technologies are not only in place but also effectively deployed. Complicating matters further, cyber attackers routinely exploit multiple vulnerabilities to execute successful breaches. As such, assessing risk reduction through isolated controls and technologies becomes inadequate. Instead, a comprehensive risk assessment is needed - one that centers on safeguarding an organization's critical assets.
For insurers to conduct a thorough risk assessment, they must grapple with two fundamental challenges. First, they must identify where an organization's critical assets are located. Second, they must ensure that cybersecurity technologies are deployed to protect these core assets. Unfortunately, obtaining information about critical assets and security deployments is often an arduous process, conflicting with the speed at which underwriting processes operate.
One of the commonly overlooked critical IT assets is SaaS applications. SaaS applications have become integral components of the IT infrastructure, often hosting valuable company intellectual property, sensitive employee personally identifiable information (PII), and customer data. The accelerated adoption of SaaS applications, especially during the widespread transition to remote work, has been remarkable, with a 41% increase in just 2 years. However, anything with a web interface, from email and core business applications like Workday, Salesforce, and NetSuite to cloud infrastructure management consoles and cybersecurity tools, can be vulnerable to misconfigurations. Misconfigurations accounted for a staggering 55% of cloud data breaches in 2022, mainly attributed to human error.
SaaS Security risks manifest in several critical ways, underscoring the complexity of securing these applications.
- Gaps in identity security and access management
- Spaghetti web of third-party integrations and SaaS-to-SaaS interconnectivity
- SaaS security misconfigurations leaving apps open to attacks or misuse
- Unmanaged external shares of files, code, and other data asses
Implementing a comprehensive SaaS security platform that includes SaaS Security Posture Management (SSPM) capabilities, such as Valence, is key to addressing these pressing challenges. Valence equips enterprises with the tools needed to provide security validation for the critical cybersecurity controls outlined earlier.
- Multi-Factor Authentication (MFA): Our 2023 State of SaaS Security Research has revealed a surprising fact - at least 1% of assets within each organization lack MFA coverage. It's a common assumption that a centralized Identity Provider (IdP) with enterprise MFA should cover all assets, especially cloud-based ones. However, the reality is that unmanaged local accounts are often created in SaaS applications which could lead to unsecured dormant accounts. Valence's SaaS security platform can not only ensure that MFA authentication is properly configured on your SaaS applications, but also helps to ensure that all applications are enrolled within your Single Sign-On (SSO) deployments.
- Zero Trust Principles: In SaaS, applying zero trust principles means ensuring least privilege access to business-critical applications and data. Access can be granted in many shapes and forms - from adding users with administrative access, creating a new third-party API integration with sensitive access, or just sharing a file with the native collaboration options. Ensuring that any identity - internal employees, external collaborators or non-human identities have only the required level of access is key to improve SaaS security posture. With Valence, security teams can monitor the actual level of access granted to both human and non-human identities and collaborate with business users as they remove unnecessary permissions, accounts, tokens and data shares to apply zero trust principles.
- Vendor/Digital Supply Chain Risk Management: In 2022, third-party breaches took the lead as the primary cause of data breaches, surpassing ransomware-based breaches by 40%. OAuth-based SaaS-to-SaaS integrations can leave organizations vulnerable to third-party attacks, where attackers can exploit valid third-party tokens and non-human identities to access core SaaS apps directly. Shockingly, over 50% of integrations within organizations are inactive, adding significant and unnecessary attack surface. Valence's platform not only detects a comprehensive set of integrations but also flags high-privilege and tenant-wide integrations. Organizations can swiftly reduce their risk by utilizing our automated remediation workflows to remove inactive integrations.
As cyber insurance claims surged in 2023, the urgency to strengthen cybersecurity defenses became abundantly clear. SaaS applications, holding a central position within an organization's IT infrastructure, demand meticulous attention to identities, security configurations and third-party integrations. Valence Security is your strategic partner in implementing and fortifying these critical cybersecurity controls, ensuring that your organization is well-prepared to navigate the ever-evolving cyber risk landscape.
What Does Zero Trust Mean for SaaS Security?

Zero Trust is not a product, it’s a concept, and it applies broadly across many cybersecurity processes, controls, and products. It also refers to a particular information systems architecture and strategy. Despite the term’s overuse these days, its importance in reducing enterprise risk can’t be overstated.
The National Institute of Standards and Technology (NIST) defines Zero Trust Architecture (ZTA) as follows.
Zero trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised. ZTA is an enterprise’s cybersecurity plan that uses zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a ZTA plan.
In short, zero trust can be thought of as reducing access to the least amount necessary. This least privilege or least access applies to data, applications, networks, infrastructure, and anything else that has value to an organization (and therefore to an attacker). That’s a long list, however - how should we structure zero trust architecture when thinking about it and planning out a security strategy?
Thankfully, CISA has published a helpful Zero Trust Maturity Model that breaks this down into five ‘pillars’.
- Identity
- Devices
- Network
- Applications & Workloads
- Data
There are then three foundational capabilities that apply to each of these five pillars.
- Visibility and Analytics
- Automation and Orchestration
- Governance

Zero Trust Pillars and SaaS
One of the primary reasons SaaS is attractive to organizations is that it simplifies the application delivery model. Without any infrastructure to deploy, networks to configure, or software to install, implementing a new SaaS solution could be (and often is) as simple as clicking “Log in with Google” or “Log in with Microsoft”. With devices and networks less relevant in the SaaS model, the job of implementing zero trust is focused on three of the five pillars: identity, applications/workloads, and data.
Identity is at the heart of SaaS adoption, with single-sign on making adoption (and over-adoption, shadow IT, abandoned SaaS) as simple as clicking “sign up”. Managing and securing these identities is also a challenge, as MFA is rarely enabled or enforced by default, even today. Reducing unnecessary permissions attached to Identities is one of the most effective zero trust exercises when it comes to real-world risk avoidance. To this point, gone is the idea of an administrator as someone that has “all the permissions” that are available. Modern applications recognize that administrative functions often need much less access than originally assumed (ability to monitor, maintain, grant access to others). Legacy applications (even SaaS), however, often over privilege administrative roles, giving access to data and functions that aren’t necessary for admins to perform their jobs.
Applications and workloads are still a consideration, even within SaaS platforms. Nearly everything from environmental controls for commercial buildings, to cloud infrastructure, and even security products are managed through SaaS applications these days. Low-code and no-code platforms like Workato, Zapier, and Microsoft Power Apps are complex platforms with permissions managed at many different layers. At one level, these platforms are SaaS applications, and access to automated workflows should have the principal of least privilege applied to each workflow: the ability to create/delete/edit workflows and the ability to create/delete/edit connectors to each SaaS application that can be used as a building block within each workflow. Furthermore, the privileges granted by the credentials used for each connector is a concern as well - the connector should have only the access needed to perform the workflow, and no more.
Data remains one of the top challenges to secure. For it to be useful, it must be easy to access, explore, and share. Once lost, stolen, or exposed, however, there’s no undo. Data can be copied and exposed forever, meaning permissions must be carefully managed, and revoked when there is no clear business benefit to leaving it exposed. The benefit of SaaS is that auditing and managing these permissions can be fully automated, thanks to the convenience of APIs. There’s little excuse not to implement least privilege for SaaS-related data sharing when privileges can be codified and much of this work can be fully automated.
Zero Trust Capabilities Within Each Pillar
While CISA’s pillars divide ZTA into logical categories, achieving maturity within each pillar requires action. To operationalize and mature each pillar, CISA outlines three capabilities.
Visibility and analytics is essential to understand the scope and severity of the SaaS security situation. Visibility and analytics is all about discovering insights and answering questions. How many employees lack MFA enforcement? How many data shares are open to anyone with the link? How many no-code workloads have been configured with accounts that have too many permissions? Answering these questions is necessary to both understand the SaaS environment and assess the level of risk it poses to the organization.
Automation and orchestration in a zero trust context tends to focus on response capabilities and playbooks. In a SaaS context, it’s highly linked to hygiene and governance: ensuring data shares and identities don’t have unnecessary permissions, for example. Automation and orchestration can manage identity and data lifecycles, ensuring abandoned, or idle resources don’t create additional, avoidable attack surface for the organization.
Governance, as alluded to from the previous description of automation and orchestration, is the process of ensuring that zero trust principles are actually being applied in an effective and consistent manner. Reporting becomes very important in this stage, without which, it can be difficult or impossible to track progress in an organization’s zero trust maturity journey.
Achieving Zero Trust Architecture Maturity with Valence
The Valence SaaS Security Platform provides visibility, automation, and governance and addresses three of CISA’s five Zero Trust Maturity Model pillars: Identity, Data, and Applications/Workloads.
The Valence platform provides visibility into identities, mapping business users and identity-related security issues across multiple SaaS applications and platforms. Governance issues can also be identified: over privileged users, dormant accounts, and accounts unmanaged by the corporate identity provider.
Visibility into external data sharing helps identify unnecessary attack surface and inappropriate permissions. Policies address governance challenges, automating data lifecycle management.
Finally, visibility into SaaS applications and workloads provides analysis of unused, abandoned, and overprivileged configurations and SaaS-to-SaaS integrations. Policies here can also automatically remove unnecessary or unused integrations.
This policy-based approach of automatically maintaining least privilege across dozens of SaaS applications simplifies the process of achieving zero trust maturity while minimizing manual work.
Racking up Convenience Debt with SaaS Integrations

NOTE: This is the sixth entry in my blog series based on the 2023 State of SaaS Security Report. The first introduced the report. The second focused on SaaS breaches. The third focused on data security. The fourth opined on SaaS identities. The fifth explores SaaS misconfigurations. This post explores the very messy interrelated mesh of SaaS integrations.
Integrations are nearly as old as software itself. In fact, one of the very first plugins for Adobe Photoshop, Kai’s Power Tools (KPT), was considered indispensable. Back in 1992, you weren’t considered a serious Photoshop user if you didn’t have it. Software vendors understand the value of allowing integrations and plugins - by allowing third parties to add-on and connect to their application, the value of their product increases. SaaS-to-SaaS integrations come in many shapes and forms - OAuth tokens, API keys, marketplace 3rd party apps, low-code/no-code automation platforms, and more.
Most SaaS applications today allow some form of integration. Everything from Google Docs to Zoom to Notion, and of course ChatGPT/OpenAI allow customers to extend the capabilities of this software by connecting third-party code. Writing integrations, for example, range from simple tools to count the number of words or characters selected, to complex tools that check grammar, spelling, or even write entire essays for you.
Modern integrations are more than just add-ons. One of the biggest SaaS productivity challenges is sharing data across applications and with other collaborators. Imagine sales tools like Hubspot and Salesforce without the ability to integrate into your email system and contacts. Some tools, like the Superhuman mail client, can’t function at all without integrating into other SaaS applications. No-code automation platforms like Zapier and Workato are useless without integrations.
Attackers are also recognizing the potential of leveraging SaaS integrations to either gain access to unauthorized data or to move laterally between enterprise applications. These non-human identities typically don’t have the same security controls and monitoring systems. For example, such tokens don’t use managed devices and can’t authenticate with MFA. In various cases, such as the CircleCI, Heroku and Travis-CI breaches, theft of third-party tokens granted to legitimate vendors led to unauthorized access to sensitive data such as GitHub code repositories. In other cases, attackers created malicious third-party apps and tricked users to install them through OAuth consent flows, taking advantage of their access to sensitive data.
Convenience Debt
Like their historical predecessor, plugins, integrations have always been focused on making the user’s work easier. In the enterprise, there’s often some distance between the user, the SaaS admin, IT, and security. The user is just trying to get work done. If they can enable an integration that saves some time, effort, or solves a problem, they’ll just enable or install it. Those responsible for SaaS governance may not even be aware it’s happening.
There’s nothing wrong with convenience, and this isn’t about undoing all the productivity gains employees have found in enabling various integrations. On the path to discovering productivity, there tend to be a lot of abandoned experiments. Trials that didn’t work out. Betas that were too buggy. We’ve learned from experience that these failed experiments don’t get offboarded, creating convenience debt.
Report Findings
You might be wondering, “how bad does convenience debt get”? We’ve got some stats on that for you.
First, however, it is important to understand two types of integrations:
- There are those that entangle data and applications at the individual account level. This is the type most of us are familiar with.
- There are also ‘tenant-wide’ integrations. These integrations have the same level of access that a SaaS administrator would - for example, access to all users, their data, email, calendars, and/or all other related data within the SaaS application in question.
When it comes to individual-level integrations, over half (51%) of an organization’s SaaS third-party integrations are inactive, on average. That’s some serious convenience debt! The good news is that no one is going to miss inactive integrations, so they’re low-hanging fruit from a governance perspective. The even better news is that Valence’s SaaS Security Platform makes it easy to do large one-time cleanups or set automated policies that continuously clean up inactive integrations as they get old and gather dust.
On average, 10% of an organization’s integrations can be traced back to ex-employees, suggesting a missing component in sunsetting employee accounts in many organizations.
When it comes to tenant-wide integrations - every company we’ve worked with has granted full read/write access to email, files, and calendars to at least one third-party. The surprising stat is that, on average, there were 21 integrations per organization with tenant-wide access. That’s potentially 21 different third parties with full control over one company’s data, accounts, email, sales leads, and/or source code? That’s a LOT of administrative control trusted to third parties.
In the State of SaaS Security Report, one of our predictions was a boom in SaaS applications and integrations. We’re already seeing that boom today. Generative AI is great at creating, analyzing, polishing, and summarizing content. Nearly every SaaS platform or application out there could benefit in some way from this ability. There’s a Chrome plugin that can give you a 60 second summary of any YouTube video. Any word processor, slide sharing, or other content creation application can benefit from GenAI’s ability to address the ‘blank page problem’. Any meeting software that can generate a transcript can benefit from GenAI to create a summary of a meeting.
Check out the 2023 State of SaaS Security Report
These are just a few highlights from this year’s State of SaaS Security report by Valence Threat Labs! This blog series will continue to explore and share interesting insights from the report, but why wait? Check out the full report for more details, real-world examples of SaaS integration security challenges and recommendations on how to manage integrations!
SaaS Misconfiguration Misconceptions Debunked

NOTE: This is the fifth entry in my blog series based on the 2023 State of SaaS Security Report. The first introduced the report. The second focused on SaaS breaches. The third focused on data security. The fourth opined on SaaS identities. This post explores some of the misconceptions around SaaS misconfigurations.
We hear a lot about attackers exploiting vulnerabilities, but did you know that misconfigurations are just as common according to the Verizon 2023 Data Breach Investigations Report? You read that right - organizations are as likely to weather a breach due to an employee mistake as they are from an exploited vulnerability. It makes sense - why would an attacker exploit a vulnerability when a misconfiguration just gives them access?
Vulnerable by Default
It’s a common misconception that SaaS vendors do all the security work for you. This is rarely the case.
SaaS vendors, like most businesses, optimize for revenue, business growth, and customer adoption. How do they do that? They reduce onboarding friction, increase customer satisfaction, and upsell to more premium or enterprise features. Sometimes, the way they reduce friction and increase customer satisfaction is by allowing customers to do insecure things like ignore MFA, or choose bad passwords.
Sometimes, the upsell IS security - we’ve seen things like single-sign on, encryption, role-based access control, and other security features sold as add-ons, or only included in premium or enterprise tiers.
For example, we recently shared an article by Brian Krebs, where he pointed out that several organizations were leaking sensitive information from their Salesforce Community websites, due to simple misconfigurations. These accidents stemmed from unclear language that confused Salesforce administrators when setting up and configuring these sites. Vermont’s CISO, Scott Carbee, was quoted as saying, “My Team is frustrated by the permissive nature of the platform.”
Misconfiguration Mayhem
One needs to look no further than open S3 buckets to realize how damaging misconfigurations can be. Misconfigurations have enabled a lot of data leaks that have led to embarrassment, lawsuits, regulatory fines, and even extortion situations.
Similar issues can occur via misconfigurations of SaaS applications and platforms. As with cloud infrastructure, each SaaS platform comes with its own unique set of features and configuration options. There’s no normalized, common issue to look for across the SaaS landscape - each has to be investigated individually. SaaS platforms also have the concept of shared responsibility in common with cloud service providers. Don’t make the mistake of assuming the SaaS provider assumes all security responsibility or monitors for attacks - this is not typically the case.
This is exactly what the Valence Threat Labs team is focused on, day in and day out. Our team has identified hundreds of security findings across dozens of SaaS apps, such as Microsoft 365, Google Workspace, Salesforce, GitHub, Slack, Okta, and others. These issues range from ensuring logging is enabled, to protecting admin accounts, to preventing private data from being published publicly by default.
Not all misconfigurations are as simple as ticking a checkbox in a SaaS settings page, either. For example, unless a custom activity policy is defined in Microsoft Defender for Cloud Apps, no one will get alerts about suspicious usage patterns. Microsoft has some very useful anomaly detection, but it’s not on by default! It’s common for busy administrators to overlook the steps required to enable these detections.
Report Findings
The reasons for security misconfigurations varied. As we’ve previously mentioned, SaaS defaults are often not ideal from a security perspective but are rarely changed by SaaS administrators. This could be because administrators are too busy, are unfamiliar with security best practices, or just don’t have time to review SaaS configurations.
One of the most common reasons for security misconfigurations is bad UI/UX, particularly when it comes to data visibility. Sometimes “public” means “everyone inside my organization can see it”, and sometimes it means, “everyone connected to the public Internet can see it”. The difference is literally having to declare a data breach, or avoiding it.
Our 2023 State of SaaS Security report highlighted some insights as to why SaaS misconfigurations occur so frequently:
- Employees without IT or security training are managing SaaS configurations
- Insecure defaults
- Poor UI/UX
- Poor, or missing documentation
- Urgency leads to sloppy work
It’s necessary to learn how to leverage native SaaS controls to align with industry best practices (thankfully, Valence’s SSPM can help here, by mapping misconfigurations to standards). Without a way to monitor for configuration drift, or even better, prevent drift with automated policies, drift will happen.
Check out the 2023 State of SaaS Security Report
These are just a few highlights from this year’s State of SaaS Security report from Valence Threat Labs! This blog series will continue to explore and share interesting insights from the report, but why wait? Check out the full report for more details and real-world examples of SaaS breaches now!
SaaS Identity and Employees: the Keys to Productivity and Breaches

NOTE: This is the fourth entry in my blog series based on the 2023 State of SaaS Security Report. The first introduced the report. The second focused on SaaS breaches. The third focused on data security. This post delves into the security challenges related to SaaS identities.
There’s a lot of focus in cybersecurity on vulnerabilities, exploits, and assets. We focus on the data that was stolen, the device that was hacked, or the malware deployed. At the center of all these incidents, however, are identities.
The identities linked to employees and machines are a critical factor in nearly all breaches and serious security incidents. In fact, identities are one of the simplest and most popular ways for an attacker to gain access. Credential theft is quite popular, and there are a variety of ways an attacker could get access to accounts and their associated passwords or secrets.
Identity Challenges
Protecting identities has always been a challenge. Every time new protections are introduced and implemented, attackers seem to find a way around them.
Multi-factor authentication (MFA) initially seemed like a silver bullet for solving authentication woes, but there are now a variety of techniques for defeating them. Another option is to simply go around additional authentication factors by stealing auth tokens. Once an attacker steals an auth token, they can simply log in as that user - no additional factors required!
The second installment in this series, More SaaS Adoption → More SaaS Breaches, provides some examples of MFA bypasses and token theft.
Enforcing login through corporate SSO, SAML, or IdP such as Okta, Ping Identity, Microsoft Entra ID (fka Azure AD), OneLogin, and others, is also typically not enough. Many organizations assume they enforce corporate SSO across all identities and accounts in the organization, but there are nearly always exceptions. Edge cases such as shared accounts, service accounts, and external contractors break the holistic protection that a centrally governed login mechanism might promise.
Other identity challenges are related to the distributed nature of SaaS applications and platforms. If an employee leaves the organization, or is being investigated, it’s impractical to log into every SaaS application to understand the breadth of their access, and to properly offboard or disable their access.
Correlating Identities Across Platforms & Apps
The obvious solution is what the Valence Platform does today: build a profile for each identity - regardless of whether that identity is an employee, a machine, or an automated process. Context is key to understanding an environment. Regardless of whether an incident responder or someone in procurement is trying to understand a situation, the context surrounding the identity will help.
Identity and the context surrounding it can provide a lot of insight into employee activity, and is also at the center of many important questions. For example:
- Who shared this file and why?
- What do these 23 accounts with MFA disabled have in common?
- Why do we have 47 global M365 admins, and do we really need that many?
- What portion of these email forwarding rules belong to contractors, versus full-time employees?
- Who gave administrative rights to these third-party integrations?
- Why do some employees have dozens of external data shares, while a few have thousands?
- Why are some GitHub users not tied to the corporate SSO?
- Why is this exec’s account still active, 3 months after they left?
- And has there been any activity since their final day as an employee?
The answers are stories that can’t be told without linking to an identity. Without normalizing and correlating identity information across disparate SaaS platforms and applications, answering these questions is a manual mess. Not only would it be time consuming to correlate this information manually, it would require contacting the SaaS administrators of each app and platform in question - potentially dozens of different individuals.
Report Findings
This year’s report made a few things clear. For example, employee and account lifecycle management is tricky and often poorly managed - particularly when employees leave the organization. On average, 10% of all of an organization’s external data sharing and SaaS integrations remain tied to ex-employees long after they’ve left.
100% of organizations have dormant accounts that haven’t been deactivated. In one case, 1 in 3 accounts within an organization were dormant.
None of the organizations we analyzed had MFA enabled across all active employee accounts. There are always exceptions, which raises other questions and challenges. Are there cases where it’s acceptable and necessary for an employee account to have MFA disabled? Are contractor accounts handled differently from employee accounts, especially where MFA and other authentication protections are concerned?
Finally, it was clear that no two organizations were the same. Each had unique challenges and exceptions that required compromises when it came to managing identities. All the more reason to closely monitor and automate policy management across SaaS platforms!
Check out the 2023 State of SaaS Security Report
These are just a few highlights from this year’s State of SaaS Security report from Valence Threat Labs! This blog series will continue to explore and share interesting insights from the report, but why wait? Check out the full report for more details and real-world examples of SaaS breaches now!
Salesforce Best Practices When Using Named Credentials

Implementing SaaS security best practices can be challenging as they are often undocumented and poorly understood by security teams, business admins, and developers, leading to misconfigurations that can often pose a more significant risk than exploitable vulnerabilities.
To make matters worse, these misconfigurations become more common and potentially damaging as platforms increase in complexity. Founded in 1999, Salesforce was one of the first SaaS applications that, over time, has evolved into one of the most complex SaaS platforms due to its numerous supported integrations, privilege sets and usage models. This complexity has exponentially increased the likelihood of mistakes, misconfigurations and misuse.
What are Named Credentials?
Named credentials is a useful feature that helps Salesforce developers using Apex (a language proprietary to Salesforce) to avoid the use of hardcoded credentials and endpoints in code. Using hardcoded credentials poses a well-known risk that developers have to manage especially if they are saved in code, in plain text, making them easy to steal and abuse. Indeed, stolen credentials have been the entry point for the majority of breaches, according to the Verizon 2023 Data Breach Investigations Report, with 86% of all breaches involving the use of stolen credentials.
Alternately, the use of the named credentials feature in Salesforce is very flexible and potentially more secure, supporting different types of authentication such as OAuth and API keys. Even custom headers can be defined and based on contextual information, like relative user properties, for example. Ultimately, this feature is designed to keep cleartext credentials out of code, reducing the chances of data leakage.
So, Apex developers should embrace the use of named credentials and security is ensured, right? Not quite - there is a right and wrong way to use this feature.
Attack Scenarios
Named credentials lacking tightly controlled permission sets or other restrictions can actually be very useful to attackers. A malicious application, malicious insider or attacker that has stolen access tokens to your tenant could use a named credential to access other applications and their data, tenant-wide. Some of this data could also include other named credentials and access tokens, which could lead to more pivot opportunities and so on.
It’s worth noting that named credentials don’t necessarily just contain proprietary secrets. There are scenarios where stolen credentials could lead to pivots across an organization, across SaaS platforms, or even between partners and customers! The 2022 breach involving Heroku, Travis-CI and GitHub is one example where this was a key factor.
The attack possibilities are as complex as the mesh that interconnects SaaS platforms and trust relationships.
Using Named Credentials
Defining and using a named credential looks like this:
HttpRequest req = new HttpRequest();
req.setEndpoint('callout:Named_Credential_Name/path/to/your/endpoint');
Once the request is sent, Salesforce will replace callout:Named_Credential_Name with the necessary authentication keys, and will add any headers required for the session. This implementation is very convenient, as it automates a lot of additional work, eliminating additional coding. Also, since this replacement is handled server-side, no plaintext credentials are exposed.
Securing Named Credentials
Simpler code is easier to read and secure, right? This is often true, but there is still a right and wrong way to use named credentials. In the following example, a Salesforce admin wants to connect the GitHub API to create issues in a specific project, from Salesforce.
❌ The insecure way to do it:
- define NamedCredential.Endpoint: "https://api.github.com"
This will allow an attacker to do the following:
HttpRequest req = new HttpRequest();
// see all scopes granted to the api key
req.setEndpoint('callout:GithubCreds/authorizations');
// create an invite to the organization
req.setMethod("POST")
req.setBody('{"role": "admin", "email": "attacker@evil.com"}')
req.setEndpoint('callout:GithubCreds/orgs/MyOrg/invitations');
Configuring the named credential this way, for example, may allow an attacker to jump between SaaS platforms, beyond the intended and necessary context of the application. Integrations are often consented by SaaS admins, and given high privilege levels to avoid having to troubleshoot permissions issues. Attackers are aware of this and target these integration points.
Why would a developer take this shortcut? Developers are typically incentivized to just Get Stuff Done. Often, the more secure method requires additional research, troubleshooting, and effort that can delay delivery, pushing work into the next sprint.
If developer incentives prioritize speed and quantity over quality, creating broad authorizations is a potential shortcut that saves time but introduces potential security risks.
✅ The secure way to do it:
- Generate a GitHub API key, applying the principle of least privilege
- Configure your named credential with an explicit URI that cannot be abused by appending data. For example:
define NamedCredential.Endpoint: “https://api.github.com/repos/MyOrg/SalesforceRepo/issues”
By applying the principle of least privilege, we’ve made this named credential considerably more secure and resilient against abuse. Even if compromised, the attacker’s actions will be limited to a very narrow scope, and the ability to pivot with these credentials will be limited, if not impossible.
Conclusion
Salesforce Apex code and named credentials can be powerful tools when used and configured correctly. Misconfigurations are common, especially with developers focused more on fast delivery than security. Organizations need to educate developers and enforce SaaS security best practices when implementing these features.
This is the latest research from Valence Threat Labs, but more is coming. Keep an eye out for breach analysis, SaaS vulnerabilities, and SaaS security insights in the near future. Also go to the Valence Threat Labs page to get more info on the latest SaaS risks, and to the breach guide for latest SaaS-related breaches.
See the Valence Platform in action
Valence's SaaS Security Posture Management (SSPM) solution makes it easy to remediate risks across your SaaS applications.
In 20 minutes learn how you can:
- Discover all your users, permissions and integrations
- Define SaaS security policies and enforce them with automated workflows
- Scale remediation workflows by engaging with business users
- Quickly remediate data, identity, SaaS-to-SaaS integration and misconfiguration risks
Schedule a demo now to see the platform in action.
External Data Sharing Is Out Of Control: But Does It Have to Be?

Secure data sharing has historically posed significant challenges for enterprises. This third entry in my blog series on the 2023 State of SaaS Security Report (the intro blog is here, and the second, focused on SaaS breaches, is here) delves into the hurdles faced by organizations governing data. This post explores legacy methods of data sharing (email attachments, file transfer software and sync & share solutions) as well as modern, cloud-based SaaS methods. Along the way, organizations have been challenged by a lack of effective shared data lifecycle management, which is borne out in the findings of the report. For example, on average, 90 percent of a company’s external data shares haven’t been accessed for more than 90 days.
The Dark Ages of Data Sharing
When I first started in cyber security in the early 2000s, protecting data and sharing securely were difficult challenges for enterprises along multiple dimensions:
Email Attachments
Email often imposed attachment size limitations. This was often frustrating, as there was no standard on maximum attachment size. Every organization could set a different limit, or live dangerously and set no limit at all! I once saw an Exchange cluster go down because someone tried sending a 1 gigabyte Microsoft Access database to 32 internal recipients.
The result was that email was down for the entire organization for most of the day. Incredibly, we couldn’t find any elegant solution to this problem at the time. The best way to prevent a single employee from taking down the entire organization’s comms was user education. A lack of file size awareness was a critical availability risk to the organization!
File Transfer Software
Dedicated file transfer products like Filezilla, MOVEit, and Accellion made it easier to share or send large amounts of data without trusting a third party, but placed all the risk in the hands of the sender. Easily guessable, or shared credentials were often abused to explore FTP servers and other file transfer servers. More recently, vulnerabilities have had a massive impact on the customers of these products, affecting hundreds, if not thousands of organizations.
There’s now an alternative to this nightmare: let someone else manage the file transfer software.
Enterprise File Sync and Share
One of the earliest file, sync, and share software startups, Box, envisioned a future where files would be synchronized between devices, saving users the trouble of remembering where they put things, or having to constantly transfer files between devices. As this category of products matured, it became a core pillar of what end users think of as “the cloud”, with a copy of all files stored by a third party.
This architecture made sharing a very simple process, regardless of the size or quantity of files. Today, sharing files is a simple, routine task. While this new level of convenience removed the need to manually organize data, we also began to lose awareness of what data was being stored or synched.
The Golden Age of Data Sharing
Today, the simplicity of cloud-based SaaS data sharing creates a significant productivity boost and virtually eliminates the need for legacy file sharing methods. Files can be shared within seconds, eliminating the need for downloading. Products like Google Drive, Dropbox, Box and OneDrive allow recipients to directly edit or review files in their browsers, facilitating real-time collaboration. Simultaneous file editing or reviewing has become a standard practice in business workflows.
However, with this power comes a corresponding responsibility. Every individual employee must apply the principle of least privilege when sharing data. In reality, most business professionals are unfamiliar with the term 'least privilege'. They typically opt for the "anyone with the link" option, as it seems hassle-free. Choosing any other option poses potential access control issues that require troubleshooting, which is time-consuming and undesirable when a seemingly effortless and universally functional option exists.
Adding to this challenge, more and more SaaS tools support external data sharing. Most of us associate data sharing with products that have ‘drive’ and ‘box’ in the name, but SaaS platforms like Zoom, Monday, Notion, GitHub and even Salesforce now have options to share data externally.
Due to a lack of use, current data share controls are no more effective now than they were in the dark ages of data sharing.
The Path Ahead For Data Sharing Control
Note that this section isn’t titled “the path back to data sharing control”. As mentioned earlier, most organizations have never had much control over data. File servers were dumping grounds for data. Exfiltration was possible over a myriad of methods: removable media, file transfers, email, SaaS, cloud, and more. This current age of API-enabled cloud and SaaS is the first real opportunity to exercise some control over how data is accessed and shared.
Data sharing is missing a lifecycle management component. Our work with customers shows that one of the most common data-sharing use cases is single-use sharing. Someone needs to share data once, perhaps for a single meeting or project. Ideally, the data share should be revoked as soon as it is no longer needed, but that doesn’t typically happen. Data assets are often shared indefinitely, whether it’s necessary or not.
Our research data shows some clear patterns. On average, 90 percent of a company’s data shares haven’t been accessed for more than 90 days. These shared resources represent risk to the organization, but sit abandoned and unused. This is 90 percent of an average of 193,000 shared assets per company, or 54 shared assets per employee. Additionally, 30 percent of these shared assets are shared with a personal (not corporate or B2B) account, such as a GMail, iCloud or Outlook.com account.
There’s a clear opportunity to actively manage the lifecycle of shared data assets. SaaS APIs make it possible to identify unused sharing, notify employees of the issue and/or automatically unshare them when they are no longer needed. It’s a win/win for organizations, as employees won’t miss what they’re not using, and the organization painlessly reduces risk without imposing significant overhead on the security team.
Check out the 2023 State of SaaS Security Report
These are just a few highlights from this year’s State of SaaS Security report from Valence Threat Labs! This blog series will continue to explore and share interesting insights from the report, but why wait? Check out the full report for more details and real-world examples of SaaS breaches now!
Exploring the Microsoft Storm-0558 SaaS Breach

Valence Threat Labs strives to keep our customers informed about significant breaches and security incidents that impact the SaaS landscape. On June 16, 2023, a Microsoft 365 customer alerted Microsoft to some anomalous email activity they had detected. Microsoft began investigating and found that an external adversary had compromised the email of 24 other customers as well. The attack began 32 days prior, on May 15, 2023.
This breach was notable for a number of reasons. First, instead of going after each target organization individually, the adversary chose a more efficient route. They compromised the SaaS vendor, Microsoft, to get to each of the target companies. This way, only one attack was necessary to access the email of 25 separate organizations, rather than 25 separate attacks.
Microsoft determined that the attack was performed by a China-based adversary referred to as Storm-0558, which has been associated with politically motivated attacks. Microsoft also noted that this adversary specializes in phishing, email, and SaaS attacks. The targets included US government agencies and private companies that work with the US government. Storm-0558 could have targeted any Microsoft 365 customer, but chose to limit focus to these 25 organizations for reasons that aren’t known or haven’t yet been shared.
The attacker used some novel exploits to achieve this attack by abusing signing and access keys. The attacker used a stolen signing key to forge Azure AD tokens. The term forge is important here, because a validation issue in Microsoft’s code made it possible to create and use invalid tokens. As long as these tokens were properly signed, Microsoft would allow their use.
The forged Azure AD tokens were then used to generate access tokens and steal email via the Outlook Mail API. Microsoft permanently addressed the two vulnerabilities that enabled these attacks but still haven’t discovered how the attacker stole the initial signing key that was used to kick off this attack.
Incident responders working for some customers affected by this attack became frustrated that necessary data wasn’t available. This data was unavailable because the customers weren’t paying for Microsoft’s premium security suite. This mirrors the experience shared at the beginning of this post and emphasizes that, while vendors should provide the necessary security features and tools, the customer still needs to ensure they’re paid for, deployed and working as expected.
Valence Threat Labs Recommendations
While Microsoft stopped the attack and fixed the vulnerabilities, it was a customer who originally detected the attack, over a month after it began. This breach emphasizes the importance of maintaining and utilizing security controls that are accessible to you, as the customer of a SaaS platform. Also, the line drawn in the SaaS vendor’s shared responsibility model may not be drawn where you expect it to be, or want it to be.
Know Your Tokens
Access tokens are everywhere. Every modern login, app, and service today generates a new access token. As the name implies, these tokens grant access to certain features, data and capabilities within the SaaS platform.
Tracking these tokens may be challenging, but it is essential to ensure that your environment is not accessed by parties in ways that you did not intend.
Awareness of new access tokens created and used during this breach could have allowed the affected organizations to escalate the issue earlier, potentially preventing further data loss.
- Track newly generated access tokens, given their access scopes and owners
- Watch for Token Replay attacks (when a token is stolen, and used elsewhere)
- Prepare playbooks to invalidate tokens when necessary to mitigate threats
Log, Monitor, Alert
Before you can respond to threats in your environment, you first need to know they are happening. This process can be broken down into 3 steps.
Log - Logs are a record of events that occur in your environment:
- Get to know your platform’s logging capabilities and events
- Map the important events and understand their meaning
- Enable relevant logs (some platforms disable logs by default)
Monitor - Now that we are recording events, we can monitor them. There are many tools that can ingest logs, prioritize and alert on notable events. Traditionally, SIEMs have been used to centralize this data, but often suffer from alert fatigue challenges. Posture management tools have emerged in the past few years to address this challenge for SaaS, Cloud, and other environments.
Alert - Platforms can generate a ton of logs, quickly drowning teams in events that can’t be effectively tracked. You should write queries that highlight and alert on specific events of interest or chains of events.
For example, this specific breach could have been detected using the following event types:
- Suspicious IP address activity - look out for suspicious IP addresses that access your environment (Such as Tor, VPN, or any other abnormal IP addresses). In this breach, both Tor and VPNs were used to access the targeted organizations. For a list of IOCs, including IP addresses, related to this breach, see Microsoft’s list here.
- Mass Download of Data - create a baseline for typical data access volume and investigate any deviation from the norm. In this breach, the actor downloaded large amounts of email data from target organizations.
- Token generation - monitor new tokens and their scopes. In this breach, the actor generated new tokens with high-privilege scopes.
- Token use - tokens may be generated by a user, but are easily stolen and used by an attacker. Create a baseline for typical usage, and look for abnormal activity. In this breach, the actor used API calls to download large amounts of email, which may not have been typical for the targeted users.
Posture Management
The term ‘posture management’ has been borne out of the realization that security teams need more than event data to monitor and understand IT environments like the cloud and SaaS. In addition to alerting on critical events and discovering misconfigurations, posture management also includes the concept of setting baselines and policies that make configuration drift visible.
Once a baseline is established, however, it becomes much easier to spot anomalies, like the strange behavior related to this breach, that customers noticed and reported to Microsoft.
Conclusion - Improve Your Readiness
This breach is sadly only one example where we’ve seen SaaS attacks that involve similar techniques. Token theft and abuse has been present in the CircleCI, Lastpass, and Heroku/Travis-CI/GitHub breaches as well.
Security incidents are stressful events we should all do our best to prevent, but they’re also opportunities. Within the details of breaches are lessons to be learned - a roadmap for improving your security program. Don’t wait until the day the attack comes. Ensure you have the necessary training, preparation and tools before scenarios like these occur.
- Simulate Attack Scenarios to verify that security operations and incident response teams can detect and respond to a SaaS breach
- Prepare Playbooks for General Scenarios in each platform such as Invalidating Tokens, Blocking IP Addresses, Disabling Compromised Users, etc.
Get the 2023 State of SaaS Security report
The 2023 Valence State of SaaS Security report compiles our perspective on SaaS security, the latest threats, data from dozens of real companies, and finally, our recommendations and predictions for this market. It is a perfect primer for anyone wanting to better understand SaaS security challenges and how to solve them. Grab a copy today and share with your colleagues!
More SaaS Adoption → More SaaS Breaches

This is the second installment in a series focusing on our 2023 State of SaaS Security report. The first post in the series is here.
Despite the frequency of breaches, attackers are fairly predictable. They’re opportunists. They’ll go to where valuable data and useful identities live. Today, more than ever, that leads them to SaaS applications. There are a number of ways SaaS breaches can occur. Here are a few of the most common we see:
Multi-factor Bypasses
Multi-factor authentication isn’t the silver bullet to preventing identity-based attacks it’s sometimes made out to be. More secure forms of MFA work well for securing human identities. The real world is messy, however.
Overlooked misconfigurations leave MFA disabled or unenforced. OAuth tokens grant access without authentication factors. Machine-to-machine SaaS connections can’t use MFA, as there are no humans to enter secondary factors. Same with service accounts. MFA bombing and SIM-swapping attacks have been successfully used to bypass less secure forms of MFA.
Info stealer malware steals authenticated SaaS sessions and sells them in marketplaces. No need for usernames, passwords, or 2FA tokens.
Example: CircleCI Breach
The CircleCI case was just one of many recent examples where session tokens were stolen from an engineer’s laptop by malware. ‘Information stealer’ malware is designed to scoop up credentials and session tokens, to be abused directly, or sold by initial access brokers on the black market.
In this particular case, an engineer’s 2FA-backed SSO session gave attackers access to generate access tokens to production CircleCI environments. This access led to the theft and abuse of GitHub OAuth tokens (SaaS-to-SaaS) belonging to CircleCI customers.
Since these session tokens are intended to be used transparently, without user intervention, MFA won’t slow an attacker down in this type of scenario. Looking at it another way, the attackers don’t necessarily need to defeat MFA if they can just go around it.
Unnoticed Platform Abuse
If an attacker created a new user account with administrator rights on your most critical SaaS platform, would you notice? What if someone was systematically downloading all customer data? What if privileges were escalated without reason or justification? Are SaaS services suddenly being used from a new location, or in a different way?
Sometimes logging isn’t enabled on these platforms. When it is, the logs often aren’t collected or reviewed. Even if events are reviewed, it’s possible for staff to miss critical events. Behavioral anomalies might create patterns only visible when analyzed at a larger scale.
Monitoring for platform abuse is difficult, particularly with hundreds of privileges, trust relationships between platforms and dozens or hundreds of SaaS applications in use.
Example: Okta/Sitel Breach
Just because the technology changes doesn’t mean attacker behavior needs to. Twenty years ago, attackers and penetration testers often found it necessary to create accounts. This could be to extend access in the compromised environment, pivot into another environment, or provide persistence - alternate means of accessing the target’s systems if the original intrusion points are closed off by defenders.
When Sitel, a third-party contractor with access to Okta customer data, was breached, the behaviors observed were classic adversary TTPs that go back decades. They occurred in a Microsoft 365, but this same story could be told in the early 2000s, in an on-prem Windows Active Directory environment. The attackers:
- Accessed credentials stored in plain text file
- Created new accounts
- Added new accounts to groups with Admin privileges
- Created mail forwarding rules to capture communications
These old techniques still work on modern SaaS platforms. Sadly, IT and security teams still miss them.
Stolen Trust
Adversaries know that one of the best ways to get past defenses is to look like a trusted party. After all, business grinds to a halt without some trusted relationships and paths in place. Compromise a trusted partner, service provider, or third-party vendor, and an attacker knows they can ride in undetected.
Exploits, stolen credentials, social engineering and other direct attacks are the more expected paths. The truth is that insider attacks, whether from an actual insider or someone that has taken over their identity are extremely common as well. This kind of attack can take many forms as well.
- A stolen OAuth key, sold on the black market
- Using a third party’s credentials to publish an app integration
- Stolen API keys and/or certificates
Example: The OiVaVoii Campaign
Threat intelligence has always been difficult to operationalize, but it becomes worthless when attacks come from a trusted, or benign source. In the OiVaVoii campaign, attackers leveraged compromised Microsoft 365 accounts to create malicious OAuth apps. These apps were then used effectively in social engineering attacks against other organizations.
This campaign resulted in the successful takeover of many C-level executives’ accounts, including CEOs, general managers, former board members and presidents. These accounts were presumably then used to further abuse privileges and launch social engineering attacks. The full impact is not publicly known.
Configuration Confusion
In the same vein as stolen trust, misconfigurations are also highly likely to lead to breaches or data loss. Some common causes for misconfigurations:
- Insecure default settings
- Confusing documentation
- Poor UI/UX
- Vulnerabilities in the SaaS product itself
- SaaS administrators with no IT or security experience
- Poor operational practices (overprioritizing convenience over security)
There can also be a fine line between a “vulnerability” in a SaaS platform and “working as intended, but the customer is using it wrong”. Who might be to blame is irrelevant when the outcome is the same, however.
Example: Leaky Salesforce Community Sites
When focused on malicious attacks, it’s sometimes easy to overlook the level of damage that can be caused by accidents. According to the Verizon 2023 Data Breach Investigations Report, roughly 10% of all breaches are caused by unintentional errors.
Much could be said about the impact of S3 bucket misconfigurations over the past decade, but more recently, Salesforce misconfigurations were making the headlines. Security researchers discovered numerous misconfigured Salesforce Community sites. As with S3 bucket snafus in the past, website admins assumed these sites were only accessible by authorized users. Unfortunately, the website data was accessible to anyone that knew of a method to exploit Salesforce’s overly permissive controls.
Check out the 2023 State of SaaS Security Report
These are just a few highlights from this year’s State of SaaS Security report from Valence Threat Labs! This blog series will continue to explore and share interesting insights from the report, but why wait? Check out the full report for more details and real-world examples of SaaS breaches now!
Introducing the Valence 2023 State of SaaS Security Report
.png)
Get the 2023 State of SaaS Security report

There’s something I love about putting together a big annual security report. The combination of data insights and industry trends is an opportunity to present a snapshot of the big picture. There’s the luxury of time we don’t have with a single blog post and a depth of exploration we can’t go into with an infographic or a time-limited podcast.
It feels a bit silly to wax romantic about an annual security report, but I love storytelling, and at the core of a report like this is a chance to tell a story. The day the Verizon DBIR is released every year feels a bit like Christmas morning to me. While the Verizon DBIR is an order of magnitude more expansive (a team of half a dozen spends an entire year on it), I’m very proud of what we’ve put together here, especially as it is laser-focused on a high-risk threat vector that doesn’t receive enough attention – SaaS applications. Our report is the result of teamwork and deep SaaS expertise, with contributions from every level: from our product and security research teams collecting the raw data from dozens of real-life customer deployments to our CEO and Co-founder, Yoni, providing his industry knowledge and detailed feedback on content and style.
SaaS Adoption Is Exploding
This report, in fact, is an excellent summary of why I was excited to join Valence Security in the first place. Constant tech innovation keeps security teams very busy, which is critical to combat evolving threats and clever threat actors armed with new tools like generative AI. SaaS, especially, is arguably one of the biggest and most impactful tech movements of the last 20 years, but it happened so gradually, it’s easy to take for granted. It contributed to or led to trends like:
- Less reliance on in-house and colo data centers
- Less reliance on IT staff for software needs
- The decentralization of enterprise software (business users evaluating, purchasing, and managing tools, independent of the IT team)
- The ‘consumerization’ of enterprise software
- The mobile app explosion that cemented the design formula for the modern smartphone
- The remote work movement, which exploded during Covid.
- Near ubiquitous availability of APIs and API-first product strategy philosophies
- Low-to-no code platforms
- Some of the most massive and accelerated market growth ever seen, funded largely by venture capital
The SaaS Report Findings
What better time could there be to adopt a platform that provides visibility and automated management of SaaS security best practices? This year’s Valence Security report takes you through how we got here, how cybercriminals are responding to the ‘saasification’ of the digital office, and what we’ve learned in our first few years helping our customers get their SaaS messes under control. Here are a few key things we’ve learned, that you can learn more about in the full report:The
- Employees love sharing data. It’s easy and convenient. However, an average of 90% of shared resources are shared indefinitely and aren’t being actively used.
- Following this same trend, 51% of an organization’s integrations are inactive, on average. It’s easy for employees to give a third-party access to SaaS platforms, and just as easy for them to forget that they’ve done so.
- There are integrations, and then there are tenant-wide integrations. Imagine giving a third party full access to your entire digital office. All email. All calendar access. All files. The ability to create, disable, or delete any information or accounts. Now consider that the average number of tenant-wide integrations is 21 per organization! Nearly two dozen third parties with full control over an organization’s employees and all their resources.
- Organizations have always had a hard time with ex-employee accounts and access. Fear of deleting critical data and integrations attached to accounts. Fear of breaking workflows dependent on them. It’s no surprise that 1 in 8 employee accounts are dormant but still active. What do they have access to? Are new security controls applied to them?
- It’s easy for misconfigurations to go unseen. Maybe everything was secure when that big SaaS security project was completed, but did it stay that way? How many exceptions have been made between then and now? For example, even if as few as 1% of employees don’t have MFA enabled, that’s more than enough for an attacker to use a cred-stuffing attack to gain a foothold.
In the report, you’ll also find:
- 5 key types of SaaS breaches, how they happen, and real-world examples
- 14 SaaS security recommendations, based on the lessons we’ve learned from our customers
- 3 big predictions about the near-term future of SaaS security and the trends that will impact it the most
Let's Fortify our SaaS Defenses Together
The 2023 Valence State of SaaS Security report compiles our perspective on SaaS security, the latest threats, data from dozens of real companies, and finally, our recommendations and predictions for this market. It is a perfect primer for anyone wanting to better understand SaaS security challenges and how to solve them. Grab a copy today and share with your colleagues!
Read The Dark Reading article on this report.
The 2023 Valence State of SaaS Security Report

SaaS has shifted many business functions to third parties and now drives enterprise communications, operations and growth across organizations. At the same time, securing the complex mesh of SaaS apps, integrations, users and data has become a distributed responsibility between vendors, security teams and end users. The increasing regularity of SaaS-related breaches confirms the need for a coordinated security response across these groups.
This is where we begin with the 2023 State of SaaS Security Report - how did we get here, and what do we do now? The report takes us through the rise of SaaS, to SaaS-based attacks, our own insights from our customers, and finally to our recommendations and predictions about where SaaS security is going.
We’re delighted to share this report with you - enjoy!
How Generative AI Benefits SaaS Security

The term artificial intelligence was at the tail end of a previous hype cycle in Information Security, particularly with a changing of the guard in the antivirus space. Those that figured out how to harness machine learning for spotting novel malware samples, and got that technology to market first, won the race. Those that didn’t, faded away with the hype.
Suddenly, here we are again - artificial intelligence hype is bigger than ever. Yet generative AI is a very different technology than what we’ve seen used by security vendors in the past. This AI technology is innately human, achieving a natural communication flow and sophistication that current virtual assistants never achieved. Large Language Models (LLMs) are uniquely suited for communication, which is why one of its most successful forms so far is a chatbot (ChatGPT - the fastest-growing tech product ever).
We believe that speed to market is as important as getting it right. That’s why we’re excited to announce that we have found some significant use cases for generative AI in the Valence SaaS Security Platform and worked around the clock to deliver it to our customers
One of the major challenges in SaaS security is that security teams are required to become experts in many SaaS applications. Each one has unique terminology, permissions, data models and security configurations. It’s both unlikely and unrealistic to expect security teams to become technically fluent across each of these SaaS platforms.
What if they didn’t have to? By leveraging generative AI capabilities, the Valence AI Assistant can analyze SaaS security risks and help security teams quickly define a remediation plan. The AI Insights option sends the data we have about SaaS applications and security configurations to OpenAI’s GPT, which elaborates on importance, context and remediation. This saves security teams the need to search for each issue separately and parse documentation on a case-by-case basis.

It is natural to be concerned about AI hallucinations, but this issue can be minimized, which Valence has successfully achieved in this release. The latest versions of GPT, on which the Valence solution is built, are considerably less likely to hallucinate than earlier GPT versions. More targeted use, and access to external data - both factors in our use case, also minimize the chances of hallucination.
The Valence SaaS security platform supports dozens of SaaS applications such as Microsoft 365, Google Workspace, Slack, Salesforce, GitHub, Okta, Atlassian, Workday and more. By leveraging the power of AI, security teams can now improve their knowledge and understanding of risks across all these platforms and establish better communication with business application owners that manage these applications today.
Read the press release here.
For more information and to see a demo of the new SaaS security AI Assistant, contact Valence Security.
The Digital Office Moved to SaaS

Two trends have reinvented the enterprise’s relationship with software: SaaS and public cloud.
The management of custom, in-house software and workloads have been vastly simplified by migrations to one or more of the public cloud providers - offerings like AWS, Azure, Oracle Cloud, and Google Cloud. The once hyper-specialized field of IT (storage admins, network admins, database admins, sysadmins) is steadily giving way to generalists (cloud and devops engineers).
For everything else, there’s SaaS.
The modern office moves at the speed of business, which no longer slows to wait for IT or security approvals. Commercial off-the-shelf software is mostly SaaS these days, and requires little technical know-how to get up and running. All it takes is an employee credit card, some minor setup, and anyone can become a SaaS admin. This is the story of how the office moved to SaaS and what security and IT folks need to do to catch up.
Who Moved Our Cheese?
In the famous Invisible Gorilla experiment and later book of the same name, Christopher Chabris and Daniel Simons set out to demonstrate how easy it is for people to miss unexpected changes. There’s often a difference between what we think we know, and reality. Sometimes things happen that we don’t expect and we explain them away as anomalies. Sometimes changes occur so slowly that one day we wake up and wonder, “when did all this happen?”
The SaaS revolution was very much like this. The first few SaaS apps to hit the market were met with skepticism. We didn’t know where our data was being stored. We didn’t like the feeling that we couldn’t see and touch the servers we were using. Trust had to be earned.
Before long, SaaS became so common, it became difficult to keep track of. The level of scrutiny declined with each new SaaS app onboarded until trust became the default. More recently, SaaS apps have grown into massive, multifaceted platforms, and are often onboarded by folks entirely outside the IT department. What were once simplified versions of on-premises software became increasingly complex due to demands for more features, role-based access control, integrations, and to increase the level of customization available to customers.
At some point, we realized that the most critical functions of the modern office have all moved to SaaS. Email, calendars, files, payroll, CRM, ERP, source code repositories, and many more critical functions are all delivered by SaaS for the vast majority of organizations today. For folks that didn’t have their “when did this happen” moment by 2020 know exactly when this process was completed for their organization: the COVID-19 pandemic.
The pandemic made a permanent shift in attitudes toward working remotely, empowering employees. The employee has more control than ever - over how to equip their home office and what tools to use - both physically and digitally. This new reality creates some challenges for IT and security teams that we’ll discuss later.
What Changed For The Better?
Speed and time-to-value: with the move to SaaS, it no longer takes weeks to plan and design a software rollout. We don’t have to order hardware, install and configure software. We don’t have to plan code freezes or outage periods for patching. We don’t have to buy more hardware to upgrade a few years down the line. The efficiency and simplicity of using SaaS have made the decision to switch an easy one.
SaaS has also made some new use cases possible. In the old days, building an integration between two products often required a team of contractors to write code and build a custom solution to synchronize data between two systems. These days, most SaaS have openly available APIs and pre-built integrations for the most common SaaS platforms. A few clicks, share API keys or consent to a third-party app in a SaaS marketplace, and a SaaS-to-SaaS connection is made. Low/No Code platforms like Microsoft Power Platform, Zapier and Workato make it possible to automate workflows between SaaS applications without a user needing to be present.
Auditing access control across the millions of files organizations produce was once an impossible task. File servers would be brought to their knees trying to log every file interaction. Cloud-based file storage solutions like Dropbox, Google Drive, Box, and OneDrive log this information seamlessly, and it is all available via an API.
Additionally, it’s possible to share a file with anyone, anywhere - something that was previously a massive challenge. Email servers might limit attachment sizes to 5 megabytes or less, leading to disorganized file shares with wide open access controls. Sharing a file with someone outside the organization was even more difficult, often leading to someone hastily setting up an FTP server and fast-tracking firewall changes. Now, we simply right-click, copy a link, and paste it into an email or chat message.
Creating an account is no longer an onerous process that requires creating yet another password (or simply reusing one). SaaS applications make it easy to sign in with Google, Microsoft, Facebook, GitHub, Apple, and many other common SaaS platforms. Creating an account often takes just a single click.
However, SaaS should be easier to audit, configure and control, so where’s the problem?
What Didn’t Change?
The business brand of urgency that leaves security concerns behind didn’t change. Why would it? SaaS was more convenient than ever. Enterprise killer apps now exist on smartphones. Files, email - all corporate data is automatically synchronized between phone, tablet, and laptop computers. There always seems to be enough time to get new software working, but not enough to lock it down and apply least privilege. Existing bad security habits worsened and new bad security habits emerged.
Dubious Data Sharing
Understanding what data we have, the significance of it, and where it lives is more challenging than ever. Instead of all data being dumped into a handful of databases and file servers, it could now be nearly anywhere. Data needs to be accessible and portable, but these attributes that make it useful make it easy to misplace or lose.
Valence has found that the average business has 54 externally shared resources (e.g. files, folders) per employee and 193,000 per company. Sharing these resources keeps businesses running. One problem is that they don’t get unshared when no longer needed, creating a massive, growing attack surface that largely goes unseen. Another is that there’s rarely a process to determine if someone is authorized to access a file.
A very popular sharing option is the kind where “anyone with the link” can access it. These links can be shared with impunity - a list of customers shared with a sales partner can easily be forwarded to a competitor. Privileges need to be continuously reevaluated based on changing business needs and employee roles.
Inane Integrations
Precisely what makes SaaS so successful is what creates such a challenge for IT and security teams. The productivity benefits are massive, but with little to no oversight, security issues, cost concerns and governance quickly becomes a problem.
As with external data sharing, integrations often remain even though they’re not being actively used. Unlike data shares, integrations can delegate breathtaking amounts of access to third parties.
On average, Valence has found that an organization will have 21 tenant-wide SaaS-to-SaaS integrations. That means 21 third parties have full access to act as an administrator: creating and deleting accounts; reading anyone’s files or emails; reading and editing any employee’s calendar.
That’s an average of 21. It’s hard to imagine why any organization would need to give that many third parties that level of access. The answer, more often than not, is that they don’t. As soon as they become aware of these integrations, most organizations remove most of this access. Some are often proofs of concept that were never revoked after the POC was done. In other cases, the company migrated to a new vendor, and admins either forgot to revoke the old vendor, or were afraid of breaking something by doing so. Regardless of the scenarios, a lack of visibility into SaaS use is clearly an issue.
Massive Misconfigurations
Like public cloud providers, SaaS has a shared responsibility model. There’s a common assumption that SaaS vendors would choose the most secure defaults possible for their customers, but that’s not the formula for selling more software. SaaS vendors that want to win over competitors remove friction and make adoption as easy as possible - which often requires security compromises. Instead of chasing vulnerabilities and CVEs, security teams have to worry about misconfigurations with SaaS applications.
The result is that most SaaS applications are optimized for a smooth, positive user experience - not for security or privacy. It took AWS years to update its UI/UX, making it more difficult to make costly access control errors with S3 buckets. Even the most baseline security configurations, like ensuring only employees can access an application, can be confusing and difficult to work out. In one example, Vermont’s CISO, Scott Carbee, expressed frustration with Salesforce Community sites, saying, “my team is frustrated by the permissive nature of the platform.” It seems many well-meaning features can present themselves to security teams as bugs.
So again, as with cloud providers, it makes sense to have a SaaS security tool that keeps track of everything from critical security gaffes to best practices and privacy requirements across multiple, disparate SaaS apps.
Unmanaged Identities
Identities have always been a challenge to manage, regardless of the era we’re talking about - even with SSO and/or an IdP. In large and even mid-sized companies, employees are constantly in flux - joining the company, leaving, changing departments, getting promotions, or getting shuffled around in a reorg. Human resources is often reticent about removing accounts, for fear of losing critical data or breaking an important process. To that point, our data shows that 1 in 8 accounts is dormant on average.
Contractors also require access to data and systems, often for limited timespans. Some contractors may be closely and individually vetted, while others are only vetted as an organization, by a vendor management program. There are also non-human identities that need access to data and systems but can’t use multi-factor authentication. These non-human identities are often used by third-party software and SaaS using the popular OAuth standard.
Granting access to data and systems is often a stressful, urgent process. The CEO needs to give a demo to a client in 30 minutes. Without the right access, a contractor won’t be able to meet a deadline, delaying a product launch. Trying to grant exactly the right levels of access could result in a painful back-and-forth that wastes precious time, so more often than not, administrators grant more access than needed.
Managing all these identities and the access granted to them is a nearly impossible task without a tool to help with the analysis. Spotting mistakes and deficiencies is important, but it is equally important to be able to see contextual information across many systems.
Conclusion
The digital office has moved and it seems like we’re in a constant state of catching up. The modern organization’s files, schedules, communications, concerns, plans, and goals all live in SaaS applications today. It’s easier than ever to collaborate, but it’s also easier than ever for data to leak. We’ve passed the tipping point where SaaS security, hygiene, and threats can no longer be safely ignored, or pushed off to be next year’s worry.
Valence was built to help organizations manage SaaS security risks resulting from misonfigurations, unused and overprivileged SaaS-to-SaaS integrations, ungoverned external data sharing and unmanaged identities. Valence enables security teams to effectively engage users to ensure that security decisions to remediate these risks are made within the context of business need and that end users work with and see security teams and processes as business enablers, not impediments. See the Valence SaaS Security platform in action.
Unleash the power of Valence, your ultimate defense against SaaS security risks. From tackling misconfigurations and excessive SaaS-to-SaaS integrations to managing external data sharing and user identities, Valence has got you covered. It empowers your security teams to make informed decisions, balancing your business needs with security imperatives. With Valence, security becomes a business enabler, not an obstacle, turning your business teams into strategic allies. Experience the Valence SaaS Security platform first-hand.
Valence Announces MISA Membership
.png)
Valence Security Announces its Membership in the Microsoft Intelligent Security Association (MISA) to Extend the Reach of its SaaS Security Solutions
TEL AVIV, Israel--Valence Security, a leading SaaS Security Posture Management (SSPM) vendor, has announced its membership in the Microsoft Intelligent Security Association (MISA), an ecosystem of independent software vendors and managed security service providers that have integrated their solutions with Microsoft's security technology to better defend against a world of increasing threats.
Valence's membership in MISA reflects its commitment to providing global enterprises with one of the most advanced SaaS security platforms available. As a member of MISA, Valence will be able to offer enhanced integrations with multiple Microsoft Security products, as well as other leading security vendors in the MISA ecosystem, that will further strengthen customers' ability to gain better visibility and control over risks associated with the distributed adoption and management of SaaS, SaaS-to-SaaS integrations, ungoverned external data sharing, unmanaged users, and misconfigurations.
"We are excited to be part of the Microsoft Intelligent Security Association," said Yoni Shohet, CEO and co-founder of Valence Security. "This collaboration enables us to leverage Microsoft's industry-leading security capabilities and provide our customers with even more powerful and comprehensive security solutions that keep them protected against the latest SaaS security threats, remediate SaaS security misconfigurations and place security guardrails to collaborate with business users."
Yoni continues, "By joining MISA, Valence deepens its relationship with Microsoft's best-in-suite set of cyber security products and its ecosystem of strategic security partners. Working together, we aim to strengthen our shared mission of increasing the cyber resilience of every business in a constantly evolving threat landscape."
In October of last year, Valence announced its integration with Azure Active Directory (Azure AD) through Microsoft Graph, Azure AD (part of Microsoft Entra) audit logs and other Microsoft APIs. Through it Valence is now able to correlate multiple data sources to provide one viewpoint into all the Enterprise Applications, Service Principals, OAuth tokens and APIs that have access to Microsoft’s SaaS services. In addition, in April the Valence platform announced it now leverages Microsoft Azure AD risk signals for both human users and non-human service accounts.
“The Microsoft Intelligent Security Association has grown into a vibrant ecosystem comprised of the most reliable and trusted security vendors across the globe,” said Maria Thomson, Microsoft Intelligent Security Association Lead, “Our members, like Valence Security, share Microsoft’s commitment to collaboration within the cybersecurity community to improve our customers’ ability to predict, detect, and respond to security threats faster.”
Valence's membership in MISA is a significant step in enhancing its already robust security features. With this relationship, Valence can offer its customers an even greater level of protection and the ability to better quantify the impact of SaaS risks.
2023 SaaS Security Trends & Insights

Download the 2023 SaaS Security Trends & Insights infographic which details some of the more notable trends and challenges related to third-party SaaS applications, OAuth integrations, external data sharing and unmanaged identities. This is original research from Valence Security Threat Labs derived from data drawn from the Valence Collaborative SaaS Security Remediation Platform.
Valence Selected as 2023 SC Awards Finalists

SC Media announces that Valence Security is one of the 5 2023 SC Award Finalists for Most Promising Early-Stage Start Up.
Some of the most high impact technologies emerge not from the mainstay security companies, but businesses many have never heard of – yet.
Businesses recognized in this new category are privately held startups offering a strong, flagship product that is within two years of initial release. For now, they're focused on continued product development, customer growth, business development and overall fiscal and workforce expansion; but they also serve as notable contributors within a community shaping future innovation.
Read The Full SC Media Post
2023 SaaS Management Index Report

The Vast Majority of SaaS of Apps Are Adopted And Managed By Individuals and Business Units, Not IT
82% of SaaS Apps are Adopted by Business Users - What Does It Mean for Security?
Zylo, a leader in SaaS Management Platforms, recently released their 2023 SaaS Management Index Report. In it, Zylo researchers provide data, trends and actionable insights from their database of SaaS spend, license and usage data. The most notable of these findings–a staggering 69% of SaaS spend and 82% of SaaS apps by number are adopted and managed by individuals or business units, not IT.

This is not surprising to the Valence Security team, as we typically find thousands of employee-owned applications and SaaS-to-SaaS integrations (and their associated misconfigurations) when we do our initial security assessments with our customers. These apps and integrations often fly under the security team’s radar, circumventing security review and ongoing management.
Given this decentralized state of SaaS adoption and management and the increased risks it poses, it ultimately makes sense to decentralize risk remediation as well. The two keys to this are automation and collaboration.
Automation is critical since most CISOs and their teams are stretched thin with their budgets and resources. They don’t just want visibility into their SaaS risks (yet another attack surface to worry about) without the ability to quickly remediate them in a way that doesn’t require additional personnel, time or skill sets.
Valence Security provides automated remediation workflows that can, depending on the security team’s processes, either fully or partially automate the remediation of risks based on easy-to-set policies. These risks can include misconfigurations, overly-privileged SaaS-to-SaaS integrations, ungoverned external data shares, and users who are unmanaged by the corporate identity provider or who don’t have security guardrails like MFA in place.
It is also important for security teams to be able to engage with business users to better understand the context in which those users are adopting and using SaaS applications and SaaS-to-SaaS integrations. This avoids a situation where security decisions are made without business user input, which can disrupt business continuity and the fast pace of SaaS adoption.
Valence security’s automated workflows enable security teams to collaborate with business users to identify and reduce risks. By simply asking users to either remediate risks themselves or provide the business context, the security team can understand the business case without disrupting the business. This creates opportunities for security teams to build a reputation as business enablers, not blockers. Educating business users on proper SaaS security hygiene best practices sets up both parties for success.
Zylo researchers also found that the total number of SaaS applications of all types is growing rapidly, with the average organization adding six apps to their portfolio every month. This suggests a highly dynamic SaaS environment. As new applications are added each month, the risk that comes with new SaaS-to-SaaS integrations, data shares, users, and potential misconfigurations, grows as well.

As a result, security teams need solutions that don’t just provide a snapshot of their organization’s SaaS risk posture and then be done with it, but need ones that provide continuous visibility into their ever changing SaaS ecosystem and continuous remediation of those risks, something that the Valence platform was designed to provide.

Finally, this rapid growth in organizations’ SaaS ecosystems also results in unused SaaS licenses that are costing each organization a staggering $17 million per year on average, according to researchers at Zylo.
When employees leave an organization, SaaS applications and integrations are often abandoned. Perhaps they have outlived their usefulness, or it didn’t occur to employees to offboard apps and integrations after an unsuccessful POV. This scenario adds to this unnecessary cost and expands the organization’s attack surface.
Valence enables security teams to quickly eliminate unused SaaS applications and integrations, reduce external data oversharing, adjust user privileges, or remove unused user accounts directly from the Valence UI, thereby saving money and reducing risk.
Read the Zylo report
Valence Security ThreatLabs Alert: Salesforce Risk

Valence Security ThreatLabs Alert: Brian Krebs from Krebs on Security has recently posted that numerous organizations, including banks and healthcare providers, are leaking sensitive info from public Salesforce Community websites due to misconfiguration. This allows unauthenticated users to access private records.Recent cases like the Vermont state and Washington D.C. government exposed sensitive data such as names, SSNs, and bank account info. Salesforce advises customers to use their Guest User Access Report Package and follow best practices when configuring guest user profiles. As SaaS security professionals, Valence Security is committed to continuously enhancing security for Salesforce customers.
Article
Brian Krebs
April 27, 2023
A shocking number of organizations — including banks and healthcare providers — are leaking private and sensitive information from their public Salesforce Community websites, KrebsOnSecurity has learned. The data exposures all stem from a misconfiguration in Salesforce Community that allows an unauthenticated user to access records that should only be available after logging in.
Salesforce Community is a widely-used cloud-based software product that makes it easy for organizations to quickly create websites. Customers can access a Salesforce Community website in two ways: Authenticated access (requiring login), and guest user access (no login required). The guest access feature allows unauthenticated users to view specific content and resources without needing to log in.
However, sometimes Salesforce administrators mistakenly grant guest users access to internal resources, which can cause unauthorized users to access an organization’s private information and lead to potential data leaks.
Until being contacted by this reporter on Monday, the state of Vermont had at least five separate Salesforce Community sites that allowed guest access to sensitive data, including a Pandemic Unemployment Assistance program that exposed the applicant’s full name, Social Security number, address, phone number, email, and bank account number.

This misconfigured Salesforce Community site from the state of Vermont was leaking pandemic assistance loan application data, including names, SSNs, email address and bank account information.
Vermont’s Chief Information Security Officer Scott Carbee said his security teams have been conducting a full review of their Salesforce Community sites, and already found one additional Salesforce site operated by the state that was also misconfigured to allow guest access to sensitive information.
“My team is frustrated by the permissive nature of the platform,” Carbee said.
Carbee said the vulnerable sites were all created rapidly in response to the Coronavirus pandemic, and were not subjected to their normal security review process.
“During the pandemic, we were largely standing up tons of applications, and let’s just say a lot of them didn’t have the full benefit of our dev/ops process,” Carbee said. “In our case, we didn’t have any native Salesforce developers when we had to suddenly stand up all these sites.”
Read the full Krebs on Security article.
Valence Joins Microsoft for Startups Pegasus Program

Valence Security is thrilled to be part of the Microsoft for Startups Pegasus Program! A big thank you to Microsoft for consistently supporting the startup ecosystem with programs like these. Here is their blog post:
Unlocking opportunities by bridging the gap between startup solutions and enterprise challenges
Hans Yang, General Manager, Microsoft for Startups
May 3, 2023
Today we are excited to unveil the Microsoft for Startups Pegasus Program, which connects growth-stage startups to thousands of Microsoft’s top customers. The program is an extension of our Founders Hub platform and provides startups additional support by driving top-line revenue for those that have already achieved product-market fit in industries, including AI, health and life sciences, cybersecurity, and retail. The program acts as a matchmaker, identifying enterprise customers with business challenges and connecting them with the right startup solutions.
In pilot, the program has already helped over a hundred startups land enterprise customers, with an average deal size of $350,000.
“Many startups struggle when it comes to enterprise sales,” said Andy Pandharikar, founder and CEO of Commerce.AI. “Working with Microsoft for Startups helps us understand how enterprise customers look at and purchase new innovative products, and through this program we have been able to close nearly $1 million in deals.”
3 out of 4 Employees Sidestep IT, Bring Their Own Tech

According to a Gartner® Press Release, “by 2027, 75% of employees will acquire, modify, or create technology outside IT's visibility, up from 41% in 2022.”1 Much of this trend is driven by the accelerated adoption of SaaS applications by business owners without the involvement of IT or cybersecurity teams, especially due to the rise of remote work following the COVID pandemic.
This trend places a greater burden on CISOs to reconsider their cybersecurity strategies. It’s necessary to take into account wider business needs beyond just security concerns. By including the input of the business users who are adopting and using SaaS applications, security decision making can be more aligned with the business.
And what if the sprawling mesh of SaaS applications, integrations, data and users isn’t addressed by CISOs? As more employees adopt or manage SaaS applications outside of IT's purview, the risk of malicious attacks, insider threats and unintended exposure increases. Employees are increasingly introducing risks by consenting to unauthorized third-party integrations via OAuth and third-party apps, sharing data with external collaborators, and creating new accounts without proper authentication such as SAML or MFA.
These risks can leave organizations vulnerable to the types of SaaS breaches that have occurred multiple times over the past year. This includes the Jan. 23 CircleCI breach of GitHub customer data that occurred due to a compromised GitHub OAuth token.
To address these challenges, IT organizations must shift their role from owning risk remediation to risk remediation advisors. The role of the CISO is evolving from ensuring compliance through security policies to becoming more of a risk management advisor. CISOs must work closely with business owners to identify and manage risks associated with the adoption of SaaS and develop a cybersecurity strategy that aligns with the organization's broader goals and objectives.
As per a Gartner Press Release, “90% of employees who admitted undertaking a range of unsecure actions during work activities knew that their actions would increase risk to the organization but did so anyway”.2 This compounds the prediction that kicked off this post - that 3 out of every 4 employees will adopt technology without IT or security in the loop.
So, to recap: 75% of employees are predicted to adopt technology without telling IT, and 90% of employees regularly take risks they know they shouldn’t. That’s a recipe for something, but it isn’t success.
There are ways to bring employees in the loop without taking away their ability to make the most productive technology choices. By automating security policies, starting a conversation between employees and security is easy. Rather than blocking employee choices, an automated policy can act as guardrails by asking for context and business justification before taking any action. If the employee doesn’t respond in a pre-defined timeframe, the automated policy can remediate the risk.
Once employees become part of the risk decision-making process, perhaps a future where 75% of employees make choices on their own won’t be a foregone conclusion. Employees can’t be faulted for trying to get their jobs done with the tools and the knowledge they have. By equipping business users with the necessary knowledge and skills to improve security posture, security teams won’t be on their own either.
In conclusion, by combining SaaS Security Posture Management (SSPM), with automated policy enforcement, security teams can enforce zero-trust security principles, least privilege access, and other security best practices, across their business critical SaaS applications like GitHub, Salesforce, Slack, Microsoft 365, Atlassian, and Google Workspace. This can reduce the risk of SaaS misconfigurations, third-party integrations, oversharing of data, unmanaged users, and privilege creep. This combination can educate users on SaaS security best practices while enhancing business productivity.
-------------------------------------
1Gartner Press Release, Gartner Unveils Top Eight Cybersecurity Predictions for 2023-2024, March 28, 2023. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved
2Gartner Press Release, Gartner Unveils Top Eight Cybersecurity Predictions for 2023-2024, March 28, 2023. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved
Detecting Risky Behavior with Microsoft and Valence

Valence leverages of Microsoft’s new risk signals for human and non-human users
The Microsoft Azure AD team has been busy building identity protection features and making them available via the Microsoft Graph REST API. Valence has been collaborating with the Azure AD team – helping to bring new capabilities to detect Risky Users and Risky Service Principals into our SaaS security platform.
Detecting Risky Business
Microsoft’s Identity Protection feature automates the process of detecting identity-based risks for both human users and non-human service accounts and makes it possible to export these detections to other tools. What kinds of risks are we talking about here? A few examples:
- Impossible travel
- Anonymous IP use (TOR, VPN, etc)
- IPs associated with malware and botnets
- Leaked passwords
- Brute-force login attacks
As you might suspect from the examples above, Microsoft uses both internal and external threat intelligence sources to inform these detections. Others use basic tried-and-true heuristic techniques to detect risky activity.
Risky Users
The Microsoft Graph riskyUsers API endpoint tells us the risk state (at risk or not), the risk level (high, medium, low) and any specific risks detected. Every user with detected risks in the Azure AD tenant is listed by this API call. This endpoint also makes it possible to retrieve results for specific users and to filter on properties, like the risk level. Finally, the riskyUsers endpoint can provide the history for any user as well, a feature useful for SOC analysts and incident response teams.
Remediating identity-based breaches has become critical over the past few years. As an example, in the Uber breach that occurred last September, the attackers were able to abuse and bypass MFA without triggering any alerts seen by IT or security. They used stolen credentials to get into Uber systems and pivot to a large, centralized password database used by IT and security, including high-privilege admin credentials. These attackers went from one set of credentials belonging to a contractor, to all the company's credentials and data without being noticed. Uber only discovered the incident when the attacker posted to their internal Slack to taunt them.
Risky Service Principals
Experienced penetration testers know that service accounts are excellent targets for credential theft and lateral movement. Service accounts often need high levels of access to sensitive workloads, but can’t have security features like multi-factor authentication enabled, since they’re ‘machine-to-machine’ accounts – used by scripts, applications and third-party software without human intervention. The Microsoft Graph riskyServicePrincipal API endpoint provides insights into risky non-human identities.
The problem with service accounts is that they have to be able to authenticate without human intervention. That means the passwords or auth tokens must be stored somewhere. In 2022’s Heroku, Travis-CI, Github incident, attackers discovered Github and Travis-CI auth tokens in Heroku’s systems and used them to access and explore private files and repositories.
Risk Detection and Valence
The benefit of bringing Microsoft risk signals into the Valence platform isn’t just convenience. Valence correlates risk signals from all supported SaaS platforms into one place, giving security teams the big picture. A single case of abnormal travel could be a false positive, so it’s difficult to draw a conclusion without more information.
In contrast, what if that abnormal travel detection was accompanied by compromised credentials and three new Salesforce integrations - all in the same hour, from the same user? That’s a much stronger signal that is probably a better use of someone’s time than chasing down isolated detections. It’s also a pattern that would have been tough to spot without a platform like Valence which correlates all these events, attributing them to a single employee.
There are other benefits to having a more complete picture of SaaS use. Investigators can more clearly and quickly see the breadth of an incident. Business users can get a better understanding of how SaaS applications are being used, and can perhaps spot inconsistencies. Those inconsistencies could go two ways - reducing SaaS use where it’s not needed, or increasing it where there is a clear productivity gain.

This is all made possible through the visibility and correlation of the SaaS data, combined with the ability to directly engage SaaS users to understand their use cases and business justifications.
Valence will continue taking opportunities to ingest risk detections from various platforms. This data, combined with inputs from business users will help security teams and SaaS application owners better understand how to optimize and secure their SaaS use.
Looking forward, Valence will continue to work with the Microsoft Azure AD team to feed and manage the risky signals based on risk indications from other platforms and inputs from other SaaS applications and from the business users (using our collaborative business user engagement platform) to “close the loop” and enrich the data in the Microsoft platform.
Read the Microsoft Blog Post
Valence 2023 RSA Conference Survival Guide

RSA is a busy time for security folks. With so many people to meet and events to attend it’s easy to overlook some basic—but critical—planning strategies. That’s why we thought it’d be helpful to put together a primer on how to not only survive but thrive at this year’s conference.
Before we jump into the survival guide, we wanted to let you know that we’ll be out in force at RSA this year!
In case you missed it, Valence was chosen as a top 10 finalist in the 2023 Sandbox competition. It’s a terrific honor and we could not be more excited. Yoni Shohet, CEO and Co-Founder of Valence will present our SaaS security solution live in-person on Monday, April 24 at the Innovation Sandbox.
Additionally, members of the Valence team will be at YL Ventures' annual cocktail party.
Join the teams from YL Ventures along with their portfolio companies Cycode, Eureka Security, enso.security, Opus Security, Satori, Spera Security, and Vulcan Cyber.
This is always a great opportunity to unwind and talk shop with some of the industry’s brightest minds. Come have a cocktail with the Valence Security team—you won’t want to miss it!
Date/Time: April 26, 6pm PDT
Location: Novela, 662 Mission Street
Register: https://lnkd.in/gpbT_3Tb
Identify Your Conference Goals
What do you really want to accomplish at RSA? The RSA Conference is one of the largest and oldest cybersecurity conferences and has far more opportunities than any single person can take advantage of. The good news is that, since it is spread across 4-5 days, it’s possible to do a bit of everything. Here are some suggestions and examples:
Networking: make connections on LinkedIn, Twitter, and Mastodon, etc. Then plan to meet your connections in person. If you don’t put it on your calendar though, it might not happen, so reach out and set a time and place for in-person meetings.
Learning: Attend talks, take copious notes, and ask lots of questions - even ones you might think are dumb! I can’t emphasize this point enough: don’t be scared to ask questions. Something you might think is the dumbest question could lead to good conversation, new connections, and even new opportunities. Talk to speakers, trade business cards—in general, make your presence known, and soak up as much good information as you can.
Prospecting: if you’re looking at RSA as an opportunity to engage prospects, do so wisely. Engage in authentic conversations, offer real-world advice, and share your expertise with interested parties. See my previous suggestion on asking questions during talks. If you ask good, thought-provoking questions, it’s possible leads could come to you following the talk to continue the conversation you started! Note that you’ll need a full pass to do this - a lot of vendors tend to go for expo-only passes, which won’t get you into talks. One more point - truly ask questions - don’t put your hand up to make a statement.
Hiring: looking for a job? Scope out events put on by companies that are hiring. Try to speak to someone at the company in person to fast-track the hiring process. Shaking hands, looking people in the eye, and explaining your superpowers is a great way to gain an advantage over other applicants!
Boozing: It goes without saying that there’s a fair amount of adult beverage consumption at the conference. It probably should not be your goal to get hammered, it’s entirely possible to do so. Just beware that your personal reputation as well as the image of any organizations you work for or represent are also attached to your actions!
Remember: the conference is crowded with sales reps, product experts, and anyone else working in the industry. The opportunity to make real connections with peers is one of my favorite things about in-person conferences.
Prepare for Meetings
People might not know how much time and effort they should spend preparing for meetings at RSA. This is totally reasonable! After all, you’re one person with a finite amount of time/energy and chances are you’re already slammed. Here are a few tactics to keep in mind:
Business cards: bring business cards—lots of them—or some other way for folks to easily get in touch with you after the conference. This sounds obvious, but I can tell you from experience that dishing out business cards left and right can deplete your supply quicker than you’d like!
Meetings: there are plenty of opportunities to meet people casually at RSA, but if you don’t want to leave it up to fate, make sure to schedule meetings now! RSA calendars fill up fast and you don’t want to miss a chance to chat with the right folks at the right time
Socialize: the conference doesn’t have to be all business. Take time to relax with a peer or group of friends. Even meeting with a vendor and learning about an interesting new solution is a great way to keep your mind engaged and your energy levels high
Just say no: Don’t say yes to a meeting simply to be polite—you’re wasting time for you and the other person. I’ll admit there are temptations: I once said yes to a meeting in exchange for a 2nd gen iPod Nano (I was weak-willed and poor at the time). In my defense, the product was really cool, but I knew there was no way I’d get my company to pay for it
Encourage Teamwork
One person is not enough to take advantage of everything RSA has to offer. This is where teamwork comes into play. Make a plan with your team so when the conference is over everyone can share insights and opportunities
Notes: everyone should be ready to take lots of notes and share what they’ve learned. There are so many ways to incorporate what you learn and experience into future business initiatives—emphasize to your team that it’s super important to soak up as much intel as possible
Vendors: hundreds of vendors will be at RSA. If you’re looking at products, or even want to see what a competitor is up to, tell your team to divide and conquer! Divide up different parts of the conference that each team member will cover and then report back.
Meeting with colleagues or friends: decide on a common meeting place beforehand. Locate the W, St. Regis, Marriott, and InterContinental on a map—these are the most likely locations outside Moscone where you’ll have meetings. They’re all easily walkable from Moscone if you know what direction to go in. San Francisco is dense, and there are duplicates of some stores, hotels, and restaurants. Consider that your first search result might not be the one right next to Moscone that everyone else in your WhatsApp/Signal group is talking about going to!
Preparation
Spend some time exploring maps around Moscone before you go. Can you walk from your hotel to Moscone? You should know the answer and how long it will take!
The conference is spread across four main areas:
North Moscone: Registration is here, starting on Saturday, April 22 and ending Tuesday evening (hours). You can take escalators down to the North Expo floor. Last year, the analyst briefing rooms were upstairs here. Previously, they had been right at the bottom of the escalators. Note: the doors to Yerba Buena Gardens will let you out, but not back in!
South Moscone: You can register here, too. Take the escalators down to the South Expo floor. There are also usually talks here. There’s a passageway underneath the streets between the North and South Expo areas that has bathrooms and more expo space. A sky bridge connects North and South Moscone.
West Moscone: You’ll find some media booths and the RSA bookstore here. Some authors will be signing their books! On the second and third levels, you’ll find most of the talk tracks. There will be coffee, water all the time, and snacks are periodically brought out.
The Marriott Marquis: This year, only training is in the Marriott - the early stage expo and Innovation Sandbox are both in South Moscone. Don’t confuse the Marquis with the Marriott in Union Square when punching in rideshare directions!
Explore the Expo
If you want to check out specific vendors, download the expo floor plans before you go! Also: the RSA website will let you add talks you want to see to an agenda and add vendors to a list of favorites. This can give you a handy list that you can use to map out where you need to go and on what days.
The expo this year is bigger than I can ever recall - over 400 vendors will have a booth! There is typically also a foldout map in the badge hanging around your neck, so be sure to pull that out if you get lost! Both expo areas also have maps at the entrance to North and South Moscone on the lower levels, and each area is laid out in a numbered grid that will be labeled with signs hanging from the ceiling.
Note that the Expo is open for a MUCH shorter period than the rest of the conference. It’s only open for two and a half days: a 2-hour welcome reception on Monday, 10am-6pm on Tuesday and Wednesday, and 10am-3pm on Thursday.
The Early Stage Expo has an even shorter schedule: a 2 hour welcome reception on Tuesday (the CyBEER Ops Networking Reception), with hours from 9:30am - 4:30pm on Wednesday and 9:30am - 3pm on Thursday.
Networking and Events
Many parties and events require advance registration and are limited. These aren’t officially linked to RSA, so you will have to go through vendors or organizations directly to register. Some of these fill up quickly so make sure you register ASAP if there are some you really want to go to. Sometimes you can get tickets to parties at the conference, or at a vendor’s booth.
Don’t assume external events will be within walking distance of Moscone. As RSA has increased in size, folks have been forced to go further and further away from Moscone to host private parties. The biggest of these external events is BSides San Francisco, which runs on Sunday and Monday. It’s hosted at the AMC Metreon 16, which is located right next to Yerba Buena Gardens, before you get to the Marriott Marquis.
Don’t cover every moment of your schedule with talks and meetings. If you know a lot of folks in the industry, there’s a good chance you’ll run into them and want to make some spontaneous plans. I find 4 or 5 talks I really want to go see and try to keep blocks of time on my calendar open. I also block off time to wander the expo floors.
Travel Tips
BladderOps: Always use the bathroom when the opportunity is presented, even if the need isn’t urgent. Nothing is worse than arriving at a meeting or talk and realizing that you have to pee like crazy. This goes for travel in general, not just attending a big conference.
BlisterOps: Unless you’re sure you can handle 80,000 steps with the footwear you’re bringing, plan on blisters. Bandages can be helpful to cover up spots where skin is getting chafed or rubbed raw. I travel with a mini first-aid kit that has bandages, aspirin, ibuprofen, etc.
LuggageOps: Unless you’re very determined not to take any swag, there’s a good chance you’ll need some extra room in your luggage to bring stuff home (e.g., I won a drone one year). One travel hack is that jeans (unless you spill something on them), don’t really get dirty like other clothing. Two pairs of jeans are plenty to get you through the whole week. You WILL want daily changes of socks, shirts, and underwear, however. All that walking gets schwetty.
💡Conference Hack: it’s a small risk, but you could leave with less socks and t-shirts than you need, and then pick some up from the expo area. Socks and t-shirts are very common swag.
PowerOps: Anker, UGreen, and Satechi GaN (Gallium Nitride) chargers are awesome, and take up MUCH less space. You can get away with just one brick half the size of a MacBook charger to charge your laptop, tablet, and phone. Also, if everything you have is USB-C, you can cut down on cables as well.
Portable batteries are nice to have. They make smaller 5000maH and 10000maH powerbanks that are light enough for pockets but can only recharge phones or tablets. You can also get a big honkin’ 20000maH+ powerbank that can even recharge a laptop, but make sure to check that you can charge your laptop via USB-C and that the output is high enough for your laptop to charge—some refuse to charge off lower output power sources. These can get VERY HOT, so beware. Probably give them some air while they’re charging at the highest rate
WeatherOps: It never hurts to bring an umbrella. SF weather is unpredictable. Even in April, it can get cool enough for a jacket in the evenings
Logistics
Do you need to be functional on Thursday or Friday? Or over the weekend following RSA? Make sure you schedule some time for rest. Have early morning plans? Don’t go out at night. Don’t go to parties. Think marathon, not sprint.
Plan for at least 30 minutes of walking time between meetings. If you’re walking from the back of the South Expo to a talk at Third Floor Moscone West, plan for about a 20–25-minute walk. Even between talk tracks—within—Moscone West, plan for 5-10 minutes of walking time. Wear comfy shoes. Plan on 15-20k steps if you’ve got a full schedule—I’m not even joking.
RSA is good about bundling similar talks close together, sometimes in the same room. Show up a little early to a talk you really want to see—there are limits to room seating and you won’t be able to get in as soon as it’s full. Note: you can’t camp in a talk track! They’ll clear the room, and you have to get back in line, even if you’re planning to watch another talk in the same track.
Uber and Lyft work well, but it’s often best to have them drop you off a block or so away. As you get closer to Moscone, it takes longer to drive than to walk. There are also scooters, provided they haven’t all been thrown into the bay by now.
Maintain Energy
Avoid getting sick and/or feeling beat down by keeping your immune system healthy. Hydrate and eat healthy. Hydrate during the flight and immediately after—airplanes recycle air so quickly and so often you could probably make jerky on them. Moscone has hydration stations near bathrooms, just like airports! Many hotels now have these as well, often one per floor, near the ice maker. How to know if you’re hydrated? With all this exercise and walking, you should be peeing CLEAR—like, barely a hint of any color. If not, drink more water.you
Take breaks outside. Yerba Buena Gardens is right there and is a great place to take some deep breaths and soak up some sunshine. Skip the parties. If you’re going to sustain full days of talks, exploring expos, and having meetings all over the place, you need a good break at the end of the day:
- Grab a quiet dinner with friends
- make some notes about the day
- catch up with social media and/or family back home
If you’re based on the East Coast, you might try to stay on East Coast time, that way there’s no adjustment when you go back home. If you’re from more than 3 time zones away—good luck…
Food Tips
Find restaurants at least 10 minutes away from Moscone—it will be quieter and easier to get a table. Just about everything, including restaurants, will be reserved for private meetings and parties by vendors. If you want to have a nice dinner, start scoping out restaurants and making reservations early.you
Places like Amber India are pretty much impossible to get into without a reservation. One exception is The Grove—it’s usually easy to get in and out for a quick meal or lunch meeting. Mel’s Drive-In is a great place to get an American-style breakfast that will keep you fueled throughout most of a crazy day.
I eat nothing but salads and the healthiest stuff I can find for every meal, because I know that, at any point, the group I’m with is going to decide to go to the bar where they serve 30 different kinds of sausage. I prepare for this moment by eating 100% not sausage the rest of the time.
Reduce Waste
Recycling is a lie: try to avoid single-use plastics and coffee cups as much as possible. Trash reduction isn’t the only benefit either—with nice, insulated containers, you can put hot coffee and cold water in your backpack, leaving your hands free! You can also save a ton of money over buying bottled water.
I bring a big, insulated water bottle with me, and a smaller insulated container for coffee or tea. Worst case, you can pick up a free reusable bottle from a vendor in the expo area. Don’t take swag unless you really think you’re going to use it. Most swag goes straight in the trash, so if it’s really garbage that no one wants, we should send that signal by not taking it. If we take it just to be kind, they’ll keep making it, bringing it, and putting it in the trash.
About the Conference
The RSA Conference is an annual cybersecurity conference that typically takes place in San Francisco, California. It is one of the largest and most well-known conferences in the cybersecurity industry, attracting thousands of attendees from around the world. The conference features keynote speakers, educational sessions, panel discussions, and an exhibition floor where vendors showcase their latest products and services related to cybersecurity. The conference is organized by RSA Security and covers a wide range of topics related to information security, including cryptography, cloud security, risk management, and emerging technologies. The conference serves as a forum for cybersecurity professionals to learn about the latest trends and best practices in the industry, as well as to network and share ideas with their peers.
About RSA’s Innovation Sandbox
The Innovation Sandbox is a competition that features some of the most innovative and promising early-stage cybersecurity startups from around the world. The competition is designed to provide a platform for these startups to showcase their innovative ideas, technologies, and products to the broader cybersecurity community.
During the competition, the selected startups have a chance to present their ideas and technologies in front of a panel of judges, which typically includes venture capitalists, industry executives, and security experts. The judges then evaluate the startups based on their innovation, market potential, and ability to address real-world cybersecurity challenges.
The winner of the Innovation Sandbox competition is selected based on a combination of judges' evaluations and audience voting. The winner receives recognition and exposure to potential customers, investors, and partners, as well as a trophy and other prizes.
Overall, the Innovation Sandbox is a valuable platform for early-stage cybersecurity startups to gain visibility, validation, and networking opportunities, as well as for the broader cybersecurity community to stay informed about the latest innovations and trends in the industry.
Valence Security is an Innovation Sandbox Finalist

The Innovation Sandbox is one of my favorite features at any security conference ever. Sure, it has highlighted some of the most innovative and exciting startups in cybersecurity, but I also love it for its entertainment value. Here’s one of my favorite presentations - Elevate Security, pitching their approach to security awareness, which, like Valence, has a user-focused approach.
Hugh Thompson, for as long as I can remember, has played the ever-exuberant and joyful MC for the event. He has some standup comedy chops, and it shows - he knows how to get the crowd excited and build up tension leading into the gauntlet each of the finalists has to run.
Here’s how it works. The top 10 finalists are chosen by a panel of judges from over 100 submissions each year. At the Innovation Sandbox event, each finalist will take the stage and has 3 minutes to pitch their company, team and product to the panel. What really ratchets up the drama here is that this is a strict 3 minutes. When the clock runs out, the microphone is cut!
Occasionally someone gets nervous and doesn’t finish before their time runs out. Regardless, after the presentation, the judges have a few additional minutes to ask the presenter follow-up questions. Then, the next finalist is queued up and introduced by Hugh.
After all 10 presentations have been completed, the judges have time to get up and visit some of the finalists’ booths (perhaps they’ll pick up a copy of the infographic from our latest research report) and to share thoughts with each other. At the end of the 90-minute event, the judges pick a winner, Hugh makes the announcement, and crowns the winner, Most Innovative Startup 2023.
In a market where funding and accolades have become scarce, the news of becoming an Innovation Sandbox finalist comes just a few months after Valence raised one of the strongest Series A rounds seen in the second half of 2022. If you’re not familiar with what Valence does, we’ll be representing SaaS Security at this event. This explainer video does a quick job (1:55) of explaining what we do.
I became an instant fan of the RSA Innovation Sandbox and have attended every event since my first year at RSA (2014). Words can’t express how excited I am to work for a company that’s a finalist this year.
Please take a moment to say hello if you see me there!
Read more about the RSAC 2023 Innovation Sandbox in their official press release on BusinessWire.
For press inquiries, contact:
Montner Tech PR
(203) 226-9290
About Valence Security
Valence Security is the first security company to offer collaborative remediation workflows that engage with business users to contextualize and reduce SaaS data sharing, supply chain, identity, and misconfiguration risks with scalable policy enforcement and automated workflows.
With Valence, security teams can secure their critical SaaS applications and ensure continuous compliance with internal policies, industry standards and regulations, without impeding business productivity or the speed of SaaS adoption.
Cybersecurity Excellence Awards 2023: Valence Brings Home the Gold, Twice Over

Valence Security has been awarded Gold in not just one, but two categories in the prestigious Cyber Security Excellence Awards.
Our first gold was for Best Cybersecurity Startup, which we owe in large part, to tackling the complex problem of surfacing SaaS security risks. These issues are buried deep below the surface of SaaS. Individual employees often introduce these issues, unaware of the risks they create when integrating two SaaS products.
We didn’t stop there. Our second gold was for SaaS Security Posture Management. Within this category, we differentiate by going beyond simply surfacing issues. We don’t leave our customers with the task of manually remediating potentially hundreds or thousands of risky or unnecessary SaaS integrations. We automate the process, saving customers hours, days, and weeks of labor.
We didn’t stop there. Simply tearing down SaaS integrations can be disruptive and could break critical business workflows. That’s why we introduced a collaboration into the Valence Security platform. Employees are prompted to explain and justify the need for these integrations. Disruptions are avoided and only unnecessary risks are eliminated.
Experience collaborative SaaS security that saves time and avoids employee disruption: the Valence SaaS Application Security Platform.
Dark Reading: Why Are Employees Integrating With Unsanctioned SaaS Apps?

As you may have noticed on your recent Zoom calls, the latest application update quietly added a slick little app-store sidebar to the right-hand side of your session screen. This feature enables any business user within your organization to integrate the software-as-a-service (SaaS) apps showcased in the sidebar with a click of a button — without so much as disrupting their Zoom session.
While seemingly innocuous, this feature highlights the greatest strength and one of the greatest SaaS security risks — the ability for anyone within an organization to adopt, configure, and manage SaaS applications. While this process may be convenient and conducive to fast business enablement, by design it also bypasses any internal security review processes. This leaves your security team with no means of knowing which apps are being adopted and used, whether they may have security vulnerabilities, if they are being used in a secure way, or how to place security guardrails around their use. Enforcing zero-trust security principles becomes almost impossible.
Shared Responsibility
But before you chastise your employees for irresponsibly adopting SaaS applications, you need to realize they're being constantly encouraged by vendors to install more apps and adopt new features. Yes, the applications themselves often serve critical business needs, and yes, your employees inherently want to adopt them quickly, without enduring a protracted security review. Yet, they're doing so because — whether they realize it or not — they're being aggressively marketed to by savvy application vendors, who often mislead users into believing they're following security best practices. Just because users are bombarded during installation with consent screens meant to give them pause and encourage them to read about their rights and responsibilities doesn’t mean users are actually reading these screens, or that the consent language is transparent, accurate, or complete.
Beyond touting their application's brilliant new features, these vendors are also constantly telling your business users and security teams their applications are secure, their infrastructure is secure, that 24/7 uptime is 99.999% assured, and they guarantee that their employees won’t have access to user's data, etc. However, they typically downplay or even fail to mention their shared responsibility model of security, where they're only responsible for the security of the platform infrastructure, and that securing usage against account takeovers and data loss are the customer's responsibility.
This is especially problematic as most security breaches are due to SaaS misconfiguration or user error, not code vulnerabilities, and your users are ill-equipped to defend against these risks by themselves. Even large and respectable vendors such as GitHub, HubSpot, LastPass, Mailchimp, Okta, and others that were recently victims of breaches, are susceptible to misconfigurations and misuse. You should always trust, but verify no matter the vendor.
Never Assume
In other cases, security is often just assumed. Take application marketplaces operated by well-known brands, for example. Vendors have neither the desire, nor the financial incentive or capacity, to vet the security posture of every third-party application being sold on their marketplaces. Yet to grow the business they can lead users to believe that anything sold there maintains the same level of security that the marketplace vendor does, often by omission. Likewise, marketplace descriptions may be written in such a way as to imply their application was developed in collaboration with or endorsed by a major, secure brand.
The use of application marketplaces creates third-party integrations that carry the same risks as those that led to many of the recent attacks. During the GitHub attack campaign in April 2022, attackers were able to steal and abuse legitimate Heroku and Travis-CI OAuth tokens issued to the well-known vendors. According to GitHub, the attackers were able to leverage the trust and high access granted to reputed vendors to steal data from dozens of GitHub customers and private repositories.
Similarly in December 2022, CircleCI, a vendor specializing in CI/CD and DevOps tools, confirmed some customer data was stolen in a data breach. The trigger to the investigation was a compromised GitHub OAuth token. Based on the investigation by the CircleCI team, the attackers were able to steal a valid session token of a CircleCI engineer, which allowed them to bypass the two-factor authentication protection and gain unauthorized access to production systems. They were then able to steal customer variables, tokens, and keys.
Lure of Frictionless Adoption
Vendors also build their platforms and incentive programs to make adoption as easy as agreeing to a free trial, a perpetual free service tier, or swiping a credit card, often with seductive discounts to try and buy without obligation.
It's in the interest of the vendors to get users hooked quickly on any cool, new functionality by removing all friction to adoption, including bypassing IT and security team reviews in the process. The hope is that even if security teams grow wise to the use of an application, it will prove too popular with business users and too critical to business operations to remove it. However, making adoption overly easy can also lead to a proliferation of unused, abandoned, and exposed apps. Once an app is rejected during a proof of concept (PoC), is abandoned due to waning interest, or the app owner leaves the organization, it can often remain active, providing an expanded and unguarded attack surface that places the organization and data at elevated risk.
While it's important to educate your business users on SaaS security best practices, it's even more important to fight indiscriminate SaaS sprawl by teaching them to evaluate more critically the siren song of SaaS vendors about easy deployment and financial incentives.
Further, security teams should also adopt tools that can assist in managing SaaS misconfiguration risks and SaaS-to-SaaS integrations. These tools enable users to continue to adopt SaaS applications as needed while still vetting new vendors and integrations for security and establishing much-needed security guardrails.
Read the Article in Dark Reading
Reimagining zero trust for modern SaaS

The concept of zero trust – as a way to improve the security of and access to an organization’s network, systems, and data – has gained traction in recent years. The basic premise is that no user or device should be trusted by default and all access to data and resources should be granted based on critical business need – and such need should be continuously verified.
While zero trust can be an effective approach to security, it can also present some challenges, particularly when it comes to implementing it for software as a service (SaaS) due to the fast pace of its adoption, distributed ownership of SaaS applications across organizations, and the shared responsibility model between a SaaS vendor and a customer.
The traditional approach to SaaS security challenges has been to use a cloud access security broker (CASB) and/or identity provider (IdP) to manage access to SaaS applications. IdPs are used by many organizations to centrally authenticate human users into an application or system, enforcing many strong authentication methods.
Some organizations also add a CASB to sit between users and the services they access, enforcing granular security policies and controls to ensure that only authorized users can access specific resources, and to protect against malicious activity. These combined solutions help to simplify the implementation of zero trust principles to SaaS applications such as Microsoft 365, Salesforce, ServiceNow and Workday, and make it easier to manage access and security at the points of both authentication and authorization.
CASBs and IdPs alone or in tandem, however, are still inadequate since SaaS applications have become increasingly more complex, including collaboration and automation elements that could “break” the zero trust model, such as:
- Third-party integrations like OAuth, APIs and low/no-code – non-human identities that are not governed by existing IdP solutions and grant direct programmatic access for third-party vendors to core SaaS applications, without applying strong human authentication methods
- External data sharing settings that enable the sharing of files with external collaborators in OneDrive, SharePoint, Google Drive, Box, Dropbox, etc., the forwarding of emails to external users and publicly sharing sensitive data repositories (i.e., source code repositories)
- External user identities that allow collaboration with contractors, vendors and other external parties which enable users to access business-critical resources from unmanaged devices without enforcing the corporate identity provider and security guardrails
Additionally, SaaS applications are much more complex than traditional applications and they allow business users autonomy to manage them without IT in a democratized model. These SaaS applications encourage users to perform what in the past would have been considered administrative actions, resulting in potential misconfigurations.
Each SaaS application has its own permission model and set of complex configurations, most of them can impact the security posture of the SaaS application. This almost makes it easy for users to mistakenly configure SaaS applications to break the zero trust model. For example, in many organizations Salesforce administrators create local users in their tenant to enable automation scripts and service accounts, which allow them to improve business processes. If such accounts aren’t properly configured, they may access Salesforce directly, without authenticating through the IdP, hence bypassing a critical security control.
Finally, security teams lack control over the underlying infrastructure of their SaaS application. When using on-prem systems, an organization has complete control over the hardware, software, and network configuration, which makes it easier to implement security controls and enforce policies. Due to the shared responsibility model for securing SaaS services, the infrastructure is managed by the service provider, which can make it more difficult if not impossible to apply zero trust principles to it. Plus, without visibility into who these security vendors are, security teams don’t even have an opportunity to vet their security posture. This limits security teams to managing configurations that were enabled by the SaaS vendor, which in many cases may not be sufficient to enforce the desired policies.
What is the key to building a scalable zero trust model for the modern SaaS?
Engagement and collaboration with the business users who adopt, manage and use SaaS applications on a daily basis. By working closely with them, security teams can gain visibility into all applications across their organization’s diverse and complex SaaS environment and ensure zero trust security guardrails are in place without disrupting either the pace of adopting and configuring SaaS applications or the pace of the business itself.
Without such engagement, security teams lack critical context into the day-to-day business use of these SaaS applications that is critical to securing SaaS services in a way that doesn’t disrupt the business. With it, they can gain valuable insights from business users, educate the entire organization on SaaS security best practices, and extend security resources to the entire organization by drawing those outside of the security team into SaaS security workflows and processes.
Read the Helpnet Article
CircleCI Says Hackers Stole Encryption Keys and Customers’ Secrets

CircleCI, a vendor specializing in CI/CD and DevOps tools, confirmed that some customer data was stolen in a data breach last month. The trigger to the investigation was a compromised GitHub OAuth token, which has been a popular attack vector that attackers leverage in the past few months, like many other breaches of developer-focused SaaS applications that the Valence Security Threat Labs team has discussed. Based on the investigation by the CircleCI team, the attackers were able to steal a valid session token of a CircleCI engineer, which allowed them to bypass the two-factor authentication protection and gain unauthorized access to production systems. The attacker was able to steal customer variables, tokens, and keys.
In this blog post, CircleCI recommends their customers to rotate their secrets, including OAuth tokens, Project API Tokens, SSH keys, and more.
Ensuring proper management of SaaS security risks such as ungoverned SaaS-to-SaaS third-party integrations like OAuth keys, API tokens, etc. is key to protect critical organizational data. Implementing a SaaS security solution like Valence can be useful in continuously monitoring for SaaS misconfigurations and misuse as well as right-sizing privileges of both human and non-human identities.
Read the full TechCrunch article
CircleCI, LastPass, Okta, and Slack: Cyberattackers Pivot to Target Core Enterprise Tool

In early January, development-pipeline service provider CircleCI warned users of a security breach, urging companies to immediately change the passwords, SSH keys, and other secrets stored on or managed by the platform.
The attack on the DevOps service left the company scrambling to determine the scope of the breach, limit attackers' ability to modify software projects, and determine which development secrets had been compromised. In the intervening days, the company rotated authentication tokens, changed configuration variables, worked with other providers to expire keys, and continued investigating the incident.
"At this point, we are confident that there are no unauthorized actors active in our systems; however, out of an abundance of caution, we want to ensure that all customers take certain preventative measures to protect your data as well," the company stated in an advisory last week.
The CircleCI compromise is the latest incident that underscores attackers' increasing focus on fundamental enterprise services. Identity services, such as Okta and LastPass, have disclosed compromises of their systems in the past year, while developer-focused services, such as Slack and GitHub, hastened to respond to successful attacks on their source code and infrastructure as well.
The glut of attacks on core enterprise tools highlights the fact that companies should expect these types of providers to become regular targets in the future, says Lori MacVittie, a distinguished engineer and evangelist at cloud security firm F5.
"As we rely more on services and software to automate everything from the development build to testing to deployment, these services become an attractive attack surface," she says. "We don't think of them as applications that attackers will focus on, but they are."
Identity & Developer Services Under Cyberattack
Attackers lately have focused on two major categories of services: identity and access management systems, and developer and application infrastructure. Both types of services underpin critical aspects of enterprise infrastructure.
Identity is the glue that connects every part of an organization as well as connecting that organization to partners and customers, says Ben Smith, field CTO at NetWitness, a detection and response firm.
"It doesn't matter what product, what platform, you are leveraging ... adversaries have recognized that the only thing better than an organization that specializes in authentication is an organization that specializes on authentication for other customers," he says.
Developer services and tools, meanwhile, have become another oft-attacked enterprise service. In September, a threat actor gained access to the Slack channel for the developers at Rockstar Games, for instance, downloading videos, screenshots, and code from the upcoming Grand Theft Auto 6 game. And on Jan. 9, Slack said that it discovered that "a limited number of Slack employee tokens were stolen and misused to gain access to our externally hosted GitHub repository."
Because identity and developer services often give access to a wide variety of corporate assets — from application services to operations to source code — compromising those services can be a skeleton key to the rest of the company, NetWitness's Smith says.
"They are very very attractive targets, which represent low-hanging fruit," he says. "These are classic supply chain attacks — a plumbing attack, because the plumbing is not something that is visible on a daily basis."
For Cyberdefense, Manage Secrets Wisely & Establish Playbooks
Organizations should prepare for the worst and recognize that there are no simple ways to prevent the impact of such wide-ranging, impactful events, says Ben Lincoln, managing senior consultant at Bishop Fox.
"There are ways to protect against this, but they do have some overhead," he says. "So I can see developers being reluctant to implement them until it becomes evident that they are necessary."
Among the defensive tactics, Lincoln recommends the comprehensive management of secrets. Companies should be able to "push a button" and rotate all necessary password, keys, and sensitive configuration files, he says.
"You need to limit exposure, but if there is a breach, you hopefully have a push button to rotate all those credentials immediately," he says. "Companies should plan extensively in advance and have a process ready to go if the worst thing happens."
Organizations can also set traps for attackers. A variety of honeypot-like strategies allow security teams to have a high-fidelity warning that attackers may be in their network or on a service. Creating fake accounts and credentials, so-called credential canaries, can help detect when threat actors have access to sensitive assets.
In all other ways, however, companies need to apply zero-trust principles to reduce their attack surface area of — not just machines, software, and services — but also operations, MacVittie says.
"Traditionally, operations was hidden and safe behind a big moat [in the enterprise], so companies did not pay as much mind to them," she says. "The way that applications and digital services are constructed today, operations involve a lot of app-to-app, machine-to-app identities, and attackers have started to realize that those identities are as valuable."
Read the article on Dark Reading
GitHub Accounts Breached…Again

Over the holiday weekend, the popular messaging app vendor Slack was notified of a breach of their GitHub account. Upon investigation it was determined that stolen Slack employee tokens had been used to gain access to private Slack code repositories. Fortunately, no customer data was compromised.
Sound familiar? In the past year, there has been a spike in the number of attacks targeting GitHub customers. We wrote a blog post in April of last year about a breach where attackers had stolen OAuth user tokens issued to third-party vendors, Heroku and Travis-CI which were then used to download private data repositories from dozens of GitHub customers, including GitHub itself. And this adds to Okta disclosing it’s code repositories were hacked, 130 Dropbox GitHub repositories that were stolen, and many more security alerts such as the recent phishing campaign disclosed by GitHub.
It is not surprising that these types of breaches occur given the ubiquity of GitHub use by software developers. As organizations are moving to the cloud and utilizing SaaS applications such as GitHub, the shared responsibility model requires them to continuously ensure proper security controls are enforced to protect their data. More users within the organization have administrative and sensitive privileges and security teams need to ensure they properly collaborate with them to implement security best practices.
To strengthen your GitHub security posture, it’s recommended to ensure:
- Strong authentication with SAML, MFA or password policies
- Reduce exposed publicly exposed GitHub source code repositories
- Eliminate unnecessary SSH keys, OAuth Apps, GitHub Apps and Personal Access Tokens (PATs)
- Enforce least privilege for human and non-human identities
- Manage external access by contractors and third-party integrations using API access
GitHub is not the only SaaS application that has been targeted by malicious actors and to ensure you’re not caught up in the next breach, it’s recommended to implement a SaaS security platform that will monitor your SaaS mesh and help with SaaS security posture management (SSPM), SaaS-to-SaaS governance, data protection and security identities.
Using SSPM to Start Resolving SaaS Security Issues

SaaS applications have become deeply embedded in every business function, enhancing business productivity and efficiency within forward thinking organizations. The ease and speed by which applications can be activated encourages business users to adopt and interconnect them directly. This is often done without IT security oversight or security controls leaving businesses open to a number of SaaS security issues, risks and misconfigurations.
Security Issues Related to SaaS Integration
As a result of this indiscriminate adoption, management and use, SaaS applications have also opened a new attack surface consisting of a mesh of interconnected applications, users and data. This has resulted in a growing web of SaaS security issues such as:
- Insecure, inactive and over-privileged integrations
- Randomly used and forgotten applications
- Security misconfigurations
- External or improper internal data sharing
- Ungoverned identities
- Over privileged users
This growing SaaS mesh can leave organizations vulnerable to data loss and account compromise. Recent Okta/Lapsus$, GitHub, and Mailchimp breaches highlight this growing risk and the fact that SaaS attacks are becoming a common threat vector.
How Can SSPM Help to Detangle the SaaS Mess?
After Cloud Security Access Broker (CASB) which were the first generation of SaaS security solutions, SaaS Security Posture Management (SSPM) solutions have recently emerged to address modern SaaS security challenges, but only solve part of the problem.
What is Saas Security Posture Management (SSPM)?
SaaS Security Posture Management (SSPM) supports automated monitoring for the security of SaaS applications. It is used primarily to minimize risky configurations and help ensure compliance.
SSPMs make it easier for organizations to ensure proper SaaS application configurations from the start and detect policy drift over the lifecycle of application use. In addition, they enable IT security teams to detect over-privileged user access, ensuring users have only the minimum privileges to access data that is necessary to remediate these SaaS security issues.
However, many security risks go beyond application configurations which current SSPMs focus on. SaaS applications empower business users to make decisions on a daily basis that can expose critical business data to attack. Existing solutions fall short in addressing such risks since they don’t understand business context. This context is required to properly address the risk of changes made by large organizations and business users without disrupting the natural flow of operations.
Securing SaaS Applications Properly Goes Beyond SSPM
IT and security teams often feel like they have to rely on strict security controls such as blocking collaborative features in SaaS applications, which could reduce the value of our innovative SaaS applications, ultimately impeding the business. Even worse, when security teams restrict the usage of popular SaaS applications like Slack, Microsoft 365 and Google Workspace, business users often find workarounds that allow them to accomplish their business goal. These workarounds may be accomplished with unsanctioned apps and methods that could create additional SaaS security issues and vulnerabilities.
Engaging with the users who adopt, use and manage each application in the first place is critical for security teams to determine which applications, integrations and configurations are business critical. Working with individuals is necessary for IT teams to maintain a reputation as collaborative security enablers, not the department of “no”. Unfortunately, existing SSPMs lack collaborative remediation workflows that incorporate user engagement.
Additionally, the scale of remediations across hundreds of applications is daunting since every application has different terminology, usage models, logic and privileges. By engaging with end users, IT departments can leverage the knowledge and efforts of the business users to remediate SaaS risks themselves while educating them on proper SaaS application security hygiene.
Choosing Valence Security
It is time for a new generation of SaaS security solutions that can understand business context and maintain visibility. There is a need for the ability to collaboratively remediate SaaS security issues across the SaaS mesh. Valence Security’s Collaborative Security Remediation Platform for SaaS has been built as a solution to bridge the gap between IT and end users.
We started Valence to deliver collaborative remediation workflows that engage with business users to contextualize and reduce SaaS data sharing, supply chain, identity, and misconfiguration risks with scalable policy enforcement and automated workflows.
With Valence, security teams can secure their critical SaaS applications like Microsoft 365, Google Workspace, Salesforce, and Slack and ensure continuous compliance with internal policies, industry standards and regulations, without impeding business productivity or the speed of SaaS adoption.
See the Valence Platform in action. Schedule a demo now.
Gartner Emerging Tech Impact Radar Reports

Valence Security is honored to have been mentioned as a SaaS Security Posture Management (SSPM) vendor in Gartner’s latest Emerging Tech Impact Radar: Cloud Native report and Emerging Tech Impact Radar: Security report. The latest SaaS security breaches at Okta and HubSpot point to the need for SaaS security solutions that go beyond Cloud Access Security Broker (CASB) capabilities.
In this report, Gartner states:
"Cloud access security brokers (CASBs) are addressing common SaaS security use cases, including shadow IT discovery, SaaS risk assessments, sensitive data protection, SaaS governance and compliance. However, there are security use cases that were not addressed, such as permissions management, especially SaaS administrator transactions and user life cycle management, including external users within content services platforms, social and collaboration software. SaaS security posture management (SSPM) addressed some of these gaps by providing continuous monitoring of SaaS risks identified in security misconfigurations, user and permission life cycle management, and SaaS app integrations risks with guided remediations. With the rise of SaaS security incidents such as those that occurred at Okta and HubSpot, there will be more focus in this area."
Gartner customers can log in to access the full Emerging Tech Impact Radar: Cloud Native report here
Published 11 November 2022 - ID G00771897 - 72 min read
By Analyst(s): Wataru Katsurashima, Colin Fletcher, Fernando Pereiro, Mark Wah, Michael Warrilow, John Santoro, Varsha Mehta, Balaji Abbabatulla, Chandra Mukhyala, Craig Lowery, Ed Anderson
Or access the full Emerging Tech Impact Radar: Security report here
Published 16 November 2022 - ID G00766277 - 101 min read
By Analyst(s): Elizabeth Kim, Swati Rakheja, Bill Ray, Nat Smith, Mark Wah, Dave Messett, Ruggero Contu, Dan Ayoub, Mark Driver, Lawrence Pingree
2023 Predictions: SaaS Security Enters the Spotlight

SaaS Security Enters the Spotlight
By Yoni Shohet, CEO and co-founder of Valence Security
Over the past two years, attackers have changed both their targets and strategies as they search for the most lucrative backdoors into organizations and their critical assets. As companies migrate from network-based infrastructure to the cloud, these assets are now shared and stored outside the well-secured organizational perimeter in multiple SaaS applications that are much more haphazardly secured. This shift has benefitted business collaboration and productivity, but it has also presented a new set of security risks that grow with every new SaaS application, SaaS-to-SaaS integration, external data share, unmanaged identity and SaaS misconfiguration.
Recent SaaS breaches involving Okta, GitHub, Microsoft 365 and Google Workspace among others have grown ever more complex, involving SaaS supply chain attacks and the exploitation of SaaS misconfigurations, ungoverned data sharing privileges and over privileged identities - all leading to account takeovers and data loss that can span multiple companies, data repositories and SaaS services.
Security practitioners and vendors must now evolve along with the SaaS environment, hackers and threats, leaving behind legacy SaaS security solutions that provide only partial visibility that lacks business context for SaaS adoption and usage. They must embrace the SaaS sprawl while also keeping up with attackers as they become more sophisticated and more determined.
As the CEO and Co-founder of Valence Security, a cybersecurity company striving to help security and business leaders improve their SaaS security posture, I believe that 2023 will be the year that SaaS security truly enters the spotlight. These are our top predictions for the coming year:
Security teams will shift their focus from proprietary apps to third-party SaaS apps.
The frequency and complexity of SaaS attacks we've seen in the past two years have shown that hackers shifted their focus to third-party SaaS applications due to their sprawl, interconnectivity and flood of ungoverned data sharing and user permissions that comprise an expansive yet marginally secured attack surface. The 2022 Shadow SaaS-to-SaaS Integration Report by Valence Threat Labs for instance noted that the average organization has 917 SaaS-to-SaaS third-party integrations - 4-5 times the amount estimated by CISOs. SaaS will be increasingly seen as the weak link in the security posture of organizations as security teams and their SaaS security vendors have heavily invested in securing IaaS, production, proprietary applications and code at the expense of securing SaaS. They will increasingly realize that SaaS environments must be hardened as the scope and expense of breaches grow exponentially.
SaaS security will evolve beyond visibility to include automated remediation.
Traditional SaaS security solutions have focused primarily on providing visibility into security SaaS adoption and use, with some light capabilities around risk mitigation. This is in spite of the fact that overworked and under-resourced security teams need tools that not just uncover risks but help them actually remediate them. The need for security solutions that provide automated remediation will be seen as critical tools in the security team's arsenal in 2023 vs. nice-to-haves as they have been considered over the previous few years. Security teams no longer want to just know about their problems, they want to be able to measure continuous scalable risk reduction.
SaaS security will increasingly be seen as a collaborative effort.
The democratization of IT has proven beneficial for the booming SaaS market. As users adopt and use SaaS applications independently, security teams will try to keep up. Going beyond visibility and alerts, remediation of SaaS risks and misconfigurations will increasingly require more business context as security professionals strive to empower users to leverage the benefits of SaaS while ensuring its security. In order to do so, SaaS security will be seen in 2023 as a collaborative effort going beyond direct security responsibility and driving engagement with business users through collaborative, decentralized workflows that will provide security teams with business insights they need to balance security and business productivity.
Zero-trust will need to be rethought for the SaaS mesh.
Enforcing Zero-trust principles for SaaS is vastly different from enforcing it on-prem as application adoption, use and management is decentralized. It requires not just a "policy of no," typical of on-prem enforcement, but a deep understanding of each application and how multiple, integrated SaaS apps as well as the sprawl of ungoverned data sharing, user identities, etc. work together to both enhance business productivity as well as create a massive risk surface. In 2023, security teams will increasingly realize that the vast mesh of SaaS-to-SaaS integrations, non-human and human identities and their privileges, and external data sharing permissions, must be mapped, monitored and their risks remediated using zero-trust principles in ways that still allow the mesh of SaaS integrations to grow at the pace of business.
Read More on VMBlog.com
Announcing Valence’s Series A Round: Introducing Collaborative SaaS Security Risk Mitigation
.jpg)
On behalf of Valence Security, I am extremely proud to announce that within a year of our seed investment, we have raised our $25M Series A round led by Microsoft’s M12 venture fund with the participation of leading investors including Porsche Ventures, Akamai Technologies, Alumni Ventures and Michael Fey, CEO of Island and former president of Symantec, as well as our longtime supporters and seed investor, YL Ventures. This is a great opportunity to thank our amazing team across the US and Israel, customers, investors and advisors who believed in and supported our vision from day zero and helped us rapidly accelerate our business.
When Shlomi and I founded Valence last year, the rise in SaaS supply chain attacks that leverage third-party integrations, OAuth tokens, API keys and no/low-code workflows to gain unauthorized access to sensitive data led us to focus on what we called the “business application mesh” of SaaS supply chain integrations. While working with our design partners and early adopters, we found that security teams are outpaced by the growth of this mesh and lack business context into SaaS adoption, making proper security governance practically impossible. Understandably, business users want to drive innovation and utilize the best tools to do so, and the benefits of using SaaS applications grow as they are integrated with other best-of-breed applications. Security teams have understood the need to adapt to this shift and are no longer interested in just gaining visibility into more risk surfaces, but now require processes and tools that will allow them to scale remediation efforts and measure effective risk reduction over time. We’ve heard CISOs tell us over and over, “Once I gain visibility into a problem, I need to be able to solve it”.
This growing need was the impetus for Valence’s collaborative SaaS security remediation solution, helping security teams engage, educate and empower business users to contextualize and remediate SaaS security risks. At first, we focused on remediating supply chain third-party SaaS-to-SaaS risks. Over time, conversations with our customers led us to understand that the problem space is much wider than we initially thought. They shared additional challenges relating to SaaS use and adoption including external data sharing, unmanaged identities and misconfigurations, and requested our assistance, leading us to expand our initial offering into a robust security platform.
Existing solutions such as Cloud Access Security Brokers (CASB) and SaaS Security Posture Management (SSPM) were inadequate to the task of mitigating and remediating these risks, and security teams today must choose between two evils - stunted business growth or increasing security risks. With limited visibility into configurations, connections, access and data sharing, these legacy solutions made it nearly impossible for security teams to remediate misconfigurations and risk without impeding business productivity or the velocity of SaaS adoption. This is why we extended our collaborative SaaS security solution to help tackle data protection, identity security and misconfiguration remediation, making SaaS security a comprehensive process rather than a fragmented patchwork of solutions. Our platform goes beyond basic SSPM functionalities to include business context into SaaS security decision-making, assisting security teams with prioritizing SaaS security risks and enabling automated and decentralized remediation workflows across the distributed organization. We pride ourselves on empowering security teams to engage with and educate business teams on security risks, while securing wide-scale adoption and interconnectivity between apps - thus becoming enablers instead of obstructors of innovation.
Building on our platform’s proven ability to help security teams automate the remediation of SaaS risks and misconfigurations and collaborate with business users effectively, our new funding round will be instrumental in accelerating our operations, scaling our R&D efforts and increasing our headcount in the US and Israel. We are always looking for talented, out-of-the-box thinkers who will grow along with us.
Excited about the next stage of our journey!
Read the Press Release here
Valence Integrates With Azure AD to Reduce SaaS Supply Chain Risks By Enforcing Zero Trust Principles
.jpg)
Valence Security has integrated with Azure Active Directory to give customers increased visibility and control over their SaaS supply chain risks. By integrating with Azure AD through Microsoft Graph, Azure AD audit logs and other Microsoft APIs, Valence is able to correlate multiple data sources to provide one viewpoint into all the Enterprise Applications, Service Principals, OAuth tokens and APIs that have access to Microsoft’s SaaS services. The Valence platform analyzes the applications access level and scope of access, data exposure, activity history, and correlates it with multiple risk signals from Azure AD, Valence’s threat intelligence and customer’s internal tools. In addition, Valence can integrate with dozens of SaaS applications to correlate configuration, activities and risks across the entire SaaS mesh and allowing security teams to enforce Zero Trust security policies at scale with collaborative remediation workflows that engage with distributed business users.By leveraging the Valence integration with Azure AD, customers can:
• Identify third-party integrations to Azure AD, Office 365, other Microsoft SaaS services, and other third-party SaaS applications
• Gain insights into high privilege integrations, exposed data and resources, admin consented integrations with organization-wide access and other end user OAuth consents
• Analyze application usage history to detect dormant integrations which are no longer needed by the business and can be revoked
• Correlate input from Azure AD, Valence’s proprietary threat intelligence and customer’s internal vendor risk management GRC tools
• Execute remediation workflows that scale engagement with business users tocontextualize third-party integrations and help security teams to enforce ZeroTrust
.jpg)
IBM Cost of a Data Breach Report Confirms the Need to Immediately Remediate Supply Chain Risks

Recently, supply chain attacks leveraging the interconnectivity of SaaS applications have become increasingly lucrative for cyber criminals. As the 2022 IBM Cost of a Data Breach report points out, one in five data breaches this year was caused by a supply chain compromise. Judging by the high-profile attacks of early 2022, including the GitHub OAuth attack campaign and Okta (LAPSUS$) breach, this trend is likely to accelerate, making these compromises more frequent and expensive.
According to the IBM report, the average cost of a supply chain breach was reported to be $4.46M, higher than the global average cost of data breaches. The continuing rapid adoption of SaaS applications by more and more business application owners, often without security review, will make this attack vector increasingly more pervasive and disastrous. Ownership over applications, integrations, identities and privileges will become primarily distributed across business units, and therefore harder for security teams to monitor and manage..
The report also notes that the average time to remediate a supply chain compromise was 303 days this year – 26 days longer than an average data breach. This remarkable lag time has clear ramifications for the overall rise in the cost of goods and services, resulting in an overwhelming ripple effect.
The growing number of external points of access into organizations and the alarming lack of adequate security controls to govern third-party access are clear contributing factors to the stark rise of this attack vector and the difficulty in achieving adequate remediation. A lack of visibility into shadow SaaS applications and the interconnected mesh of third-party integrations makes it difficult to catch breaches as they occur, stop attacks in real-time, or undertake post-event remediation. In Valence Security’s recent 2022 Shadow SaaS-to-SaaS Integration Report, our research shows that the average organization has 917 SaaS-to-SaaS third-party integrations – 4-5 times the amount estimated by CISOs who responded to our survey. As a senior enterprise CISO notes in Valence’s report, “[With] our workforce changes (on and off boardings), contractors, and cloud environment changes it is difficult to keep up with SaaS connections.”
Placing trust in a vendor’s own security controls is clearly not a sound security solution for enterprises, as third-party risk management processes lack context, continuity and visibility into the scope of a third-party integrations access to their organization’s core SaaS applications such as Microsoft 365, Google Workspace, Slack and Salesforce. These integrations are drivers of business productivity, efficiency and velocity, but with 19% of data breaches stemming from supply chain attacks, security teams must balance these benefits with appropriate security mechanisms to govern them.
Valence helps organizations dramatically reduce time to remediation by mapping, monitoring and mitigating these growing threats with a comprehensive security solution leveraging automated risk contextualization and remediation, without adversely influencing business processes. Remediation workflows can be scaled through engaging business users, educating them about their SaaS security risks, thereby empowering your security team as business enablement champions rather than impediments to adopting SaaS applications at scale.
Constant enforcement of security policies across the organizational SaaS stack - ensures that any new risks, topology changes and anomalies are immediately addressed and remediated. Such full-scale risk reduction can significantly reduce the cost of supply chain breaches, mitigating them before they occur and eliminating the need for legacy point solutions throughout the remediation process.
Infographic: Major SaaS Security Breaches 2021-2022
.jpg)
Over the past two years, the SaaS mesh has exploded, with 1.5K applications and 900 integrations adopted by organizations on average–many of which are onboarded without security review. This has led to an increased frequency and magnitude of SaaS breaches and SaaS supply chain attacks. This infographic shows some of the most destructive recent exploits.
.jpg)
The Most Overlooked Element in Most Organizations' Cybersecurity Strategy
.jpg)
Securing the adoption and use of non-human identities is probably the most overlooked element in most organizations' cybersecurity strategy today. Most organization’s SaaS security strategy focuses almost exclusively on human-to-SaaS interactions, and their security stacks, dominated by Cloud Access Security Brokers (CASBs), SaaS Security Posture Management (SSPM) solutions, and Identity Providers (IdPs), reflect this. This focus is only natural, as human users are the most visible.
Unfortunately, shadow non-human identities and SaaS integrations typically remain hidden, unmanaged, and ripe for exploitation. Even Third Party Risk Management (TPRM) solutions adopted to determine the security posture of third-party SaaS vendors don’t have visibility into their integrations with core SaaS services, thereby missing critical usage context.
The mass adoption of SaaS services and third-party integrations such as OAuth apps, APIs and low/no-code workflows that has accelerated due to the shift to remote work, increased business need for distributed, global collaboration, and the rapid, unmanaged, employee adoption of SaaS, has exposed organizations to potentially devastating SaaS supply chain attacks.
Such breaches are potentially more extensive than a direct attack on a single SaaS application or user account, since attackers can compromise not only the targeted SaaS account and its stored data, but multiple accounts or data repositories integrated with that breached account.
The growing problem of over-privileged API Integrations, ungoverned hyper-automation workflows, the onboarding of unauthorized SaaS vendors, and unused SaaS integrations that haven’t been properly offboarded all contribute to the growing exposure of most organizations to such SaaS supply chain breaches.
The result? We have witnessed a literal supply chain attack avalanche starting with the SolarWinds breach in late 2020 and accelerating to include multiple SaaS supply chain breaches occurring in just the first few months of 2022–including the Okta (LAPSUS$) and multiple GitHub compromises.
Yet despite this avalanche, most IT security teams are either unaware of the potential risk, are yet to conclude that the risk is substantial enough to allocate scant cybersecurity resources to mitigating the risk, or are finding a lack of available third-party solutions focused specifically on securing non-human identities. The 2022 Shadow SaaS-to-SaaS Integration Report by Valence Threat Labs, in fact, surveyed numerous CISOs, who on average estimated that they have less than 200 such integrations between third-party SaaS applications and their core SaaS, such as Microsoft 365, Salesforce, and Google Workspace.
In reality, according to cross-tenant usage data drawn from the Valence SaaS Risk Remediation Platform, the report found that the average organization had over 900 third-party integrations (4-5x estimated by CISOs). Most were adopted without IT team oversight or security review. Further, nearly half (48%) were found to be abandoned or unused, typically due to a failed PoC, providing a broad SaaS integration attack surface exposed and unmonitored.
Request a Free Shadow SaaS Integration Risk Assessment and find out how many hidden and unmanaged third party integrations are lurking in your organization.
Verizon 2022 DBIR Report: Supply Chain Attacks at Record High
.jpg)
In what has become an annual rite of spring in the cybersecurity world, Verizon recently published its 15th annual Data Breach Investigations Report. One of the most authoritative and well-documented studies of breaches and security incidents affecting both public and private sectors, the DBIR establishes clear benchmarks and key data points that the information security community relies on for understanding the global threat landscape and planning defensive measures to improve security postures in the future. Some of the expected findings include:
- Stolen credentials remain the primary threat vector malicious actors use to access systems and carry out exploits such as data exfiltration and denial of service (DoS) attacks.
- The role of ransomware in breaches continues its upward trend, with an almost 13% increase—a rise as big as the last five years combined—coming into play with a total of 25% of breaches this year.
- When it comes to data breaches, external actors are consistently more common than internal, with 80% of breaches being caused by those external to the organization.
Where the DBIR gets interesting is in regard to the explosive growth in incidents related to partners and the supply chain: “2021 illustrated how one key supply chain breach can lead to wide ranging consequences. Supply chain was responsible for 62% of System Intrusion incidents this year.” Broadly speaking, these designations include the risks associated with ungoverned and unseen integrations between third-party SaaS applications and core SaaS applications such as Salesforce, Slack, Microsoft 365 and Google Workspace using API keys, end-user OAuth tokens, and no/low code workflows.

In the System Intrusion data set Verizon researchers compiled, the category of “Partner” moved from its previous position as somewhat of a novelty issue (showing up in less than 1% of the data in years past) to the main attack vector in 2021. The authors point to the SolarWinds attack of late 2020, and the cascade of data breach incidents in 2021 that flowed from that initial hack, as the ignition point for this change in the threat landscape. But they also assert that this trend is indicative of larger forces at work, and likely portends a needed shift in cybersecurity priorities going forward.
The multiple supply chain breaches occurring in just the first few months of 2022–including the GitHub and Okta (LAPSUS$) breaches–certainly reinforce this line of thinking.

To quote the report on the initial SolarWinds hack and its larger implications: “While this incident might seem like an anomalous one-off, it may actually be representative of larger trends that we’ve been seeing in the industry, in terms of the interconnected risks that exist between the vendors, partners and third parties we work with on a daily basis.” Indeed, for the first time, the vulnerabilities posed by complex partner relationships in the cloud, reliance on third-party vendors, and extended supply chains have come into sharp focus.
IT Democratization Increases SaaS Supply Chain Risks
The findings in the DBIR, along with recent attacks targeting third-party integrations with core SaaS, dovetail with and bolster our understanding of the state of the threat environment we’re currently facing. Consider that the democratization of IT and the widespread adoption of cloud apps began several years ago, accelerated through the COVID pandemic, and now has become a primary IT concern.
It was a process through which many organizations became hyperconnected, expanding to operate dozens of SaaS applications, with identities and privileges (human and machine) distributed throughout business units and departments across the organization. Significantly, the democratization of IT empowered business users across organizations to manage best-of-breed SaaS applications directly, without IT security review or governance. All this significantly increased enterprises' dependency on supply chain third-party vendors.
It’s a trend that has greatly reduced deployment time and enhanced business agility, productivity and collaboration within countless organizations. SaaS applications are increasingly interconnected to maximize their benefits by automating business processes and data exchange.
Yet as business users indiscriminately connect their SaaS applications, so grows the risk of unvetted supply chain access to business-critical applications. As these SaaS-to-SaaS third-party integrations increasingly grow, it becomes a challenge for security and compliance teams to ensure proper coverage of their third-party risk management (TPRM) programs since they lack context and visibility into which vendors have access to their applications and the scope/exposure of such access. The lack of continuous governance over SaaS-to-SaaS integrations results in a sprawl of unnecessary third-party access. Without security oversight, business owners can generate over-privileged API tokens that significantly increase the blast radius of any supply chain vendor breach.
Looking Ahead
No doubt, the 2022 Verizon DBIR sets out some alarming new trends confronting the IT security community. Heightened awareness of the fact that as organizations grow and scale, so does the number of SaaS-to-SaaS integrations and the range of their new and ungoverned risk surface, will provide the appropriate foundation for new and effective solutions to emerge. Looking forward, it’s clear that fully securing your sanctioned and unsanctioned business-critical SaaS apps from partners and SaaS supply chain attacks requires both third-party integration attack surface and blast radius minimization.
Cyber Week 2022 Presentation by Yoni Shohet (5 Minutes)


Yoni Shohet, CEO and Co-founder of Valence Security, spoke at the Innovation spotlight at Cyber Week 2022 that was held at Tel Aviv University and is one of the largest, international cybersecurity conferences in Israel.
Yoni explained the challenges of securing the fast growing mesh of SaaS-to-SaaS third-party integrations and how Valence solves these challenges. In addition, Yoni addressed questions from the Innovation Spotlight panelists, including:
• How Valence is different from a traditional Cloud Access Security Broker (CASB)?
• How long does it take to get visibility over shadow SaaS integrations and gain insights into necessary remediation steps using the Valence platform?
• How does the Valence Platform discover shadow SaaS and shadow integrations that IT teams otherwise has no visibility into?
• How does Valence enable organizations to build the business application owners into the workflows for vetting, adopting, and offboarding SaaS-to-SaaS third-party integrations?
Democratizing SaaS Security Remediation
.png)
To fully embrace digital transformation at scale, enterprises are democratizing IT to empower business users across organizations to select, deploy and manage best of breed SaaS applications and their third-party integrations directly. As we all know, this paradigm shift unlocks innovation opportunities by enabling business users to independently adopt new solutions and integrations quickly, addressing their business technology needs at maximum velocity.
The flip side of this, is that when many of the decisions are made outside of the central IT department, in most cases they also lack the required security and governance. Therefore, security teams are left without critical business context to contextualize and assess the risks associated with their SaaS mesh. How can a security engineer or SOC analyst understand why a marketing team needs a new Salesforce extension, or why the engineering team added a new GitHub App? Employees and business stakeholders must be involved in the process in order to gain comprehensive understanding of the business context. Security controls and procedures must adapt to this new modus operandi and democratize their SaaS risk mitigation processes.
The reality is that security teams have largely struggled with communicating security requirements to the entire organization. Often, they are perceived to operate like a secretive “Big Brother” that demands that all IT decisions be channeled through them, with little transparency into why the security vetting and deployment of new SaaS applications and third-party integrations takes so long or why it is critically important. And, on top of this, it often appears to the end user that security teams view business needs as a low priority, and rank security concerns as more important. This provided only a minor inconvenience in the days of a limited number of organization-wide on-prem applications, where IT was required for configurations. But with IT decentralization, this is no longer the case when business users adopt hundreds and even thousands of SaaS applications and third-party integrations.
The end user’s perspective is that the security team performs time-consuming reviews of their chosen SaaS apps, with little or no regard for their immediate business needs. The end user is satisfied by their SaaS vendor’s inherent security mechanisms, which do not necessitate additional IT reviews, making it seemingly simple and safe to deploy it. What the vendor fails to tell them - and security teams may fail to communicate - is that the shared responsibility model stipulates that the vendor is responsible only for the security of their infrastructure, not for its usage. That responsibility lies with the end user, and ultimately their organization. The sad truth is that end users, naive as they are when it comes to security, almost universally over-privilege third-party integrations, thereby unnecessarily increasing the potential blast radius of any supply chain breach, regardless of the inherent security of the connected SaaS applications.
To make matters worse, end users will often deploy multiple third-party applications and/or integrations during a PoC evaluation, and fail to offboard those that were not selected at the end of the evaluation. This, in addition to failed offboard of terminated or inactive third-party vendors, can leave organizations with hundreds of abandoned integrations that sit unused and exposed, increasing the organization’s SaaS attack surface.
Democratizing SaaS security remediation workflows is increasingly necessary for modern business needs, and security teams must find ways to adapt - not obstruct - such progress. This must be the product of communication between users and security teams which requires trust. Security leaders must strive for their users to trust their judgment and intent, so that they feel their business needs are being considered and will not need to bypass security reviews. Security teams must also enable the end user to remain empowered to adopt and review SaaS apps and integrations, while voluntarily allowing security policies into the process. Finally, security teams can benefit from educating the end users in a collaborative way, in order for them to fully understand and appreciate the importance of security in their daily tasks.
Valence was built from the ground-up with these three pillars in mind. Instead of evaluating new SaaS integrations and offboarding existing ones from a purely security standpoint without end-user input on business need, security teams can use Valence to automate the process of eliciting application business owner feedback and empower them to either approve business critical applications or offboard unused or non-critical ones themselves. Over time, this trains end users to proactively consider the security implications when evaluating and adopting SaaS applications.
The democratization of SaaS security remediation workflows is an important complement of IT democratization. It means engaging with end users and SaaS application business owners to include them in the mitigation process so that they are actively engaged with the security team as they remediate SaaS security risks, and are consulted by the security team when offboarding high risk, over privileged, or unused integrations.
Over time, this also educates the entire business organization on the principles of SaaS security hygiene, clearly establishing that they can be implemented without disrupting business productivity. Ultimately this enables users, not security teams,to become the first line of defense against SaaS supply chain attacks and other abuses of high-risk third-party integrations.
Quantifying the SaaS Supply Chain and Its Risks


While software-as-a-service helps organizations improve productivity and agility, it also adds complexity to the enterprise environment as IT security teams need to have visibility over the data stored in each of the applications.
And when organizations integrate SaaS applications with other SaaS applications, the attack surface grows even more because more applications have access to the corporate data. For example, connecting Asana to Google Workspace gives the task management platform access to data stored in the productivity suite.
In a recent report from Valence Threat Labs, 56% of CISOs said they don't have a process in place, or are not satisfied with the process they have, for discovering and managing SaaS-to-SaaS connections and integrations.
Understanding SaaS Mesh
SaaS mesh refers to connecting a SaaS application with another SaaS, using methods such as OAuth and API tokens, low-code/no-code workflow, and SaaS marketplaces. Examples include using third-party platforms such as Heroku to access GitHub repositories via OAuth user tokens, or creating and sending email campaigns from the organization's website using the API instead of logging into Mailchimp's platform. It is possible to complete a task in Asana and have a corresponding notification message be printed in Slack.
Connecting SaaS tools to core business applications such as Office 365, Salesforce, and Google Workspace within a SaaS mesh helps enhance the organization's agility, productivity, and collaboration. However, if the mesh isn't managed correctly, it can expose data stored in business-critical applications, according to Valence Threat Labs.
The average organization uses around 80 SaaS applications — BetterCloud estimates that organizations with more than 1,000 employees use more than 150 applications, while organizations with 50 employees or less use only 16 SaaS applications. When asked how many SaaS-to-SaaS connections and third-party integrations are connected to core SaaS applications (such as Office 365, Salesforce, and Google Workspace), 50% of CISOs said they have 200 or fewer integrations, or that they didn't know, Valence Threat Labs found.

In actuality, the average organization has 917 SaaS-to-SaaS third-party integrations, according to Valence Threat Labs.
While 76% of CISOs think under 20 new integrations are added every month to their environment, in reality, 76 new third-party integrations are onboarded every 30 days.
Over-Provisioned Connections
When asked if they had a process in place to determine if an integration is overprivileged, 53% of CISOs in the Valence Threat Labs report said they didn’t. This is a problem because nearly half, or 48%, of SaaS integrations (443 integrations, to be specific) are unused, and many of them have more privileges than they need. A SaaS-to-SaaS integration is usually inactive because someone forgot to turn it off after testing out the integration and then deciding not to use it. But because the integration is still there, someone else who gains access to one application now has access to the other and can move laterally.
"Most organizations do not have a continuous process in place that allows them to assess the business justification of non-human identities and properly offboard unnecessary third-party vendors," Valence Threat Labs said in its report.
Low-code/no-code platforms such as Workato, Zapier, and Microsoft Power Platform are powerful because non-developers can pull together workflows to access data from multiple sources. However, if they aren't configured correctly, they can expose data erroneously. Because these platforms often are not managed by application security or IT security teams, CISOs may not even know these tools exist or are accessing business applications. In the Valence Threat Labs report, 35% of CISOs said they do not have low-code/no-code platforms in their environment, when it turns out over 96% of companies have at least one such platform in use. In fact, the average organization has four or five, according to the report.
In the report, 85% of CISOs said they did not have appropriate visibility and protection from the risks of SaaS-to-SaaS connections and third-party integrations. "The fact that 85% of CISOs were unhappy with the current solutions suggests the need for more solutions specifically designed to protect the SaaS mesh," Valence Threat Labs said in its report.
Read the Dark Reading Article here.
Valence Wins 3 Global InfoSec Awards from CyberDefense Magazine

SAN FRANCISCO, June 06, 2022 (GLOBE NEWSWIRE) -- Valence Security, a cybersecurity startup delivering the first security platform to bring zero trust principles to the SaaS Mesh, has been named a winner in three categories of the Global InfoSec Awards, presented by Cyber Defense Magazine. Valence is the recipient of the following awards: Hot Company SaaS/Cloud Security; Most Innovative Low-code/no-code Security and Publisher's Choice InfoSec Startup of the Year.
“We founded Valence to help enterprises protect their business-critical SaaS applications from supply chain risks. SaaS-to-SaaS interconnectivity, third-party integrations and no/low-code automation are prime targets for attackers since they are often underlooked, over privileged and ungoverned,” said Yoni Shohet, CEO and co-founder of Valence. “We’ve witnessed significant market adoption of our platform over the past 12 months and we’re honored by the industry's recognition of the importance of securing the SaaS mesh by being among such an impressive list of recipients of the most respected cybersecurity awards in the industry.”
“We scoured the globe looking for cybersecurity innovators that could make a huge difference and potentially help turn the tide against the exponential growth in cyber crime. Valence Security is worthy of these coveted awards and consideration for deployment in your environment,” said Yan Ross, editor of Cyber Defense Magazine.
Judges for the Global InfoSec Awards are CISSP, FMDHS, CEH, certified security professionals. Three major features judges look for in the nominees are: understanding tomorrow’s threats, today, providing a cost-effective solution and innovating in unexpected ways that can help mitigate cyber risk and get one step ahead of the next breach. CDM is always asking “What’s Next?” so we are looking for Next Generation InfoSec Solutions.
You can find the full list of winners located here: http://www.cyberdefenseawards.com/
Please join us virtually at the #RSAC 2022, https://www.rsaconference.com/usa today, as we share our red carpet experience and proudly display our trophy online at our website, our blog and our social media channels.
About Valence Security
Valence Security is a pioneer in enabling organizations to automatically protect their business-critical SaaS applications like Microsoft 365, Google Workspace, Slack and Salesforce from supply chain attacks by enforcing zero trust controls to their SaaS mesh - the network of SaaS-to-SaaS interconnectivity, third-party integrations and no/low-code automation.
The Valence platform simplifies the process of continuous compliance by automating shadow integration discovery and risk assessment, continuous monitoring of integrations and privilege drift and enforcement of least privilege access. The platform continuously engages with end users and business owners to encourage self-governance through regularly revoking unnecessary API integrations, unvetted apps, ungoverned no/low code workflows, and shadow OAuth third-party app tokens.
Valence Security is backed by YL Ventures and a group of renowned security executives with backgrounds from Google, Zscaler, Zendesk, Akamai, Goldman Sachs, Bank of America and Unity. For more information, visit www.valencesecurity.com.
About Cyber Defense Magazine
Cyber Defense Magazine is the premier source of cyber security news and information for InfoSec professions in business and government. We are managed and published by and for ethical, honest, passionate information security professionals. Our mission is to share cutting-edge knowledge, real-world stories and awards on the best ideas, products and services in the information technology industry. We deliver electronic magazines every month online for free, and special editions exclusively for the RSA Conferences. CDM is a proud member of the Cyber Defense Media Group.
Learn more about us at https://www.cyberdefensemagazine.com and visit https://www.cyberdefensetv.com and https://www.cyberdefenseradio.com to see and hear some of the most informative interviews of many of these winning company executives. Join a webinar at https://www.cyberdefensewebinars.com and realize that infosec knowledge is power.
Media Contact:
Montner Tech PR
Deb Montner
dmontner@montner.com
CDM Media Inquiries:
Irene Noser, Marketing Executive
marketing@cyberdefensemagazine.com
1-833-844-9468
1-646-586-9545
www.cyberdefensemagazine.com
The SaaS-to-SaaS supply chain is a wild, wild mess

Cloud migration and IT democratization have created a continuously growing network of interconnected business applications, integrated to digitize and automate business workflows. Employees in the digital transformation age are now compelled to choose their best-of-breed applications, independently adopting and connecting SaaS applications, no/low code platforms like Workato and Zapier, and SaaS marketplace third-party apps in order to increase productivity, creating a convoluted web of ever-growing app-to-app integrations. This expanding new network is built in the cloud and is based on third-party vendor integrations, introducing the SaaS-to-SaaS supply chain as the future of enterprise interconnectivity.

Massive amounts of data are now flowing between these applications in the highly dynamic cloud environment, and the modern enterprise cannot revert to the days of data silos and isolated applications. However, with every new connection and automated workflow, a new and concerning risk surface grows with indiscriminate and shadow connectivity. A ubiquitous phenomenon of the interconnectivity era, CISOs should take heed and consider the challenges introduced by the size, expansion, security and governance ramifications of the SaaS-to-SaaS supply chain.
Zero trust for non-humans
For years, security teams have focused on securing human-to-app interactions, adopting security controls such as managed devices, endpoint security, CASB, ZTNA, MFA and IdPs. These solutions provided value for their original purpose, but the SaaS-to-SaaS supply chain today thrives on application integration, non-human identities and app-to-app connectivity – leaving out the human element in order to streamline and automate work processes.
The SaaS-to-SaaS supply chain continues to grow uninhibited, without alerting security teams on new risks and connections created by non-human identities that cannot be resolved using traditional security controls designed for human-to-app interactions. The continuous increase in non-human identities in app-to-app integrations and their robust access to sensitive data-intensive platforms heighten attackers’ motivation to exploit these new attack surfaces.
Security teams struggle with handling the scale and sophistication of impending attacks. Blind to these threats and with application adoption becoming as easy as signing a form, employees are no longer inclined to request CISO consent to adopt new apps, and CISOs are not able to govern third-party access due to the ease of bypassing existing controls. The number of supply chain attacks via third-party vendors has skyrocketed over the past few years, as malicious actors leverage non-human identities to gain unauthorized access to business applications.
Third-party API takeover attacks
Enterprise budgets and organizational resources are heavily routed to fortifying internal security postures, while critical assets are left exposed to external threats due to these unmanaged third-party integrations. The infamous Solarwinds attack brought organizational reliance on third-party integrations to the forefront, leading to an inevitable backlash against existing, woefully unsuitable solutions for third-party risk management. As part of the attack campaign, the abuse of application credentials, like in the case of Microsoft Azure, and the focus on API takeover attacks targeting third-party vendors like Mimecast, highlight how attackers leverage such integrations to gain unauthorized access to critical business applications.
Securing the hyper-automated enterprise
The SaaS-to-SaaS supply chain with its unique characteristics is prone not only to third-party breaches, but also to various other ways by which malicious actors may leverage it as an attack vector.
As organizations strive for automated business workflows, hyper-automation, no/low code and enterprise application integration (EAI) platforms are the methods of choice for connectivity. These platforms are now configured by citizen developers, without security governance and oversight, potentially leading to misconfigurations and sensitive data exposure. Attackers actively target such platforms as they hold the keys to the kingdom with their high privileges across the enterprises’ most critical business applications.
Malicious OAuth token access
Attackers have found that human error and employee trust are lucrative opportunities for exploits and trickery, and target employee independence with SaaS marketplaces for phishing campaigns. With the increasing adoption of multifactor authentication (MFA), traditional account takeover techniques have become less efficient as it’s no longer enough to have a username and password to gain access. Attackers leverage marketplaces and third-party apps to trick employees into installing malicious apps via sophisticated consent phishing campaigns that provide them with OAuth tokens with high privileges, bypassing many security controls, such as MFA.
It all comes down to managing trust
The SaaS-to-SaaS supply chain will continue to grow and provide enterprises with value at scale, simplifying and automating processes, enabling robust data collection, and maximizing the benefits of enterprise software. That said, security teams cannot continue to ignore the pitfalls and challenges of this wild, wild mess, as it creates organizational dependency on external vendors, leading users to trust third parties for integration and interconnectivity while potentially jeopardizing their most important assets.
The shift from human to non-human interactions necessitates a corresponding shift in the paradigm used to secure these integrations, without impeding workflows. These challenges cannot be mitigated and resolved in silos. Security teams must gain more visibility and control by bolstering their collaboration with business application teams, decentralized owners, citizen developers and end users to ensure the secure growth of the SaaS-to-SaaS supply chain and enhance innovation, increase productivity, and enable organizations to reap the benefits of their digital transformation journey.
Read the HelpNet Article here.
2022 Shadow SaaS-to-SaaS Integration Report
.jpg)
Overview
This report covers key trends and challenges organizations face when trying to gain visibility and control over the growing and fast-changing world of SaaS-to-SaaS third-party integrations – known as the SaaS mesh. This mesh grows via API tokens, OAuth third-party apps, SaaS marketplaces, and no/low-code automated workflows that place sanctioned business-critical SaaS applications at risk of supply chain attacks. Statistics in this report include both results from a survey of top CISOs, collected anonymously by Valence Threat Labs researchers in conjunction with , and cross tenant metadata extracted from the that has been aggregated and anonymized to ensure customer privacy.
Executive Overview

SaaS Mesh Risks
The democratization of IT has empowered business users across organizations to manage best of breed SaaS applications directly, without IT security review or governance. This has greatly reduced deployment time and enhanced business agility, productivity, and collaboration. However, the indiscriminate connection of SaaS applications also increases the risk of unvetted supply chain access to business-critical applications like Salesforce, Microsoft 365 and Google Workspace. These high-risk connections are typically driven by end users that are encouraged to consent to OAuth apps by SaaS vendors without understanding the security implications of their actions and how to revoke the access they granted. In addition, business owners often generate over-privileged API tokens that significantly increase the blast radius of any supply chain vendor breach. Lastly, citizen developers automate workflows by creating complex data flows that are hidden from security teams who lack visibility into no/low-code platforms.
Survey Methodology
The survey queried decision-makers with job titles relevant to cybersecurity such as CISOs, CIOs, and Directors/VPs of IT security distributed across organizations ranging in size from under 1000 employees to more than 20,000 employees. Respondents were recruited via email invitations containing an embedded link to the online survey. The email invitations were sent to a select group of YL Venture’s qualified database. Valence Security was responsible for all survey design, data collection, and data analysis. These procedures were carried out in strict accordance with standard market research practices and existing US privacy laws.
Read the full report here.
Offboarding: Don't Forget Third-party Non-human Identities
.jpg)
Offboarding Employees is a Top CISO Priority
IT security departments have become pretty fastidious when it comes to offboarding ex-employees and contractors in order to ensure they don’t have the ability to access critical SaaS applications, corporate resources and sensitive data after they leave. In most cases, IT can complete the process of revoking a user’s privileges easily and quickly through the organization’s identity and access management (IAM) service, such as Okta or OneLogin. Of course, offboarding users from SaaS applications managed outside of the IAM service can be more challenging, though newer technologies are emerging to help manage these as well. At a minimum, however, offboarding of human users is now on the radar of, and a top priority for most CISOs to implement proper zero trust access controls.
….But Non-Human Identities and Third-Party Integrations Are Still Overlooked
This is not the case when it comes to non-human entities – SaaS-to-SaaS integrations that provide third-party vendors with access to corporate data, applications and privileges. These integrations are created using direct APIs, OAuth apps in SaaS marketplaces, and no/low code citizen development platforms such as Zapier, Workato, Mulesoft, and others.
The democratization of IT has empowered business users across organizations to reduce deployment time and enhanced business agility, productivity and collaboration by managing these SaaS-to-SaaS integrations directly. Unfortunately, they typically do so without IT security review or governance, thereby pushing them off the CISO’s radar.
This indiscriminate connection of SaaS applications significantly increases the risk of unvetted supply chain access to core business applications like Salesforce, Microsoft 365 and Google Workspace. This supply chain attack risk is a major, and growing, attack vector. For example, during the GitHub attack campaign in April 2022, attackers were able to steal and abuse OAuth tokens issued to well known vendors like Travis CI and Heroku. According to GitHub, the attackers were able to leverage the trust and high access granted to highly-reputed vendors to steal data from dozens of GitHub customers and private repositories.
On top of not having visibility into these employee/business unit adopted integrations, IT departments often lack awareness that non-human integrations impose a significant risk of expanding an organization’s privilege attack surface. In fact, even when it comes to IT-managed services, SaaS admins typically have a ‘set-and-forget’ mentality, not realizing that privileges can drift over time, and those elevated privileges can facilitate SaaS supply chain attacks and the lateral movement of threats. They also don’t consider that these integrations may at some point go unused, leaving unnecessary points of compromise. For privileges managed outside of IT, security teams are often unaware of their existence all together.
The Growing Challenge of Offboarding Non-Human Identities
The lack of awareness of the need to offboard non-human identities only exacerbates the risks inherent in unmanaged SaaS integrations. In many cases, it dwarfs the risks posed by improperly offboarded human users due to the lack of maturity of the non-human identity lifecycle compared to the broad adoption of human identities IAM controls like SSO, SAML and MFA. Disconcertingly, Valence Threat Labs analysis has found that over 50% of integrations between your third-party applications and business critical SaaS applications have not been used for at least 30 days for various reasons due to improper offboarding. This is because SaaS vendors and integrations are abandoned for multiple reasons, creating a wide range of challenges.
Offboarding Challenge #1: SaaS Evaluation/Assessment Hygiene
Let’s begin with proof of concepts (PoCs) for new third-party SaaS applications. An employee or team will often test several services, including integrating them into their overall SaaS mesh, before selecting the one that is best suited to the organizations’ needs. Most organizations today don’t have a process to ensure that such third-party vendors are properly offboarded after the trial and that all of their integrations to core SaaS applications are revoked. This can be exploited by hackers who can gain access to an account by stealing access tokens, or through other SaaS applications due to the lateral movement of threats or a supply chain attack.
Making matters worse, SaaS admins typically provision such integrations with excessive privileges due to the difficulty of manually configuring services with zero trust and least privilege best practices. This further facilitates the lateral movement of threats, placing organizational data at an even greater risk of cross-SaaS compromise once an attacker gains a foothold.
Offboarding Challenge #2: Natural Changes in Business Needs Over Time
The second offboarding challenge is the simple replacement of SaaS-to-SaaS integrations over time. Changing business needs often render certain SaaS applications and their integrations no longer necessary, while others become obsolete when innovative or improved technologies emerge. Revoking access for unnecessary, legacy or obsolete services and their integrations is often the last thing on a SaaS admin’s mind as they move to their next business project, and if it is a free or minimal cost application, there is little financial incentive to terminate it. Continuous SaaS hygiene in the wake of this natural drift is currently nearly impossible.
Offboarding Challenge #3: Application Owner or Organizational Change
Application ownership is currently a vague and cursory concept in most organizations. Without a comprehensive inventory of why specific applications exist within the organization and who is responsible for their access, privileges and activity, risk grows while security posture weakens. Connecting to third-party applications using OAuth tokens, for instance, can cause both SaaS management headaches and disrupt business continuity since they are often adopted by individual users for their own use without IT knowledge or an understanding of the company-wide business implications.
Suppose a marketing employee adopts Hubspot and then integrates it with Salesforce using their own Salesforce account rather than a dedicated organizational service account, which would be a standard procedure for IT teams when they are managing such integrations. The employee then sets up lead capture forms on the website, lead nurturing and distribution processes with the sales team, and so on. If the employee at some point leaves the organization and IT disables their account access during the offboarding process, the HubSpot integration will break, potentially disrupting the entire organization’s digital lead generation process.
The Need to Continuously Monitor Non-human Identities to Ensure Proper Offboarding
The key takeaway here is that overlooking the need to properly offboard non-human integrations harms the organizational security posture. IT departments must treat the offboarding of non-human identities with equal seriousness to offboarding their human users. Digital transformation, constant innovation and the adoption of SaaS applications provide significant business benefits, but organizations must take into consideration that the world of non-human identities within this digitized and automated environment is every bit as dynamic and a source of risk as that of human users. Security teams want to be business enablers, adapting to the modern API/integration economy where many innovative solutions “just need API access” to deliver their service.
This demands the ability to constantly monitor all changes to this dynamic environment in real time, identify and review new applications and integrations as soon as they enter the organization’s SaaS mesh, and offboard applications and integrations quickly when they sit unused. These are the fundamental actions necessary if security teams are serious about fully minimizing their attack surface, maintaining least privilege access, and ensuring that the principles of zero trust are applied across the board when it comes to access to their core SaaS applications and valuable corporate data.
Indeed, an effective, unified offboarding process must formally consider both human and non-human identities and their access privileges as a matter of course in order to minimize this burgeoning attack surface.
GitHub and Their Customers are the Latest Victims of Supply Chain Attacks
.png)
GitHub announced last Friday that an internal investigation had discovered a breach: attackers had stolen OAuth user tokens issued to third-party vendors, Heroku and Travis-CI. These tokens were then used to download private data repositories from dozens of GitHub customers, including GitHub itself and npm, who had been using Heroku and Travis-CI-maintained OAuth applications.
Github researchers suspect that secrets harvested from these data stores could potentially be used to launch much wider supply chain attacks to gain access to additional infrastructure.
A day after the initial breach discovery, GitHub revoked tokens associated with GitHub and npm’s use of these compromised OAuth applications. GitHub also recommended to Heroku and Travis-CI that they conduct their own security investigations, revoke OAuth user tokens for the affected applications, and notify their users. GitHub customers, in turn, will be notified within 72 hours by GitHub via email with next steps to guide their own response.
While GitHub’s discovery of the breach was relatively quick, we still do not know when the attack took place. Even if the exploit was discovered on the same day of the initial breach, it still left customers potentially vulnerable during the days-long gap between initial discovery, customer notification, and full remediation. This lag-time provides ample opportunity for an attack of this type to metastasize and cause additional damage, pointing to the need of a more proactive defense.
If you haven’t done so yet, we recommend verifying that the following OAuth application are blocked in your GitHub organization and revoking any unknown or unvetted third-party vendor access:
- Heroku Dashboard (ID: 145909)
- Heroku Dashboard (ID: 628778)
- Heroku Dashboard – Preview (ID: 313468)
- Heroku Dashboard – Classic (ID: 363831)
- Travis CI (ID: 9216)
You can follow this guideline to review your OAuth access restriction policy and this guideline to review the OAuth tokens you authorized. In addition, it’s recommended to review the audit log, the user account security log for suspicious activity, installed GitHub Apps, and authorized Personal Access Tokens.
Feel free to contact us at info@valencesecurity.com for further assistance.
After doing this, the first step to secure your SaaS mesh from future supply chain breaches is for security teams to ensure they have proper inventory and monitoring of all non-human third-party integrations into critical SaaS applications like GitHub.
Valence Security can help provide this inventory through a free risk assessment of GitHub or any of several other business-critical SaaS applications. This assessment, which takes minutes, will uncover shadow GitHub Apps, third-party OAuth applications–as well as other third-party integrations connected to that SaaS application, terminated and inactive third-party vendors with valid access tokens to those SaaS applications, and suspicious and risky third-party integrations with high privilege access.
Ongoing use of Valence can help you continuously monitor the topology, configurations, and activities across your SaaS-to-SaaS supply chain to detect new connections, anomalous activities, data leakage, and over-provisioned privileges. In addition, it can extend zero trust principles to your SaaS-to-SaaS supply chain, enabling you to enforce policy controls such as least privilege access, workflow compliance, and revocation of compromised tokens.
This GitHub incident is just the latest in a string of recent attacks leveraging supply chain access to gain unauthorized access to critical business applications and data, and it certainly won’t be the last. You can depend on Valence to help cover your critical SaaS applications.
Contextualizing Supply Chain Risks In A SaaS Environment

.png)
According to the report by YL Ventures, 70% of surveyed enterprise security leaders do not believe that TPRM solutions have helped them avoid risk. Much of their doubt is rooted in the lack of context in current TPRM processes. This is significant for a solution used by 83% of respondents. In the meantime, bad actors have intensified their attacks on – transforming them into one of the most popular attack vectors. Compliance and board-level pressures around third-parties are rapidly mounting, placing further pressure on CISOs already struggling with the process. In the race to address these growing supply chain risks, it is worth investigating how we can optimize existing practices to better manage the potential risk to enterprise networks. The reveals two critical blind spots that keep us from actualizing the true potential of TPRM: how we interact with third parties and how they interact with each other in our own environments.
The SaaS Boom
Third-party SaaS vendors have increasingly permeated every facet of our workflows and business processes. The adoption of SaaS applications and the race to optimize their use has led organizations to create more integrations between these applications to enable data flow and automated workflows. Visually, we can imagine information passing through an interconnected web of SaaS solutions continuously pinging one another for access and data. These communications lie at the heart of our newly uber-streamlined workflows and accelerated productivity. They are also inherently risky gateways into our environments since they increase dependency on and interconnectivity with third-party vendors.
Accounting for Dynamism
Lacking meaningful context, third-party risk management (TPRM) solutions are limited by critical blind spots that mute CISOs’ confidence in their actual risk-mitigation. Where today’s third-party integrations are continuous, widespread, and ever-evolving, current TPRM solutions tend to offer point-in-time assessments of the security posture of vendors, rather than assessing actual integrations with third-parties and vendor-customer relationships. The democratization of IT has empowered business users across organizations to manage best of breed SaaS applications directly, without IT security review or governance. This has greatly reduced deployment time and enhanced business agility, productivity, and collaboration. However, as business users quickly and indiscriminately connect their SaaS applications, the risk of unvetted supply chain access to business-critical applications like Salesforce, Microsoft 365 and Google Workspace increases dramatically. It then becomes a challenge for security and compliance teams to ensure proper coverage of their TPRM programs since they lack visibility into which vendors have access to their applications and the scope/context of such access in this ever-changing environment.
Current Best Practice Limitations
Best-practices, such as and proper data access protection, face limitations due to blind spots. They are impossible to implement without accounting for larger contexts and the often dynamic nature of third-party relationships and information. Even one misattribution can undermine zero trust, leading to over-privileged third-party access or to dormant vendors with unnecessary access. In addition, many enterprises suffer from “set-and-forget” third-party integrations that can either evade or bloat the supply-chain risk management process. All of this means that an entire network of third parties is working with and exchanging enterprise data without adequate supervision and governance.
Unlocking TPRM Potential
According to the CISO Circuit report by YL Ventures, CISOs are often more motivated by compliance than real security strategy when employing TPRM solutions. These findings underscore their lacking faith in TPRM efficacy. It is possible to improve supply chain security and generate better best practices. However, solutions must demonstrate a better appreciation for actual implementation of third-party vendors and how that impacts the communication of our digital assets. Correspondingly, we must have a better understanding of integrations across every—or at least multiple—points of their lifetimes, to implement proper zero trust.
As we grow more dependent on third-party SaaS applications, we must extend third-party vendor risk assessments from their security controls to how we use and interact with the third-party itself. This does not negate the current utility of TPRM solutions; they are still among the most comprehensive approaches available to managing supply chain security. Nonetheless, without change, the persistence of these limitations all but guarantee that our supply chain protection remains incomplete. To this end, acknowledging that it is ongoing and in need of more continuous attention is an important start. Extending the scope of third-party security risk factoring can, in turn, feedback into a more effective TPRM process. The more engaged we become in seeing, tracking and governing third-party integrations into enterprise networks, the more data we can offer to the risk scoring process. Though it may verge on the idealistic, this would likely improve the accuracy of TPRM results and consequential CISO confidence in TPRM reliability.
Download PDF
The Mailchimp Breach Is Just The Latest Supply Chain Attack

MailChimp, a leading email marketing firm, recently discovered that hackers had gained access to internal customer support and account management tools, which could be used to launch phishing attacks to steal customer data. Buried by the headline, however, was this even bigger eye-opener:
“In addition to viewing accounts and exporting data, the threat actors gained access to API keys for an undisclosed number of customers, which have now been disabled and can no longer be used.”
In today’s API economy, API keys and OAuth tokens truly hold the keys to the kingdom, enabling bad actors to not only launch phishing attacks but conduct potentially broader and more destructive supply chain attacks that can lead to massive data theft. In fact, the vast majority of recent high profile attacks like the Mimecast breach that resulted from the SolarWinds breach, and the recent LAPSUS$ attack against Okta, have a significant supply chain attack component. In each case, hackers targeted supply chain access and third-party vendors since they are trusted with high privilege access, yet often don't apply sufficient security controls.
The reality is few SaaS customers actually do a full audit of their third-party vendors, applications, and their integrations, leaving applications with inherent vulnerabilities, misconfigurations, and over-privileged integrations unseen and unmanaged. Worse yet, over time privileges drift, integrations go unused, and configurations can change, necessitating continuous monitoring – something overburdened IT security departments can’t effectively do manually.
Valence is the first SaaS security company to address the security challenges posed to an organization’s SaaS-to-SaaS supply chains by unmanaged third-party integrations, including direct APIs, OAuth apps in SaaS marketplaces, and no/low code citizen development platforms such as Zapier, Workato, and Mulesoft.
The SaaS-to-SaaS Supply Chain Threat Landscape


The SaaS-to-SaaS Supply Chain
As the number of SaaS applications used by organizations rises, so do the benefits inherent in the ever-growing SaaS sprawl. Connectivity and transparency are fundamental in today’s business environment and are the vehicles for improved information sharing, scalable workflows, agility, and efficiency. In the SaaS age, these benefits are multiplied as organizations are able to choose their best-ofbreed SaaS applications and use hyperautomation no/low code platforms (like Workato, Zapier, etc.) to integrate them with other applications, creating the convoluted and ever-growing SaaSto-SaaS supply chain. Pandium’s 2020 report on “The State of Product Integrations at the SaaS 1000” indicates that the 15 largest SaaS companies (including Zoom, Shopify, Salesforce, Slack and Okta) each have an average of 347 integrations and extensions available.

The ability to seamlessly integrate business applications using organization-wide API integrations, no/low-code platforms and SaaS marketplaces is crucial for enterprises. Zoom has recently announced that it has created a dedicated fund of $100M to expand its communication ecosystem and extend Zoom’s platform play by encouraging third-party developers to build applications and integration extensions. SaaS platforms have intrinsic motivation to encourage users to subscribe to as many applications as possible. This creates vendor lock-in effects, as enterprises find themselves entrenched deeper into the platform feature set, and make switching to a different vendor cost-prohibitive. This causes those platforms to tend to implement more and more features that encourage integrations and make them simpler to create (for example, Slack actively promotes relevant applications for subscription when you paste a URL, and it usually takes only two additional clicks to complete the subscription). Facilitating communication and providing seamless collaboration opportunities in an automated fashion is becoming the standard for the modern workplace, as Gartner estimates that over 70% of large commercial organizations have dozens of hyperautomation initiatives underway.

The limitations inherent in on-prem and network-based integrations and workflows allowed security teams to tightly control and govern the organization’s applications integration portfolio but hindered users’ ability to discover tools and platforms that benefit productivity, drive innovation and save time and resources for the organization. As digitalization transforms business processes through the cloud, end-users now have the ability to onboard new third-party services independently, without organizational governance or security oversight, using “set and forget” integrations and lacking continuous validation or integration into TPRM processes. However, revoking these integrations is usually a complex feature, hidden behind multiple screens in the settings screen. What this translates to is users almost never revoking access, so even a single-day experiment with a vendor turns into continuous and persistent access.

This drive to connect and the ensuing benefits for both users and enterprises cannot overshadow the risks inherent in automated processes involving third parties and indiscriminate shadow connectivity, which security teams may be completely blind to. At Valence, we strive to raise the awareness of both security teams and executives to this new and constantly expanding supply chain risk surface, and provide remediation tools to map, manage and mitigate the SaaS-to-SaaS supply chain. The following report offers a comprehensive review of what security teams should know about the SaaS-to-SaaS supply chin and its challenges.
SaaS-to-SaaS Supply Chain Security Risks
Essentially, it all comes down to managing trust. While every new integration takes business to a new, streamlined and efficient level, security teams should be wary of developing an organizational dependency on external entities and expect them to secure their internal assets. Digital interaction in the cloud era is predicated upon user identities, establishing privileges and controls for their access to data and assets. Traditional access control solutions such as managed devices, IdP, CASB, and ZTNA have been relatively successful in securing human-to-app integrations. Security teams focus on these integrations, controlling user accounts that expose data intentionally or not. Non-human or app-to-app integrations operate and act in the background, connecting through service accounts, constantly ‘logged in’ and available to malicious actors.

SaaS-to-SaaS Supply Chain Security Risks Essentially, it all comes down to managing trust. While every new integration takes business to a new, streamlined and efficient level, security teams should be wary of developing an organizational dependency on external entities and expect them to secure their internal assets. Digital interaction in the cloud era is predicated upon user identities, establishing privileges and controls for their access to data and assets. Traditional access control solutions such as managed devices, IdP, CASB, and ZTNA have been relatively successful in securing human-to-app integrations. Security teams focus on these integrations, controlling user accounts that expose data intentionally or not. Non-human or app-to-app integrations operate and act in the background, connecting through service accounts, constantly ‘logged in’ and available to malicious actors.
The free flow of data in the supply chain and its constant growth result in over-privileged API integrations, shadow OAuth tokens and ungoverned automated workflows, forming a new risk surface. Malicious actors abuse these integrations and take advantage of the SaaS-to-SaaS supply chain in order to leverage non-human identities and shadow connectivity. An example of such leverageable loopholes are applications developed by Google Workspace users. Using Google’s Apps Scripts platform, users can develop business applications that integrate with Google Workspace, using a highly optimized serverless script for automating Google services. These home-grown applications interact with Google Workspace users via Google OAuth 2.0 to receive consent, permanent access privileges into these users’ Google suite of services. These privileges can be garnered through consent phishing, and are also attractive for backdooring accounts as App Scripts lie beyond the purview and sight of standard security controls and ondevice monitoring, in a completely serverless environment. The SaaS-to-SaaS Supply Chain Threat Landscape 8Hyperautomation platforms like Microsoft Power Platform, Zapier and Workato have become increasingly popular, as they improve data sharing across various applications in the business environment, adding to the ease of data flows within the SaaS-to-SaaS supply chain. Additionally, hyperautomation breaks down data silos and communication barriers and contributes to scalability and profitability as it replaces manual workflows. However, the use of these platforms without appropriate security oversight may lead to shadow connectivity, over-provisioned privileges and possible misconfigurations as was the case with Microsoft Power Apps.
Misconfigurations regarding access to Microsoft’s low-code platform led to the exposure of 38 million records of sensitive data, such as COVID-19 contact tracing, employee IDs and email addresses, belonging to 47 government agencies and companies. The extended ownership citizen developers receive increases the likelihood of human error, making it easier for attackers to leverage them in order to steal the keys to the kingdom.

The Anatomy of SaaS-to SaaS Supply Chain Attacks
1 | Supply Chain API Takeovers
Arguably the most famous attack of recent years, the SolarWinds campaign also targeted the Microsoft 365 accounts of Mimecast customers. The attackers abused Mimecast’s high privileges to gain unauthorized access to Mimecast certificates and keys, and obtain sensitive data well beyond the Mimecast environment. A similar breach occurred when attackers leveraged a vulnerability found in Waydev, an analytics platform and third-party tool used by software companies, to steal GitHub and GitLab OAuth tokens after gaining access to the platform’s databases.
2 | Malicious 3rd Party Apps and Consent Phishing
With heightened adoption of MFA, classic phishing attacks have grown ineffective - a username and password will not grant attackers access any longer. Therefore, attackers attempt to trick users into consenting to malicious 3rd party apps and OAuth tokens. According to a warning by Microsoft from 2020, they leverage the ease of authorizing new plugins and extensions with limited visibility for security teams. This technique was used to gain unauthorized access to the SANS Institute emails and to steal users’ contacts and mail by APT groups.
3 | Non-human Identity Based Attacks
Attackers leverage the increased usage of non-human identities and app-to-app connectivity to execute exfiltration, lateral movement and privilege escalation techniques. In the SolarWinds breach, attackers manipulated Microsoft OAuth app certificates to abuse appto-app trust and gain unauthorized access to sensitive data. In another case, Microsoft published that attackers used Microsoft’s low-code platform, Power Platform, to maintain persistence and exfiltrate sensitive data.
Introducing Valence
Valence is the first security platform that helps organizations manage the risks associated with SaaS interconnectivity. The platform connects to core business applications, analyzing configurations and activity logs. Within minutes, Valence provides organizations with visibility, continuous monitoring, and automatic policy enforcement and remediation. First, the platform generates an inventory of all SaaS-to-SaaS connectivity, mapping third-party integrations, OAuth tokens, and automated workflows. The platform then continuously monitors topology changes and activities to detect anomalies, compromised tokens, and track how PII and sensitive data flows between applications. Finally, the platform allows security teams to mitigate risks by providing a self-serve platform that applies zero trust principles, enforces least privilege access, and ensures compliance of all automated workflows. Valence helps you gain contextual visibility and reduce risks associated with your third-party integrations and app-to-app connectivity.
Download the Whitepaper PDF
VentureBeat–With threats like Lapsus, security playbooks ‘go out the window’

The world of cybersecurity is infamous for changing fast. But tactics such as those exhibited by the hacker group Lapsus$ in a series of breaches over the past month suggest there’s even less that security teams can feel certain about, experts said.
As just one example: After stealing and threatening to leak data from Nvidia in February, Lapsus$ at one point made the demand that the graphics chipmaker “completely open source” its GPU drivers for Windows, macOS and Linux. And, Lapsus$ said on Telegram, Nvidia needed to do so “from now on and forever.”
The group’s “oddball behavior” tends to “complicate companies’ responses,” said Emsisoft threat analyst Brett Callow.
Companies “will have planned what to do in the event of being hit with a $1 million cash demand,” Callow said. “However, their playbooks will almost certainly not cover a crazy scenario in which they’re asked to make their drivers open source.”
Lapsus$ has been responsible for a string of confirmed breaches over the past month, including against Nvidia, Samsung, Microsoft and a third-party Okta support provider.
Bloomberg reported Wednesday that Lapsus$ is headed by a 16-year-old who lives with his mother in England. And today, the BBC reported that the City of London Police have arrested seven teenagers in connection with the Lapsus$ group. It was unknown whether the group’s leader was among those arrested.
But while the continuance of Lapsus$ itself may be uncertain, any other threat actors that seek to emulate their approach will serve as a different type of threat that must be adjusted for.
“Old-school ransomware gangs are predictable, and companies can pre-plan their responses,” Callow said. “With Lapsus$ et al, playbooks go out the window.”
Bribing Insiders
In its post about Lapsus$ earlier this week, Microsoft pointed to a number of unconventional tactics used by the group, particularly when it comes to gaining initial access. For one thing, the group is fond of bribing insiders, Microsoft researchers said.
To gain initial access, Lapsus$ has been observed “paying employees, suppliers, or business partners of target organizations for access to credentials and multifactor authentication (MFA) approval,” according to Microsoft researchers.
On his KrebsOnSecurity site, Brian Krebs also shared details on the bribery tactics used by Lapsus$. According to Krebs’ sources, the group has been working to recruit insiders through social media for several months. Messages posted by the group on Reddit offered employees at major telecoms as much as $20,000 per week for doing “inside jobs,” Krebs disclosed.
Given that Lapsus$ has been paying to gain access into companies’ environments, this means “they don’t use vulnerabilities, and don’t deploy malware to breach the organization and cause damage,” said Shahar Vaknin, who heads the threat hunting team at cybersecurity firm Hunters.
This makes many of the security tools used by companies “irrelevant,” since “there are no IOCs [indicators of compromise], no malware,” Vaknin said.
“We need to make a stronger case for the concept of zero trust — to actually assume malicious, compromised insiders — and be able to spot them,” he said.
However, this is very difficult to accomplish in practice, given that this approach tends to create a lot of false positive signals, Vaknin said.
Third-party risk
Of course, the group’s use of a third-party as a way to access larger vendors, as in the Okta incident, is nothing new, noted Yoni Shohet, cofounder and CEO of cyber firm Valence Security.
“As organizations go through digital transformation and democratization of IT, they become highly dependent on third-party integrations. We can only assume that the attackers will increasingly focus on supply chain access and third-party vendors,” Shohet said.
Lapsus$ has just borrowed that approach and put its own, unusual spin on things, experts said.
In the Okta incident, Lapsus$ did not make any demands at all — at least not on its Telegram channel — prior to posting screenshots as evidence of the breach this week.
The closest thing to a clue on motive is the group’s statement, in the Telegram post about Okta, that “for a service that powers authentication systems to many of the largest corporations (and FEDRAMP approved) I think these security measures are pretty poor.”
Lapsus$ followed up with another post on Tuesday, criticizing Okta for a number of its security measures.
But the apparent motive and target has varied by attack, as noted by Microsoft. Researchers at Microsoft — which confirmed that Lapsus$ stole some of its source code — believe that Lapsus$ is “motivated by theft and destruction.” The group has in some cases extorted victims to prevent the release of data, but in others has leaked data without making any demands, the researchers said.
In its communications about the Nvidia breach, Lapsus$ demanded that Nvidia remove an anti-cryptomining GPU feature, suggesting to some that financial motives are a factor to some degree. But the overall picture remains opaque when it comes to Lapsus$.
With a mix of financial targeting and hacking of IP, there has been “no one clear direction or motive for the group,” said Oliver Pinson-Roxburgh, CEO at cybersecurity services firm Bulletproof.
And while the future of Lapsus$ itself may be in doubt, the group did manage to become a “force to be reckoned with” in a short period of time through unconventional means, he said. Whether it’s Lapsus$ itself, or any others that emulate the group, “businesses should be prepared and learn their tactics, techniques and procedures, and monitor for attack.”
Read the Venturebeat article here.
Three Security Take-aways From The LAPSUS$ Breach of Okta

Okta has denied that the hacker group LAPSUS$ breached their service and performed malicious exploits, while LAPSUS$ claims it has gathered significant Okta customer data over the past several months—enough for additional exploits. No matter which claim is found to be accurate, it should still be sounding alarms that looming supply chain attacks are always brewing that could hit an organization’s interlinked business-critical SaaS applications across customers and the high-value data stored in these services. Such attacks rely heavily on risky, over-privileged integrations between services to maneuver across accounts and services, wrecking havoc along the way.
Whether this specific incident leads to supply-chain attacks remains to be seen, but as we increasingly trust third-party vendors to perform business critical functions, including ones like Okta that many organizations highly trust, so does the potential risk of attackers like LAPSUS$ targeting them as the “weakest link” to gain access to a broader mesh of integrated SaaS services increase. This goes double for unvetted and unsanctioned SaaS apps adopted by business units due to the democratization of IT, typically onboarded without security team review or oversight. These third-party apps may have significant vulnerabilities and misconfigurations, or be integrated with business-critical apps (like Microsoft 365, Salesforce, and Google Workspace) through over-privileged integrations that can provide the keys to the kingdom.
It has almost become axiomatic that, in the cloud, “Identity is the new perimeter” to be defended with robust Zero Trust controls. But SaaS security solutions to date have mostly focused on human identities, not non-human identities like direct APIs, SaaS marketplaces, and no/low code platforms (such as Zapier, Workato, Mulesoft, and others), that make the integrated mesh of business applications possible. This oversight significantly expands the potential blast radius of any exploit through the lateral movement of threats once the “weakest link” has been breached.
To address this oversight, IT security teams need to ensure robust Zero Trust security controls on the access they, or other business units, provide third-party vendors into corporate environments. What does this mean?
- Maintain Compliance Visibility & Auditing for Third-Party Apps and Integrations
Regularly audit your SaaS services to uncover shadow integrations, high-risk apps, and over-privileged integrations. This provides compliance visibility and auditing trails both if a breach occurs, and to maintain constant visibility even if one doesn’t. It also helps baseline your risk level as you move to reduce your third-party integration risks and monitor for changes over time, such as the unsanctioned adoption of new services and integrations or instances of privilege drift, which continually occur.
- Offboard Unnecessary & Risky Integrations
As a necessary second step, you should quickly offboard any unnecessary third-party vendors and integrations. This includes ones that have been abandoned after initial evaluation but never turned off, the departure of the app owner/admin, or just plain falling into disuse, as well as those apps and integrations that have been vetted and found to be high risk. This will reduce your potential non-human attack surface by reducing the number of unnecessary or high risk integrations into your sanctioned business-critical SaaS apps that can be exploited in the event of a supply chain attack.
- Maintain a State of Least Privilege Access for All Third-Party Integrations
The third step is to apply least privilege policies to ensure integrations have only the level of permissions necessary to function nominally. The truth is most business users tend to over-privilege their integrations, increasing the opportunity for bad actors to perform damaging cross-service exploits. This includes both continuous monitoring for application and privilege changes, but also auto mitigating the risks.
One often overlooked point is that such a security regime is most effective when you democratize SaaS integration risk mitigation, since they are the ones adopting these services in the first place. Alerting the application owners when a risky app or over-privileged integration is discovered, and guiding them to mitigate them themselves, will not only help build awareness around the need to prevent risky adoption of integrations going forward, but also avoid disruptions in business continuity that can be caused by over-vigilant security personnel cutting off an integration without the collaboration of the service owner.

Valence Security Completes SOC 2 Type II Certification

We at Valence Security are extremely pleased to announce that we have successfully completed System and Organization Controls (SOC) 2 Type II certification for our first-of-its-kind platform for securing the SaaS mesh.
The SOC 2 audit process included an extensive evaluation of our security processes and controls, the development best practices our engineers have implemented, and the ongoing activities we carry out to ensure our platform and customers' data is secure.
This tremendous step, taken so soon after our initial product launch in 2021, shows our dedication and commitment to not only securing our customers’ mesh of SaaS-to-SaaS third-party integrations, but also to maintaining effective controls over the security, availability, and confidentiality of our platform and our customers' data in accordance with attestation standards established by the American Institute of Certified Public Accountants (AICPA).
“SOC 2 Type II certification provides our customers with confidence that we maintain rigorous controls to secure our platform and their data,” said Shlomi Matichin, Co-founder and CTO of Valence. “As a company dedicated to securing SaaS-to-SaaS third-party integrations and helping customers build trust in their SaaS vendors, completing this key certification has been a top priority for us since the beginning of our journey and we are proud to have achieved this in record time.”
As part of our commitment to the highest security and governance standards, in addition to implementing the standard SOC 2 Type II requirements, we have implemented advanced security controls to ensure we earn our customer trust such as multi-tenancy, zero trust access to production, and continuous audit trail capabilities. As part of the process, we were able to quickly remediate and respond to every potential security risk that was detected. Security is part of our DNA and always a top priority.
Going forward, we will be enhancing compliance with additional security and privacy standards to provide our customers with confidence in our commitment to the security of our platform, their SaaS-to-SaaS third-party integrations, and their business critical data.
About Valence Security
Valence is the first security platform that enables organizations to enforce zero trust controls on the rapidly expanding mesh of shadow third-party integrations connected to their sanctioned business critical SaaS apps. The platform ensures continuous compliance by automating the enforcement of least privilege access and revocation of unnecessary access across all of an organization’s API tokens, OAuth third-party apps, and no/low code workflows.
Valence: Illuminating and Securing the Business Application Mesh

Trust is a crucial element of building a successful business. Innovation thrives in collaborative environments, and an organization cannot sustain itself as an island. External vendors, third-party integrations, employee independence and democratization demand a measure of trust to be placed outside of the organization. At the same time, trust makes us vulnerable. It can quickly breed reliance, then complacency and ultimately may affect our business and security postures. Third parties, while beneficial, require access to critical organizational assets and data, and must be managed. The growing dependency on cloud-based solutions and automation led enterprise environments to build an evolving network of application-to-application interconnectivity which is a technological blind spot and creates an emerging risk surface.
Today, we are extremely excited to share that we have raised a $7M seed round from YL Ventures and prominent security professionals to launch Valence, the first Collaborative SaaS Security Remediation platform company.
If the Solarwinds attacks taught us anything, it’s that trust and dependence on third-party vendors without oversight and management can have severe ramifications. It proved to us that we are only as strong as our weakest link, and that existing third-party risk management solutions such as vendor questionnaires, are not as robust as we need them to be. When Shlomi and I began our ideation process for Valence, we wanted to find a way for enterprises to increase business efficiency and innovation, while maintaining trust between organizations, vendors and third parties, without jeopardizing security.
During our conversations with dozens of potential customers and seasoned security professionals, we noticed a recurring narrative. Hyperconnected organizations operate dozens, if not hundreds, of best of breed SaaS and self hosted business applications. Application ownership is distributed in business units and departments across the organization, accelerating innovation and efficiency. However, security teams are scrambling in the dark in their efforts to map out the numerous vendors, connections and data flows between them. While this expansive network provides value and agility previously unattainable for businesses, this interconnectivity is indiscriminate, carried out on an app-by-app and owner-by-owner basis through SaaS marketplaces, direct API connections and complex hyperautomation workflows that results in shadow connectivity, over-provisioned privileges and unmanaged third-party access.
The markers came out, and as we began to sketch our understanding of this web of interconnectivity, we discovered the formation of a new network - a Business Application Mesh - with its own unique risks and rules. The Business Application Mesh is constantly growing and evolving, and with it the blindspots for organizations relying on this web of connections for productivity and automation, without knowledge or transparency as to the risks they are susceptible to. These are uncharted waters for security, and as we dove deeper into understanding it, we realized that by applying zero-trust principals, we can significantly reduce the risk surface for digital enterprises. Valence’s platform shines a light on all of the critical API connections and hyperautomation workflows in the Business Application Mesh, monitoring their usage and defining and enforcing access policies across them. Our platform allows organizations to utilize the significant benefits of the Business Application Mesh without constraints, ensures that their security posture is sound and continuously protects their assets.
Positive market reception of our platform, gained through early customer feedback, compounded these concerns. Cybersecurity experts and potential customers were surprised by the number of third-party connections exposed by our platform for the first time. The actionable risk reduction was immediate. Through these conversations with industry professionals it was clear that the Business Application Mesh can no longer be ignored or mitigated using antiquated risk management solutions. Maintaining the status quo harms enterprise security and jeopardizes stored data. Recent third-party breaches brought third-party risk management front and center in boardrooms, becoming a top concern for security teams and managers alike. Our vision was validated by CISOs’ need for full visibility into application-to-application connectivity, and for a full assessment of the supply chain risk surface. This is how Valence was born.
Valence defines a new category in the cybersecurity landscape. A critical problem space, necessary market education and potential access to the largest network of cybersecurity advisors cemented our decision to partner with YL Ventures, a leading early-stage cybersecurity VC, to fulfill the unique market opportunity we identified. Consistent industry feedback on our solution increased our determination to illuminate the Business Application Mesh and make it safe, accessible and continuously monitored. Our stellar core team at Valence, armed with a phenomenal group of advisors including successful entrepreneurs and CISOs from global enterprises, and with the support of YL Ventures and their large network of cybersecurity heavyweights, is up for this challenge and ready to become the industry standard for securing the Business Application Mesh.
We can’t wait to share our insights with the industry, and invite you to learn more about securing your Business Application Mesh at www.valencesecurity.com.